In a world where cyber threats are becoming more frequent, more sophisticated, and more damaging, traditional perimeter-based security is simply no longer enough. The days when IT teams could build walls around networks and trust everything inside are over. Modern IT ecosystems—full of remote workers, multi-cloud deployments, and personal devices—have rendered the old security models obsolete.
Enter Zero Trust Architecture (ZTA): a transformational approach to cybersecurity based on the principle of “never trust, always verify.” Zero Trust is not just a technical model—it is a fundamental shift in how companies think about security in an interconnected world.
At Fyld, we help organizations rethink their security strategies to stay ahead of evolving threats, ensuring that security isn’t just an IT concern but a business enabler for the future.
What Is Zero Trust Architecture (ZTA)?
Zero Trust Architecture (ZTA) is a modern cybersecurity model based on a fundamental premise: trust nothing, verify everything.
In traditional security models, once a user or device was inside the network perimeter—such as inside a company’s firewall—it was often assumed to be safe. However, today’s environments are much more porous and complex. Employees work remotely, applications are hosted in multi-cloud environments, and personal devices often access sensitive business data. In this context, the old assumption of “inside = safe” no longer holds true.
ZTA breaks away from perimeter-based security by insisting that no user, device, or application—regardless of location—should be trusted automatically. Every access request must be authenticated, authorized, and encrypted before access is granted. And even once granted, access should be constantly reassessed based on real-time behavior and context.
Core Principles of Zero Trust
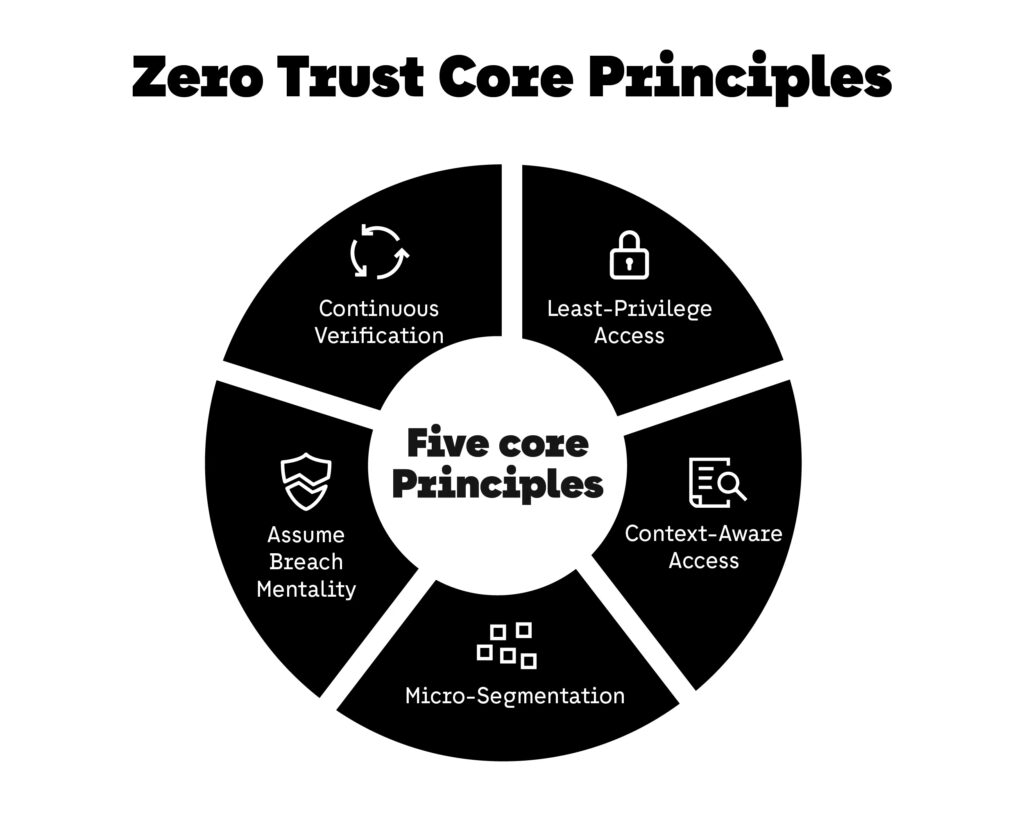
ZTA is not a single product—it’s an architectural philosophy built around several key principles:
- Continuous Verification:
Identity and security postures are verified at every stage, not just during the initial login. - Least-Privilege Access:
Users and devices only get access to the data or systems necessary to perform their tasks—nothing more. - Assume Breach Mentality:
Systems are designed with the expectation that breaches can and will happen. The architecture aims to contain and minimize the impact. - Micro-Segmentation:
Networks are broken into small zones to limit lateral movement. Even if attackers breach one zone, they cannot easily spread. - Context-Aware Access:
Access decisions take into account user roles, device health, location, time of day, and other contextual factors.
How ZTA Differs from Traditional Models
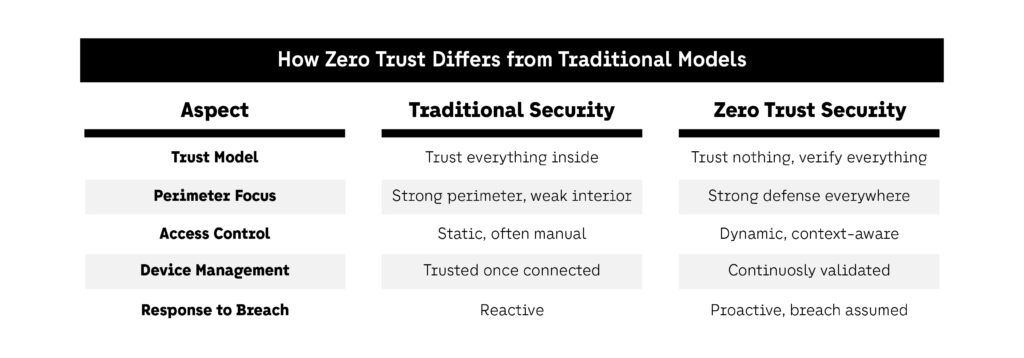
In simple terms:
- Traditional security builds a castle and hopes intruders stay out.
- Zero Trust assumes intruders are already inside—and builds multiple defenses within.
Why ZTA Matters Now More Than Ever
Several macro trends have made ZTA a business necessity, not a technical luxury:
- Remote and Hybrid Work: Employees are working from anywhere, often on personal devices.
- Multi-Cloud Deployments: Businesses are spreading workloads across AWS, Azure, and Google Cloud, with each platform introducing new risks.
- Sophisticated Threats: Modern attackers use lateral movement, privilege escalation, and advanced malware to evade traditional defenses.
- Regulatory Demands: Compliance frameworks like GDPR, HIPAA, and the U.S. Executive Order on Improving the Nation’s Cybersecurity (2021) all encourage or mandate Zero Trust principles.
According to Zero Networks, companies that implement ZTA models reduce their average data breach costs by up to 40%.
Why Traditional Security Models Are Failing
For decades, cybersecurity strategies relied on the idea of a secure perimeter—like walls around a castle. If you were inside the network, you were trusted. Security solutions like firewalls, VPNs, and intrusion detection systems were designed to keep “bad actors” out, while assuming “good actors” were already safely inside.
However, the reality of today’s digital environment has rendered this model obsolete. In 2025 and beyond, the perimeter is an illusion.
Here’s why traditional security models are failing:
1. The Disappearance of the Network Perimeter
The modern IT landscape is no longer confined to on-premises servers protected by a single firewall. Instead, organizations have:
- Employees working remotely from personal networks.
- Applications deployed across multiple cloud providers.
- IoT devices connecting from untrusted locations.
With assets, users, and data scattered globally, there is no longer a clear “inside” and “outside.” Traditional defenses based on perimeter control can’t protect data that exists everywhere.
2. Sophisticated and Targeted Cyber Threats
Attackers have evolved. Modern threat actors use:
- Phishing campaigns to steal credentials.
- Ransomware to paralyze organizations and demand massive payouts.
- Supply chain attacks (e.g., SolarWinds) to infiltrate trusted vendors and partners.
- Advanced Persistent Threats (APTs) to maintain stealthy, long-term access to networks.
These methods often bypass traditional defenses entirely. They don’t attack the walls; they trick the people inside.
In IBM’s 2023 Cost of a Data Breach report, compromised credentials were the most common initial attack vector, leading to breaches that took an average of 277 days to identify and contain.
3. Complexity of IT Ecosystems
Today’s organizations are juggling a patchwork of technologies:
- On-premises servers,
- Cloud-native applications,
- SaaS platforms,
- Third-party integrations,
- Mobile and IoT devices.
Each environment has its own authentication methods, security settings, and monitoring challenges. Traditional security models can’t provide consistent visibility or control across such fragmented ecosystems.
4. Trust Assumptions Are No Longer Valid
Traditional security models implicitly trust anything inside the network:
- A compromised employee laptop can infect internal systems.
- A stolen VPN credential can allow full access without raising alarms.
- An insider threat can move laterally across the network without detection.
ZTA reverses this flawed assumption. Under Zero Trust, no user or device is trusted by default, even if they’re “inside.”
The U.S. National Institute of Standards and Technology (NIST) states clearly in their Zero Trust guidelines that implicit trust is a vulnerability, not a feature.
5. Reactive Security Is Too Slow
Traditional security is often reactive:
- Defend the perimeter,
- Monitor for alerts,
- Respond after detection.
This is simply too slow for today’s threat landscape. Modern cyberattacks are automated, rapid, and capable of exploiting weaknesses within minutes. By the time perimeter defenses trigger an alert, attackers may already have exfiltrated sensitive data.
In contrast, Zero Trust builds a proactive security posture:
- Continuous verification,
- Behavioral monitoring,
- Real-time risk assessment.
Traditional security models were designed for a different era—one of static offices, static users, and predictable threats.
That world no longer exists.
Today’s digital enterprises need security models that assume:
- Users are mobile,
- Data is decentralized,
- Threats are already inside.
Core Components of ZTA
Implementing Zero Trust Architecture (ZTA) is not about installing a single product or flipping a switch—it’s about orchestrating a series of interlocking strategies and technologies that together enforce continuous security.
At its heart, Zero Trust is based on three foundational ideas:
- Never trust any request by default,
- Always verify every user, device, and application,
- Continuously monitor and enforce least-privilege access.
Let’s break down the essential components needed to bring this architecture to life.
1. Identity and Access Management (IAM)
Identity is the new perimeter.
- Every user and device must prove who they are before access is granted.
- Strong Authentication: Use Multi-Factor Authentication (MFA), biometrics, and, increasingly, passwordless methods (such as FIDO2 keys).
- Fine-Grained Authorization: Access decisions should be based on roles (RBAC), attributes (ABAC), or behavior.
According to Okta’s 2025 State of Identity report, 80% of Zero Trust-ready companies prioritize Identity as their first investment.
2. Device Security and Posture Management
This model doesn’t just care who is accessing a resource—it cares what they’re accessing it from.
- Devices must meet security baselines (e.g., encryption enabled, up-to-date OS).
- Non-compliant or risky devices are either denied access or restricted to limited resources.
- Mobile Device Management (MDM) and Endpoint Detection and Response (EDR) tools are key enablers here.
Microsoft’s ZTA Deployment Guide emphasizes device health as a mandatory checkpoint.
3. Micro-Segmentation
Instead of a “flat” network where attackers can move freely once inside, it advocates breaking infrastructure into tightly controlled segments.
- Different departments, applications, and environments are isolated from one another.
- Communication between segments is strictly controlled and monitored.
- Breaches are contained quickly, limiting lateral movement.
Tools like VMware NSX and Cisco ACI offer micro-segmentation capabilities that align with Zero Trust architectures.
4. Continuous Monitoring and Analytics
Access decisions aren’t one-and-done—they’re constantly reevaluated based on changing risk signals.
- Real-time monitoring of user behavior, device health, and network activity.
- Use of SIEM (Security Information and Event Management) platforms like Splunk or Azure Sentinel.
- Behavioral analytics and User and Entity Behavior Analytics (UEBA) to detect anomalies early.
In Zero Trust, the security posture is dynamic, not static.
5. Policy Enforcement Points (PEPs)
Policy Enforcement Points are the gatekeepers of Zero Trust.
- They sit between users, devices, and resources, enforcing dynamic access policies based on real-time context.
- PEPs can be firewalls, identity proxies, secure access brokers (like Zscaler or Netskope), or embedded directly within applications.
The policies they enforce are defined based on principles like least privilege, device trust, and real-time threat scoring.
6. Strong Encryption and Secure Communication
In a Zero Trust world, all communications should be encrypted, whether inside your corporate network or across the public internet.
- End-to-end encryption is enforced for all sessions.
- TLS 1.3 and modern VPN alternatives (like Zero Trust Network Access, or ZTNA) become standard.
The goal is to treat every network as untrusted, no matter where it is.
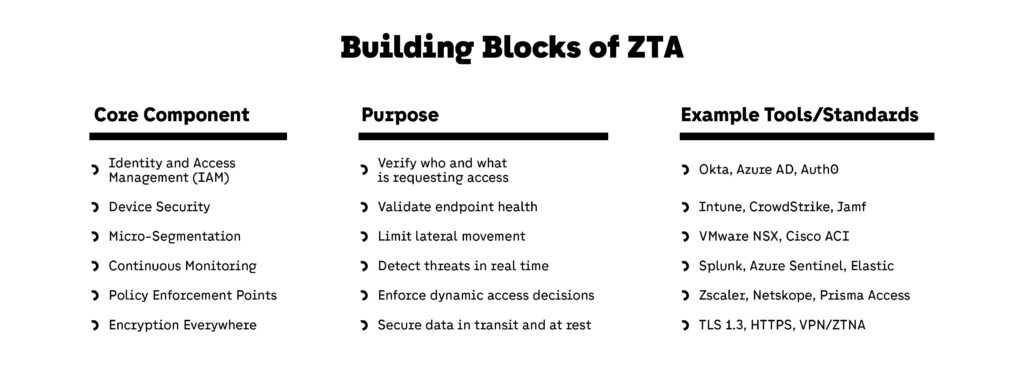
It isn’t about a single solution—it’s about integrating identity, device health, network segmentation, real-time analytics, and policy enforcement into a seamless, dynamic security model.
Benefits of Implementation
While the shift to a ZTA can seem complex, the long-term business and security benefits are profound. Organizations that embrace Zero Trust move beyond reactive, perimeter-based security and establish a proactive, dynamic defense model—one that strengthens resilience, improves visibility, and supports innovation.
Here’s what adopting Zero Trust brings to the table:
1. Drastically Reduced Attack Surface
Zero Trust minimizes the number of entry points available to attackers. By enforcing strict authentication, micro-segmentation, and least-privilege access:
- Unauthorized users are blocked before they can move laterally.
- Even if attackers compromise credentials, their ability to escalate privileges or exfiltrate data is dramatically limited.
According to Forrester Research, companies that implement Zero Trust models can reduce their risk of a major data breach by up to 40%.
2. Better Breach Containment and Incident Response
In a traditional flat network, a single breach can spread quickly across systems. In a ZTA environment:
- Micro-segmentation isolates systems and applications.
- Continuous monitoring detects anomalies early.
- Automated policies can shut down suspicious activity instantly.
This means breaches are not only harder to execute but easier to contain and recover from.
3. Stronger Compliance and Regulatory Alignment
Compliance frameworks such as GDPR, HIPAA, CCPA, and new regional laws increasingly require:
- Data minimization,
- User activity monitoring,
- Risk-based access control.
Zero Trust naturally supports these requirements:
- Enforcing least-privilege and audit logging.
- Providing granular access reports.
- Enhancing data protection at every layer.
As Gartner notes in their Cybersecurity Trends 2025 report, Zero Trust adoption is becoming a de facto expectation for demonstrating compliance readiness.
4. Better Support for Remote and Hybrid Workforces
Today’s workforce expects to work from anywhere, on any device. Traditional VPNs struggle to scale securely, but Zero Trust enables:
- Secure, context-aware access to apps and resources from any location.
- Continuous verification of device security posture, ensuring only healthy endpoints are allowed.
With Zero Trust Network Access (ZTNA), businesses empower flexible work without compromising security.
5. Full Visibility into Users, Devices, and Activity
In traditional security models, users inside the network were often invisible unless a major alert was triggered.
ZTA demands continuous inspection, which leads to:
- Better asset inventory (knowing who and what is connected).
- Real-time behavior monitoring (catching abnormal patterns quickly).
- Proactive threat detection across cloud and on-premises environments.
As organizations move deeper into multi-cloud ecosystems, visibility becomes crucial to avoid blind spots.
6. Enhanced Agility and Innovation
Finally, Zero Trust lays the foundation for secure digital transformation:
- DevOps pipelines can integrate Zero Trust checks into workflows.
- New apps and services can be launched faster without exposing the broader environment.
- IT teams spend less time firefighting breaches and more time enabling business growth.
By focusing on dynamic risk management, companies using Zero Trust free themselves from rigid, perimeter-based infrastructures—and instead build systems designed for continuous change.
It sn’t just about blocking threats—it’s about building a security-first foundation for a flexible, innovative, and resilient enterprise.
Challenges and Considerations When Implementing Zero Trust
While ZTA offers undeniable security benefits, adopting it is not without its hurdles. Organizations need to approach Zero Trust strategically, understanding that it requires more than technology changes—it demands a shift in mindset, processes, and culture.
Here’s a breakdown of the main challenges and what companies need to consider:
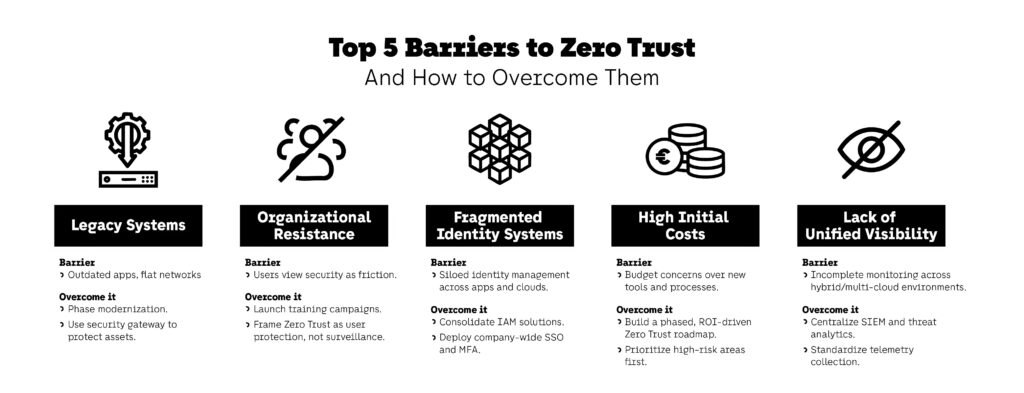
1. Complexity of Integrating with Legacy Systems
Most companies aren’t starting from scratch—they have years or even decades of legacy infrastructure:
- On-premises applications not designed for modern identity protocols (like SAML or OAuth).
- Flat networks with minimal segmentation.
- Devices that lack modern security features.
Challenge:
Retrofitting Zero Trust into legacy environments can be time-consuming, costly, and technically challenging.
Solution:
- Start with a phased rollout.
- Prioritize critical systems.
- Use security gateways or identity brokers to bridge older systems where possible.
According to the Microsoft Zero Trust Deployment Guide, these steps can help facilitate the integration process.
2. Organizational Resistance and Culture Shift
Zero Trust fundamentally changes how users interact with systems:
- No more “one login, full access.”
- Access might be denied if devices are non-compliant.
- Users may encounter more frequent identity checks.
Challenge:
Without clear communication, employees may view Zero Trust as an inconvenience or a sign of distrust.
Solution:
- Educate all stakeholders about why Zero Trust matters.
- Highlight how it protects them personally (e.g., against identity theft).
- Make security enhancements as frictionless as possible (e.g., passwordless authentication).
3. Fragmented Identity and Access Management (IAM)
A solid IAM foundation is the cornerstone of Zero Trust. However:
- Many organizations manage identities across siloed systems (Active Directory, Okta, cloud IAM, etc.).
- Devices, applications, and services might have inconsistent authentication policies.
Challenge:
Fragmented identity makes it difficult to enforce consistent, context-aware access policies.
Solution:
- Consolidate identity providers where possible.
- Invest in Single Sign-On (SSO) and Multi-Factor Authentication (MFA) across all assets.
- Implement centralized identity governance solutions.
Identity maturity assessments, like the ones described by Gartner, are useful starting points:
www.gartner.com/en/documents/identity-governance-architecture-trends-2025
4. Initial Investment in New Tools and Processes
Zero Trust requires:
- Modern IAM systems,
- Endpoint security and device management solutions,
- Network segmentation,
- Continuous monitoring tools (SIEM, UEBA).
Challenge:
There is often a significant upfront cost—not just in purchasing tools, but in integration, training, and ongoing management.
Solution:
- Build a clear business case tied to risk reduction, compliance, and potential breach cost savings.
- Phase investments according to risk exposure and ROI.
- Leverage cloud-native or as-a-service options (e.g., ZTNA solutions) to spread costs.
According to IBM’s 2023 Data Breach Report, organizations with fully deployed Zero Trust frameworks saved an average of $1.76 million compared to those without.
5. Visibility and Monitoring Across Disparate Environments
Zero Trust relies on real-time insights about:
- Who is accessing what,
- From where,
- Under what conditions,
- And whether their behavior is normal.
However, in complex environments—especially multi-cloud or hybrid setups—getting a unified, real-time view is challenging.
Challenge:
Without full visibility, enforcement points can be blind to risky behavior or anomalous access.
Solution:
- Deploy centralized SIEM and monitoring platforms.
- Standardize telemetry collection across endpoints, cloud platforms, and applications.
- Integrate threat detection with incident response automation where possible.
For related challenges in cloud visibility, check:
www.fyld.pt/blog/the-rise-of-multi-cloud-strategies-pros-and-cons-for-businesses-in-2025
Zero Trust is a journey, not a quick fix.
It demands:
- Technical modernization,
- Cultural evolution,
- Executive support,
- And strategic patience.
Real-World Examples of Zero Trust in Action
Zero Trust Architecture (ZTA) is no longer just a concept discussed in cybersecurity circles—it’s being implemented by some of the world’s most influential organizations. These real-world examples show how Zero Trust models can secure diverse environments, support business agility, and defend against today’s most sophisticated cyber threats.
Here are some of the most notable Zero Trust success stories:
1. Google’s BeyondCorp Initiative
Background:
In the early 2010s, Google faced sophisticated attacks (most notably Operation Aurora) that compromised some of its internal networks. Recognizing that perimeter security was no longer enough, Google pioneered the BeyondCorp initiative—one of the first full-scale Zero Trust implementations.
What Google Did:
- Removed trust based on network location (internal or external).
- Moved all applications to a model where every access request required strong authentication, device validation, and contextual risk assessment.
- Employees could work securely from any device, anywhere in the world, without needing a traditional VPN.
Impact:
- Increased flexibility for remote and hybrid workforces.
- Enhanced resilience against insider threats and credential theft.
- Laid the foundation for many modern Zero Trust best practices.
2. U.S. Federal Government Mandate
Background:
Following the SolarWinds supply chain attack and a rise in nation-state cyber threats, the U.S. government issued an Executive Order on Improving the Nation’s Cybersecurity in 2021. This order mandated that all federal agencies adopt Zero Trust principles.
What Agencies Are Doing:
- Implementing strong Identity and Access Management (IAM) frameworks with MFA.
- Enforcing encryption for data at rest and in transit.
- Shifting from network-centric defenses to data-centric security models.
- Requiring continuous monitoring and automated threat detection.
Impact:
- Enhanced resilience of critical infrastructure systems.
- Improved public trust through demonstrable cybersecurity modernization.
- A model that many private sector organizations now follow.
3. Healthcare Providers Embracing Zero Trust
Background:
Healthcare organizations have become prime targets for ransomware attacks due to their sensitive patient data and often outdated IT systems.
Real-World Example:
- A large U.S. hospital system deployed Zero Trust to control access to patient records, applications, and connected medical devices.
- Identity verification and device compliance checks became mandatory before allowing any access to Electronic Health Records (EHRs).
- Micro-segmentation separated critical medical equipment (e.g., MRI machines) from general hospital IT systems.
Impact:
- Limited the blast radius of ransomware attacks.
- Reduced insider threat risks (intentional or accidental).
- Strengthened HIPAA compliance and patient data privacy.
According to Health IT Security, organizations adopting Zero Trust in healthcare reduce the average breach detection time by over 40%.
4. Financial Services: Securing Transactions with Zero Trust
Background:
Financial institutions operate in one of the most heavily regulated and attacked industries. Zero Trust is becoming essential to protect customer data, online banking platforms, and internal systems.
Real-World Example:
- A major European bank adopted Zero Trust policies to secure its multi-cloud environment.
- They implemented real-time behavioral analytics for all users accessing financial platforms.
- API communications between services were encrypted and authenticated continuously.
Impact:
- Improved fraud detection and prevention.
- Accelerated secure rollout of digital banking services.
- Enhanced alignment with PSD2 and GDPR compliance frameworks.
Why These Examples Matter for Your Business
Whether you’re a global enterprise, a healthcare provider, a fintech company, or a public institution, Zero Trust principles can be tailored to meet your unique environment and risk profile.
The key is to move incrementally but decisively, starting with areas of highest risk and building a scalable, resilient security posture.
Zero Trust and the Future of Cybersecurity
As we move deeper into a world defined by remote work, multi-cloud ecosystems, and AI-driven operations, Zero Trust is not just an emerging model—it’s becoming the foundational framework for cybersecurity strategies worldwide. In the future, companies that thrive will be those that treat Zero Trust as a continuous journey, not a one-time project.
Here’s how it’s reshaping the cybersecurity landscape for the next decade:
1. AI-Driven Threat Detection and Response
Artificial Intelligence (AI) is fundamentally changing how security threats are identified and managed:
- Machine learning models analyze millions of user actions and device behaviors in real-time.
- AI can predict abnormal behaviors before traditional rules-based systems even notice a problem.
- Automated responses, like isolating a suspicious device or denying access based on risk scoring, will become standard.
Zero Trust architectures will lean heavily on AI for continuous risk assessment, allowing security policies to dynamically adapt without human intervention.
2. Securing the Multi-Cloud Universe
In a multi-cloud world—where businesses simultaneously use AWS, Azure, GCP, and SaaS providers—consistent security controls are essential.
Zero Trust offers a unifying security approach across cloud providers:
- Identity-centric access control replaces IP-based perimeter rules.
- Micro-segmentation extends across cloud and on-prem environments.
- Centralized monitoring enables threat detection across all platforms.
For organizations pursuing multi-cloud strategies, Zero Trust is the glue that holds cloud security together.
3. Compliance Will Require Proactive Security Models
Future regulations—especially in Europe (e.g., NIS2 Directive) and North America (e.g., updates to HIPAA and CCPA)—are moving toward requiring not just best effort, but demonstrable, proactive cybersecurity controls.
Zero Trust:
- Ensures strict authentication and access policies.
- Improves auditing and reporting through continuous monitoring.
- Demonstrates alignment with “security-by-design” and “privacy-by-design” principles.
As Gartner predicts, by 2026, 70% of boards will demand Zero Trust principles be included in enterprise risk management strategies.
4. Industry-Specific Zero Trust Models Will Emerge
Different sectors have unique risks:
- Healthcare: Protecting patient records and medical devices.
- Finance: Securing transactions, APIs, and personal financial data.
- Manufacturing: Defending connected industrial control systems (ICS).
Zero Trust frameworks will evolve to include industry-specific controls, making adoption faster and more relevant.
For example, the Health Sector Cybersecurity Coordination Center (HC3) has already released guidelines for applying Zero Trust to healthcare networks:
www.hhs.gov/about/agencies/asa/ocio/hc3/index.html
5. Zero Trust for Sustainability and Green IT
Surprisingly, Zero Trust is aligning with sustainability efforts too:
- By enabling remote access securely, companies reduce carbon footprints from commuting and redundant data centers.
- Optimized security architectures use less compute and fewer network resources.
A lighter, more efficient security posture not only saves money—it helps meet ESG (Environmental, Social, and Governance) goals.
In the near future, Zero Trust won’t be a “nice-to-have” — it will be the minimum standard for operating in a digital economy.
Organizations that start early—modernizing their identity frameworks, securing multi-cloud environments, adopting AI-driven monitoring, and embedding security into their business models—will not only protect themselves better, but gain competitive advantages in trust, compliance, and operational resilience.
Key Steps to Begin Your Zero Trust Journey
Adopting a Zero Trust Architecture (ZTA) can feel overwhelming—but it doesn’t have to be.
The most successful organizations treat Zero Trust as a phased, strategic transformation, not a one-time overhaul.
Whether you are starting from a traditional network model or already using cloud-native services, these key steps will help you begin building a Zero Trust foundation with confidence:
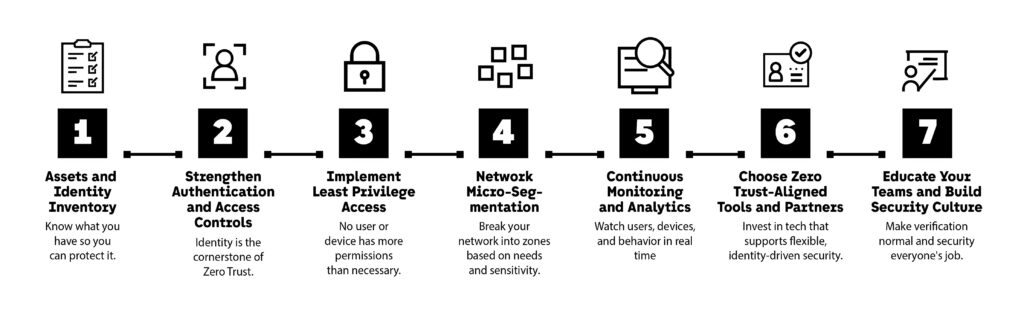
1. Conduct a Comprehensive Asset and Identity Inventory
Before you can protect what matters, you must know what you have.
Start by:
- Mapping users, roles, and permissions across all systems.
- Cataloging devices (managed and unmanaged) accessing your environment.
- Identifying critical applications and sensitive data repositories.
- Assessing current third-party vendor access and integrations.
Why it matters:
Zero Trust requires visibility. You cannot defend assets that are invisible to your security tools.
Tip: Use automated asset discovery tools and identity governance platforms to build a real-time, living inventory.
2. Strengthen Authentication and Access Controls
Identity is the cornerstone of Zero Trust.
Prioritize:
- Deploying Multi-Factor Authentication (MFA) across all users—especially for privileged accounts.
- Moving towards passwordless authentication (e.g., biometrics, security keys like FIDO2).
- Consolidating identity providers (IdPs) wherever possible to centralize policy enforcement.
According to Microsoft’s 2025 Zero Trust Adoption Report, passwordless authentication reduces phishing attack success rates by over 90%.
3. Implement Least-Privilege Access
No user or device should have more permissions than absolutely necessary.
Steps to take:
- Enforce Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC).
- Regularly review and adjust permissions (access reviews).
- Apply Just-In-Time (JIT) access for sensitive systems—granting permissions only when needed and automatically revoking afterward.
Why it matters:
Least-privilege principles dramatically limit the blast radius if an account is compromised.
4. Start Micro-Segmentation of Your Network
Break your network into logical zones based on business needs, user roles, and data sensitivity.
Start by:
- Segmenting critical systems like databases, payment systems, healthcare records, or production servers.
- Restricting lateral movement by enforcing strict access policies between zones.
- Monitoring traffic between segments for unusual behavior.
Tools like VMware NSX and Cisco Secure Workload can support software-defined micro-segmentation deployments.
5. Establish Continuous Monitoring and Analytics
In Zero Trust, security is never static.
You need real-time visibility into:
- User behaviors and deviations from normal patterns.
- Device health and security postures.
- Application access and service-to-service communications.
Deploy:
- SIEM (Security Information and Event Management) systems like Splunk, Elastic, or Azure Sentinel.
- UEBA (User and Entity Behavior Analytics) to spot anomalies that traditional rule-based systems miss.
Tip: Integrate monitoring with automated threat response workflows to cut detection and response times dramatically.
6. Choose Zero Trust-Aligned Tools and Partners
Zero Trust is a strategy, not a single product. However, choosing vendors and partners that align with Zero Trust principles makes your journey smoother.
Look for solutions that offer:
- Context-aware access control (e.g., ZTNA providers like Zscaler, Netskope).
- Centralized policy management across hybrid and multi-cloud environments.
- APIs and integrations that allow flexible enforcement points (identity, device, application, network).
7. Educate Your Teams and Foster a Security-First Culture
Technology alone isn’t enough.
To truly embed Zero Trust, you must:
- Train users on secure behavior expectations.
- Update onboarding and offboarding processes to include tighter access control.
- Foster a mindset where verification is normal and security is everyone’s responsibility.
Change management is a critical success factor.
Without buy-in from technical and business teams alike, Zero Trust initiatives risk stalling.
Practical Tip: Start Small, Then Expand
Many successful organizations begin with pilot programs:
- Protecting a small, high-risk application or user group first.
- Learning lessons about user experience, operational impact, and technology gaps.
- Gradually expanding coverage to include more users, devices, applications, and environments.
Think of Zero Trust like building a city—not a castle.
You start with secure, well-defined neighborhoods, then connect them safely over time.
Embracing Zero Trust: Building Cyber Resilience for the Future
In today’s hyperconnected world, where digital operations are the lifeblood of every business, cyber resilience is no longer optional—it’s mission-critical. Organizations that continue to rely on outdated, perimeter-based security models are leaving themselves dangerously exposed.
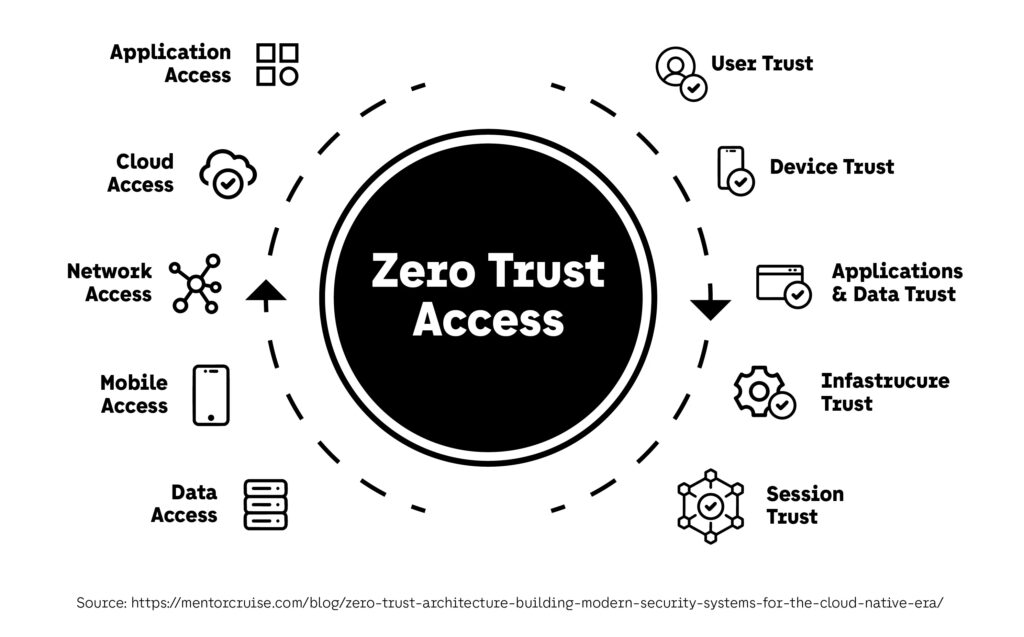
Zero Trust Architecture (ZTA) offers a future-proof blueprint for how businesses must think about cybersecurity going forward:
- Trust nothing automatically,
- Continuously verify everything,
- Limit access rigorously,
- Monitor behavior relentlessly.
But adopting Zero Trust is about more than technology—it’s about embracing a fundamental shift in mindset:
Security isn’t a barrier to business—it’s a business enabler.
Why Zero Trust Is No Longer Just “Nice to Have”
The future landscape will demand that companies:
- Prove strong cybersecurity practices to partners and regulators.
- Protect distributed, hybrid, and multi-cloud environments.
- Adapt quickly to evolving threats without slowing down innovation.
Those who proactively invest today will lead tomorrow—not just in security posture, but in customer trust, regulatory readiness, and market competitiveness.
Zero Trust Is a Journey, Not a Destination
Zero Trust isn’t a box you can check—it’s a continuous evolution that adapts as:
- New threats emerge,
- New regulations come into force,
- New business models develop.
Organizations that succeed with Zero Trust:
- Start small but think big,
- Prioritize visibility and control,
- Continuously measure and refine security practices.
Building cyber resilience means baking Zero Trust into the DNA of your organization.
How Fyld Can Help
At Fyld, we believe that every company—whether a growing startup, a multinational enterprise, or a public institution—deserves a security model that matches the speed, complexity, and ambition of the digital era.
Our cybersecurity experts:
- Assess your current security posture,
- Help you prioritize and roadmap Zero Trust initiatives,
- Support tool selection and integration,
- Train teams to adopt security-first mindsets,
- Continuously monitor and refine security implementations.
With Fyld, Zero Trust becomes not just a framework, but a competitive advantage—fueling innovation, building customer loyalty, and protecting the future you are building.
The threats of tomorrow are already here.
The businesses that will thrive are not those that build taller walls—but those that build smarter, adaptive defenses from the inside out.
Zero Trust isn’t about fear—it’s about empowerment.
And the future belongs to those ready to embrace it, one verified connection at a time.
Discover how Fyld can help you embark on your Zero Trust journey today.


