1. Misconfigured Cloud Storage
Why Storage Misconfigurations Threaten Cloud Security
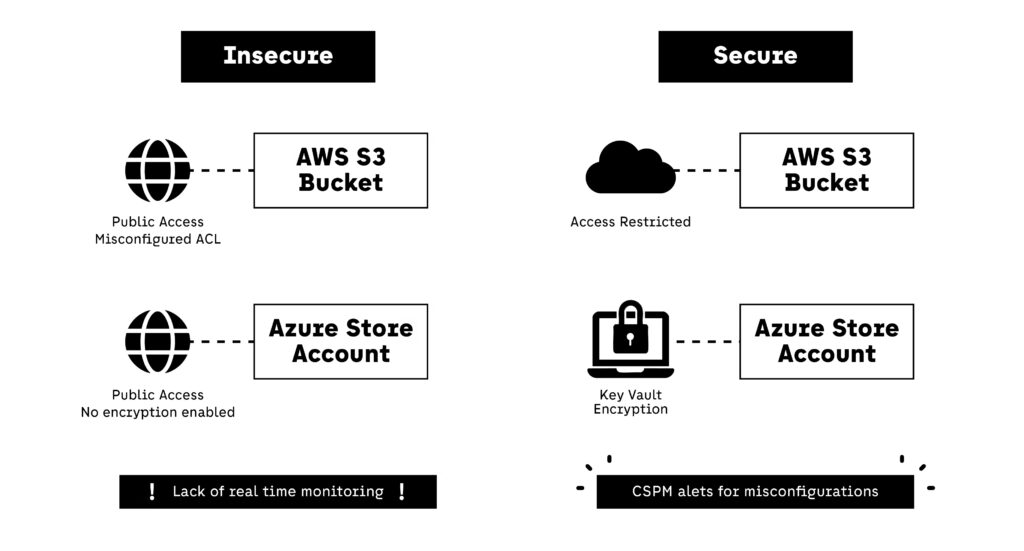
In 2025, misconfigured cloud storage remains one of the most widespread and damaging threats to cloud security. As developers and DevOps teams deploy faster using infrastructure-as-code tools like Terraform, small missteps in storage configuration often go unnoticed — until public access or data leakage becomes a headline. Storage services such as Amazon S3, Azure Blob Storage, and Google Cloud Storage are all vulnerable when defaults are left unchecked.
Storage misconfigurations are dangerous because they can make sensitive data public, expose APIs to unauthenticated users, or bypass encryption protocols silently. Since many teams assume cloud providers “secure by default,” they often overlook access policies, ACLs, and network-layer protections — exposing their cloud security perimeter unintentionally.
Real-World Example: TalentHook Resume Exposure
A major example occurred in 2024 when TalentHook, a resume-building platform, left an Azure Blob container open to the public. The result? Over 26 million resumes — complete with emails, phone numbers, work history, and education — were accessible without authentication. This kind of cloud security failure is not theoretical; it’s recurring and highly exploitable.

Common Misconfigurations That Weaken Cloud Security
Most cloud storage threats originate from simple oversights:
- Public read/write access enabled unintentionally
- No encryption at rest or in transit
- Missing versioning or deletion protection
- Hardcoded access tokens in IaC templates
- Overly permissive IAM roles or ACLs
These create weak points in your cloud security architecture. Attackers often scan for misconfigured buckets using tools like GreyNoise, Shodan, or built-in cloud search queries.
Here’s a real (and dangerous) example of a public AWS S3 bucket policy:
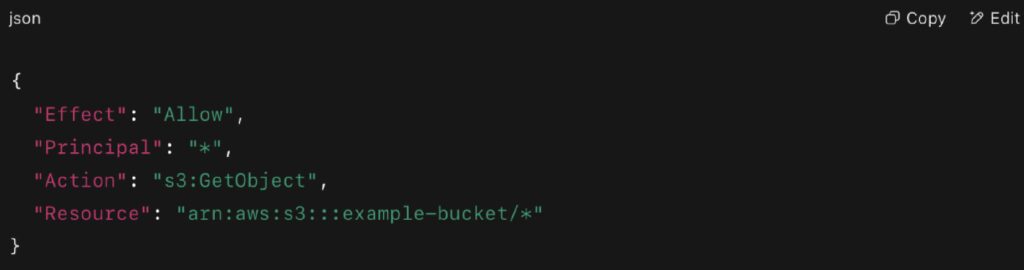
This configuration means anyone can download all objects inside that bucket — a critical cloud security error.
Tools to Detect and Prevent Misconfigured Storage
To mitigate risk, security teams should implement defense-in-depth strategies that monitor and enforce secure storage practices.
Detection and Monitoring Tools:
- AWS Config and Azure Policy for compliance baselines
- GCP Security Command Center for misconfiguration alerts
- CSPM tools like Wiz, Prisma Cloud, and Orca Security for real-time monitoring
- Open-source scanners like ScoutSuite, Prowler, and KICS
Policy Enforcement with Infrastructure as Code:
- Use Checkov, TFLint, or OPA (Open Policy Agent) to validate storage settings before deployment
- Embed automated checks in CI/CD pipelines
- Set default templates to enforce encryption and restrict public access
These approaches align cloud storage configuration with cloud security best practices and compliance standards such as SOC 2, ISO 27001, and GDPR.
Prevention Through Architecture and Automation
Cloud security around storage must extend beyond tools — it should be baked into your architecture.
Best practices include:
- Enforcing private endpoints and VPC-level controls
- Using KMS-managed encryption keys for data-at-rest
- Implementing organization-wide guardrails with SCPs (AWS) or Management Groups (Azure)
- Logging all object access with CloudTrail, Azure Monitor, or GCP Audit Logs
Netflix’s cloud team provides a strong example: they built Lambda functions that trigger on Config Rule violations to automatically remove public access and quarantine buckets. This prevents exposure before manual review, treating cloud security as a proactive pipeline rather than a passive control.
Why Developer Education Still Matters
Even with tooling, the human factor is a consistent weak point. Many misconfigurations stem from misunderstanding platform defaults or misusing IaC modules. Developers should be trained to:
- Avoid wildcard permissions
- Apply the principle of least privilege
- Use secret managers rather than storing credentials in buckets
- Review generated storage policies before pushing to production
Building a shared understanding of cloud security risks among engineers, not just security teams, is essential to closing the storage threat gap.
2. Inadequate Identity and Access Management (IAM)
Why IAM Is the Backbone — and Achilles’ Heel — of Cloud Security
Identity and Access Management (IAM) is one of the most foundational — and most commonly mishandled — elements of cloud security. In modern environments, identities are no longer limited to users. They include service accounts, machine users, CI/CD processes, and third-party integrations. Each identity must be carefully scoped, monitored, and governed, or it becomes a direct pathway for attackers.
When IAM is poorly managed, even strong perimeter controls collapse. Overprivileged roles, dormant credentials, and lack of visibility are all common in 2025 — especially across multi-cloud setups — and these issues severely degrade cloud security posture.
Real-World Breach: Forgotten IAM User Enables Lateral Movement
In 2024, threat actors linked to groups like Nemesis and ShinyHunters targeted AWS environments by scanning for and exploiting long‑unused IAM credentials. One breach involved a global fintech company, where these inactive access keys granted access to services like S3, Lambda, and Secrets Manager. Once inside, the attackers pivoted laterally across multiple accounts and exfiltrated sensitive data—turning forgotten IAM accounts into a critical entry point.
This breach mirrors a broader trend: according to the 2024 Verizon Data Breach Investigations Report, over 40% of cloud-related breaches involved stolen credentials or identity misuse — the majority of which originated from IAM mismanagement.
Common IAM Pitfalls That Undermine Cloud Security
IAM failures come in many forms, including:
- Assigning AdministratorAccess or wildcard permissions (“Action”: “*” and “Resource”: “*”)
- Leaving access keys active for years without rotation
- Persisting unused service accounts with powerful privileges
- Not enforcing MFA for admin or root users
- Hardcoding secrets into Terraform or GitHub repositories
Each misstep increases cloud security risk, and many go undetected until they’re exploited.
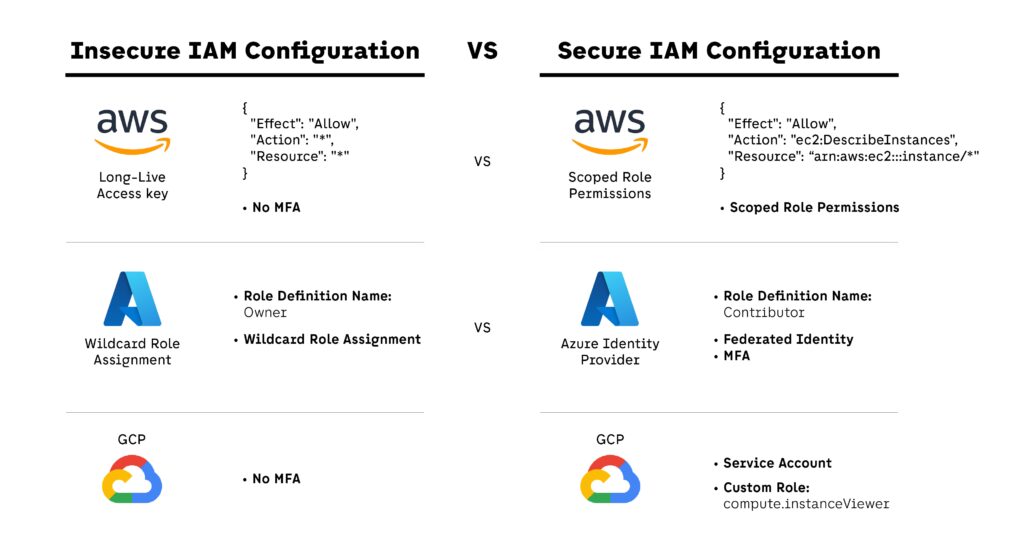
IAM Complexity in Multi-Cloud Environments
IAM structures vary greatly between providers, making standardization difficult:
- AWS: policies, trust relationships, roles, service-linked roles
- Azure: role assignments through Entra ID (formerly Azure AD), scoped to resource groups or subscriptions
- GCP: IAM bindings at project, folder, or organization level
Without unified visibility or policy control, companies often lose track of which identities have access to what — creating unnecessary and unmanaged cloud security exposure.
Practical Strategies to Strengthen IAM Hygiene
Effective cloud security teams approach IAM as a dynamic, auditable system, not a one-time setup. Core techniques include:
Access Monitoring and Visibility
- Enable AWS CloudTrail, Azure AD Sign-In Logs, and GCP Admin Activity Logs for traceability
- Use IAM Access Analyzer (AWS), Azure Entitlement Management, or GCP Policy Analyzer to detect privilege overreach
- Run quarterly access reviews aligned with job function, not account age
Credential Management
- Replace long-lived keys with STS tokens, Azure Access Packages, or Google Workload Identity Federation
- Enforce rotation via Secrets Manager, Vault, or Azure Key Vault
- Auto-disable unused identities with inactivity detection policies
Infrastructure-as-Code Governance
- Enforce least-privilege policies in Terraform using tools like OPA, KICS, and Checkov
- Integrate policy checks into CI/CD (e.g., pre-commit hooks, Sentinel, or Rego logic)
- Audit Git repos for IAM drift and policy escalation
Case Study: Scaling IAM Guardrails with Atlassian Guard
In 2024, Atlassian introduced Atlassian Guard (formerly Atlassian Access + Beacon), a platform designed to centralize identity and access governance across its cloud ecosystem, including Jira, Confluence, and Bitbucket. Guard helps organizations reduce IAM drift, enforce least‑privilege access policies, and detect high‑risk behaviors—all without slowing down developer workflows.
Key capabilities include:
- Automated provisioning and deprovisioning – Guard integrates with identity providers to automatically manage user onboarding and offboarding, reducing over‑privileged accounts and minimizing access sprawl (Atlassian Guard Docs).
- Authentication policy enforcement – Administrators can require SSO and multi‑factor authentication, ensuring only trusted, verified users access sensitive cloud resources (Atlassian Guard Features).
- Audit logging and activity monitoring – Guard tracks changes to permissions, API tokens, and access activity, providing visibility into potential privilege escalations and suspicious behaviors (Atlassian Guard Docs).
- Threat detection and rapid remediation – Advanced threat detection in Guard Premium identifies abnormal activities—like unauthorized API token creation or external access attempts — and enables security teams to respond quickly (Atlassian Guard Blog).
While Atlassian hasn’t publicly disclosed automatic reversion of unauthorized privilege escalations, Guard provides programmable hooks, alerting, and APIs that organizations can leverage to build custom remediation workflows — bringing IAM automation closer to real‑time enforcement.
IAM Governance Requires Cross-Functional Ownership
IAM security is often treated as a backend configuration issue — but in reality, it’s a shared responsibility:
- Security engineers must design reusable roles and boundaries
- Platform teams need automation to detect and fix drift
- Developers should understand the blast radius of the roles they assume
- Leadership should enforce accountability through policy and training
Without coordination, even the best IAM tools fail to deliver true cloud security coverage.
Fyld helps organizations implement scalable IAM and cloud governance strategies tailored to multi-cloud environments.
3. Shadow IT and Unvetted SaaS Tools
The Hidden Layer Undermining Cloud Security
Shadow IT — the use of unapproved tools, services, or platforms by employees — has grown rapidly in the cloud era. In 2025, nearly every team uses some form of SaaS, from AI-powered productivity platforms to niche data collaboration tools. When these services operate outside IT governance and security review, they introduce silent but significant threats to cloud security.
Because modern SaaS platforms often require access to corporate identities, file storage, or messaging systems, they become tightly embedded in daily workflows. And yet, many of these tools are onboarded without security scans, data handling assessments, or logging — making them a blind spot in cloud security strategy.
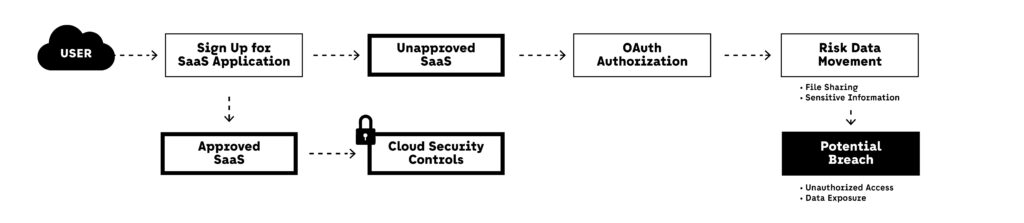
Real-World Breach: Slack Token Leak via Personal App
In 2023, a cybersecurity firm disclosed a case where a team member installed a personal Slack add-on that requested OAuth permissions to access workspace messages. The app stored tokens in plain text on a poorly configured web server. An attacker harvested the token and silently monitored messages, including internal incident discussions.
While not a breach of core infrastructure, it exposed how overlooked integrations — even on trusted platforms — can quietly degrade cloud security. For context, see this Huntress report on OAuth abuse in third-party SaaS.
How Shadow IT Expands the Attack Surface
Common examples of risky Shadow IT include:
- Employees uploading files to personal Google Drive or Dropbox accounts
- Using AI platforms (e.g., ChatGPT or Notion AI) with confidential customer or source code data
- Creating API keys in services like Zapier, Miro, or Trello and sharing them without lifecycle management
- Deploying SaaS tools that request broad OAuth scopes (e.g., read_all, write_all, admin_all)
- Unvetted browser extensions that access webmail, calendars, or credentials
Each of these activities introduces uncontrolled external touchpoints into your cloud security perimeter. They often operate without encryption controls, monitoring, or incident response capabilities.
Why Traditional Controls Don’t Catch Shadow IT
Legacy security controls — such as VPNs or on-premise firewalls — are ineffective in detecting or managing SaaS-based shadow IT. Even CASB (Cloud Access Security Broker) tools, while helpful, often fail to scale effectively without deep integration and customization.
Additionally, most cloud-native tools prioritize infrastructure-level monitoring (e.g., network and compute resources), leaving cloud security blind to application-layer behaviors.
Strategies for Controlling Shadow IT in Cloud Environments
To reduce cloud security risk from Shadow IT, leading organizations implement a layered response that combines detection, policy, and enablement:
1. Visibility
- Use tools like Microsoft Defender for Cloud Apps, Cisco Umbrella, or Netskope to discover unauthorized SaaS
- Monitor DNS, proxy, or firewall logs for patterns linked to new domains or data exfiltration
- Track OAuth authorizations through identity providers like Okta, Entra ID, or Google Workspace
2. Access Governance
- Restrict the ability to self-authorize third-party apps via cloud SSO portals
- Apply conditional access and granular app control policies
- Integrate security questionnaires or vendor reviews into procurement processes
3. Employee Enablement
- Offer pre-approved, vetted alternatives (e.g., company Slack workspace instead of WhatsApp)
- Build internal SaaS catalogs and automate onboarding with pre-defined access scopes
- Educate teams on how casual app usage creates cloud security exposure
Enterprise Example: Google’s Zero Trust SaaS Model
Google’s internal BeyondCorp model now extends to SaaS governance. All third-party integrations must pass Zero Trust checks for identity, device security, and behavioral context. Employees cannot grant OAuth permissions to external apps unless pre-cleared via endpoint and access rules.
This model has been adapted in part by other cloud-native companies as a scalable pattern for reducing cloud security fragmentation across thousands of tools.
Cloud Security Isn’t Just About Infrastructure
Shadow IT highlights that cloud security is not just about servers, storage, and IAM. It’s also about human workflows, collaboration apps, and the way employees interact with digital tools. Without visibility into unapproved integrations, even the most secure cloud environment becomes porous over time.
Organizations must treat SaaS access with the same rigor they apply to cloud VMs, databases, and APIs — especially when data leaves governed environments.
4. Insider Threats in Cloud Environments
Why Insider Threats Are Rising in Cloud Security
While most security strategies focus on external attackers, insider threats remain one of the most complex risks to cloud security in 2025. Insiders — whether malicious, negligent, or compromised — often have legitimate access to sensitive systems and data. In cloud environments where access is abstracted through roles, tokens, and federated identities, detecting abuse from the inside becomes significantly harder.
A key challenge with insider threats is the contextual legitimacy of the user. Actions like downloading files from S3, querying a production database, or spinning up a new compute instance might look routine — unless you understand the intent behind them. This makes cloud security monitoring much more difficult without behavioral baselining and granular visibility.
Real-World Incident: GitHub Secrets Accessed by Insider
In late 2023, a developer at a tech company cloned multiple GitHub repositories that included encrypted environment variables and CI tokens. Although no malicious action occurred, the developer had recently submitted notice of resignation. Because audit logging on repository access wasn’t enabled and the secrets manager lacked per-user tracking, the organization couldn’t confirm whether sensitive data had been exfiltrated — a textbook cloud security gray zone.
For an overview of real insider threat patterns, see the 2024 Verizon Insider Threat Report.
Types of Insider Threats in Cloud Contexts
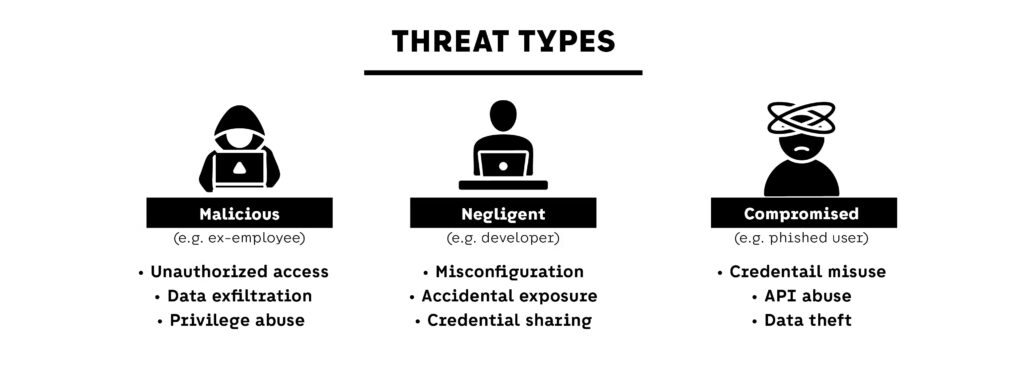
Insider threats to cloud security typically fall into three categories:
- Malicious insiders: individuals who abuse their access deliberately, often after termination or during a conflict
- Negligent insiders: employees who accidentally expose data or misconfigure resources
- Compromised insiders: users whose credentials or sessions are hijacked by attackers
Each of these can operate within the boundaries of legitimate permissions, which makes traditional rule-based detection ineffective in most cloud security architectures.
Why Cloud Environments Amplify Insider Risk
Cloud platforms like AWS, Azure, and GCP are highly abstracted — using roles, policies, tokens, and federated identities. This creates indirect access paths where a single user or service can impact hundreds of resources without being explicitly aware of it.
Examples include:
- A user with Terraform access can apply destructive changes to production
- A developer with access to container registries may overwrite critical workloads
- A support agent with excessive IAM permissions might access sensitive customer data
- An over-permissive Lambda function triggered by an insider can delete logs or snapshots
These are not hypothetical — they’re common blind spots in many cloud security programs.
Monitoring and Mitigation: From Trust to Telemetry
Preventing insider threats requires a layered approach that goes beyond just limiting access. Key strategies include:
1. Behavioral Monitoring
- Use tools like AWS GuardDuty, Microsoft Defender for Cloud, or GCP Security Command Center to baseline activity
- Leverage UEBA (User and Entity Behavior Analytics) to detect unusual access patterns
- Integrate SIEM tools (e.g., Splunk, Sentinel, Chronicle) with cloud-native logs for context
2. Granular Audit Trails
- Enable detailed logging for storage access, database queries, and function triggers
- Use CloudTrail Lake, Azure Monitor Logs, or GCP Cloud Audit Logs to retain history and correlate actions across services
- Tag access requests by user, not just system identity, for traceability
3. Access and Role Hygiene
- Apply Just-In-Time (JIT) access with automated revocation
- Use break-glass accounts with approval workflows
- Disable roles immediately after employee offboarding
Example: JIT Access at Capital One
Many leading organizations have adopted automated Just-In-Time (JIT) access systems for cloud environments. For instance, developers must request access to production actions through automated workflows (often via Slack or portal), and access is granted only for a short, predefined time window — typically under 30 minutes. Every access event is logged, reviewed, and automatically revoked. This approach reduces standing permissions and significantly strengthens cloud security posture.
For detailed workflows and industry validation, see resources such as Cloud Security Alliance on Just‑In‑Time access workflows or the Tenable blog on why JIT access is essential for cloud security.
Insider Threats Are a Human and Cloud Problem
Cloud security is not only a matter of encryption, IAM, and firewalls — it’s about user behavior, intent, and accountability. The same tools that enable flexibility and speed in the cloud can be misused internally if guardrails are missing.
Organizations must foster a zero-trust mindset that assumes no identity is safe — not even internal ones. Combine this with user education, strong policy enforcement, and behavioral monitoring to close insider-driven cloud security gaps before they lead to impact.
5. Insecure APIs and Interfaces
APIs: The Front Door to Your Cloud — and an Attack Surface
In modern architectures, APIs are the backbone of service interaction. They handle authentication, data transfer, orchestration, and integrations between internal systems, third-party services, and end-user interfaces. As cloud-native applications scale, so does API complexity — and with it, risk. In 2025, insecure APIs are among the fastest-growing threats to cloud security.
APIs often expose sensitive functions: database queries, billing operations, user provisioning, and more. When these interfaces are improperly secured — or when deprecated versions remain active — attackers gain direct access to business logic and underlying infrastructure, bypassing perimeter protections entirely.
Real-World Breach: API Vulnerability at T-Mobile
In 2023, T-Mobile confirmed an incident where attackers exploited an API without proper rate limiting or authorization checks, gaining access to over 37 million customer records. The API was never meant to be exposed externally — but it was. This breach highlighted how broken access control at the API layer can undermine even mature cloud security programs. TechCrunch covered the breach in detail here.
What Makes APIs So Vulnerable in the Cloud?
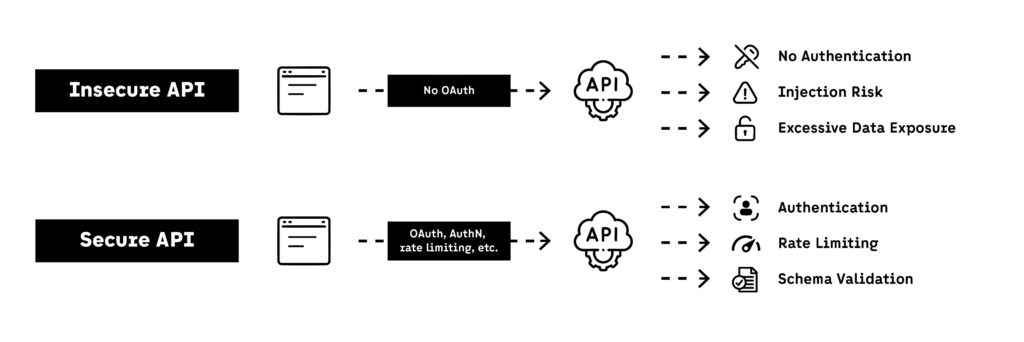
Cloud-native APIs often evolve rapidly. New endpoints get added, schemas change, and teams ship fast — but security reviews don’t always keep pace. Common API weaknesses that erode cloud security include:
- Lack of authentication or token validation
- Broken access control (e.g., vertical/horizontal privilege escalation)
- Unrestricted input (leading to injection or denial of service)
- Excessive data exposure in responses (e.g., sensitive IDs, tokens, logs)
- Lack of logging or monitoring
These risks are amplified by automation: APIs drive IaC pipelines, CI/CD tooling, and DevOps workflows. One insecure webhook or endpoint can become an invisible backdoor into production systems — a silent but critical cloud security liability.
Tools and Strategies to Secure Cloud APIs
The most effective cloud security programs treat APIs like first-class assets — not just backend utilities. This means integrating security from design to deployment.
1. Authentication and Authorization
- Use OAuth 2.0, OIDC, or JWTs with scoped permissions
- Implement API gateways (e.g., AWS API Gateway, Azure API Management, GCP Apigee) with throttling, validation, and routing
- Enforce zero trust API access by evaluating identity, context, and behavior
2. Testing and Observability
- Use OWASP API Security Top 10 as a reference baseline
- Run dynamic tests with tools like Postman, Burp Suite, or APIsec
- Monitor traffic and anomalies with Datadog, AWS CloudWatch, or Azure Monitor
3. Design and Deployment Governance
- Tag and version all APIs
- Disable unused endpoints and apply rate limiting
- Include API schema validation in CI pipelines
- Use WAFs and runtime protection (e.g., from Imperva, Cloudflare) to defend high-risk endpoints
Enterprise Example: Shopify’s Secure API Lifecycle
Shopify implements automated reviews for every internal and external API. All endpoints are tested against OWASP API top 10 threats before release. They use GraphQL access control, context-aware rate limits, and real-time telemetry to track usage patterns. This has helped them minimize cloud security risks despite a rapidly evolving product architecture.
API Sprawl = Shadow Infrastructure
In large organizations, untracked APIs become a kind of shadow infrastructure. Engineering teams may spin up internal services with undocumented or unauthenticated endpoints. These don’t show up in traditional asset inventories — but they still interact with production systems.
Cloud security teams must treat API discovery and control as core responsibilities, just like they do with VMs, containers, and IAM roles.
6. Lack of Cloud Incident Response Planning
Why Traditional IR Fails in the Cloud
Most incident response (IR) plans are built around legacy IT models — static networks, monolithic apps, and on-premises systems. But in 2025, cloud-native architectures dominate: distributed, ephemeral, API-driven, and automated. Without IR plans specifically designed for this model, even experienced security teams can be caught flat-footed during a breach.
According to the 2024 SANS Detection & Response Survey, only 21% of organizations rated their cloud-native detection and response capabilities as extremely effective — highlighting a widespread gap in preparedness.
In a cloud security context, where events move at the speed of automation, traditional IR is simply too slow.
Real Failure: Serverless Breach Through GitHub Secrets
In a 2023 incident, attackers exploited an exposed AWS access key accidentally committed to GitHub. It granted permissions to invoke a Lambda function connected to internal APIs and a DynamoDB table. The attacker used the function to exfiltrate customer data — all while staying within the role’s allowed actions.
Because the team had no cloud-specific IR automation or detection thresholds, the breach went unnoticed for nearly two weeks. There was no alerting, no function isolation workflow, and no cross-account monitoring — a breakdown in basic cloud security hygiene and response planning.

Key Gaps That Undermine Cloud Incident Response
When teams fail to update their IR plans for the cloud, the following breakdowns are common:
- No defined playbooks for cloud services (e.g., S3, GCS, VMs, IAM, container platforms)
- Logs scattered across regions, services, and cloud providers
- No automation to isolate or tag compromised assets
- No pre-staged credential rotation or access revocation process
- Limited communication plans across multi-cloud environments
- Lack of experience running cloud-specific tabletop exercises
- Long delays in confirming the scope of data exposure
Each delay increases the dwell time of the attacker — directly increasing the impact on cloud security.
What a Cloud-Specific IR Plan Needs to Include
1. Platform-Aware Playbooks
Each cloud provider — AWS, Azure, and GCP — requires its own set of IR guides. These should cover:
- Storage misconfigurations (e.g., public S3 or Blob containers)
- IAM abuse or privilege escalation
- API key leakage
- Suspicious compute actions (e.g., cryptomining, root escalation, lateral movement)
- Service account misuse and token replay
2. Real-Time Containment Automation
Leverage serverless and API-based containment:
- Auto-tag and quarantine EC2/GCE instances
- Invoke a Lambda or Azure Function to revoke IAM roles
- Trigger secret rotation in Secrets Manager or Key Vault
- Pause CI/CD pipelines if unauthorized role changes are detected
- Alert DevSecOps via Slack/PagerDuty/Ticket queues immediately
Use SOAR tools like Tines, Cortex XSOAR, or Microsoft Sentinel to link detection to action.
3. Unified Telemetry and Forensics
Aggregate logs from all environments into a single SIEM or data lake:
- AWS CloudTrail + GuardDuty + CloudWatch Logs
- Azure Monitor Logs + Activity Logs + Defender for Cloud
- GCP Cloud Audit Logs + Event Threat Detection
Feed these into tools like Chronicle, Panther, Splunk, or Sentinel for normalized incident investigation. This is core to scalable cloud security response.
Tested Example: CSA’s Cross-Cloud Incident Response Framework
The Cloud Security Alliance’s Cloud Incident Response Framework outlines how to build effective, cloud-native IR programs across AWS, Azure, and GCP. It emphasizes:
- Provider-specific playbooks for cloud-native threat categories
- Automation of detection and containment using serverless and API hooks
- Centralized telemetry for complete forensic visibility
Used globally by security teams, the framework is a tested reference for reducing response times and validating cloud-specific security controls under stress.
Testing Is the Missing Layer
Even if you write a perfect IR plan, it’s useless unless tested. Top-tier cloud security teams tie simulations into regular workflows. They test scenarios like:
- Misconfigured storage exposed in a non-production region
- Credential leaked and replayed via GitHub
- Privilege escalation from overly broad IAM policies
- Unauthorized API-induced database deletion
Microsoft underscores this through ongoing Red Team/Blue Team attack simulations, live-site penetration exercises, and automated attack-emulation tools that constantly validate detection and response capabilities across Azure and Microsoft 365 workloads. You’ll find practical templates and scenarios in Microsoft’s attack simulation documentation here: Microsoft attack simulation testing for cloud workloads.
And for a broader perspective on security testing as a foundational control, check Microsoft’s Azure Well-Architected Framework: Security Testing recommendations
People and Process Matter More Than Tools
Technology can trigger actions — but human judgment and team alignment drive outcomes. A complete IR plan must define:
- Roles and owners per platform
- Communication escalation trees
- Customer and legal disclosure thresholds
- Critical service RTOs (Recovery Time Objectives)
Cloud security is not just about detecting threats — it’s about stopping them quickly, publicly, and recoverably.
7. Compliance Gaps Across Multi-Cloud Systems
Why Multi-Cloud Makes Compliance Riskier
By 2025, most enterprises run critical workloads across AWS, Azure, and GCP. Microsoft’s 2024 State of Multicloud Security Report confirms that many organizations manage multiple cloud providers, yet still face major fragmentation and compliance blind spots.
As each provider uses its own controls—encryption defaults, access management, log retention policies—control drift becomes inevitable. Without unified enforcement, inconsistencies across environments weaken cloud security posture and increase the likelihood of audit failures.
Real-World Example: PCI Failures in a Multi-Cloud Retail Stack
In 2024, a global retail company failed its PCI-DSS audit due to disconnected controls across AWS and Azure:
- AWS RDS databases had encryption disabled in a staging environment
- Azure Blob logs were silently overwritten due to incorrect lifecycle rules
- Customer PII flowed between platforms with no cross-cloud tracking
This breakdown mirrors trends reported in the Cloud Security Alliance Cloud Compliance Risk Report.
The Most Common Compliance Breakdowns in Multi-Cloud
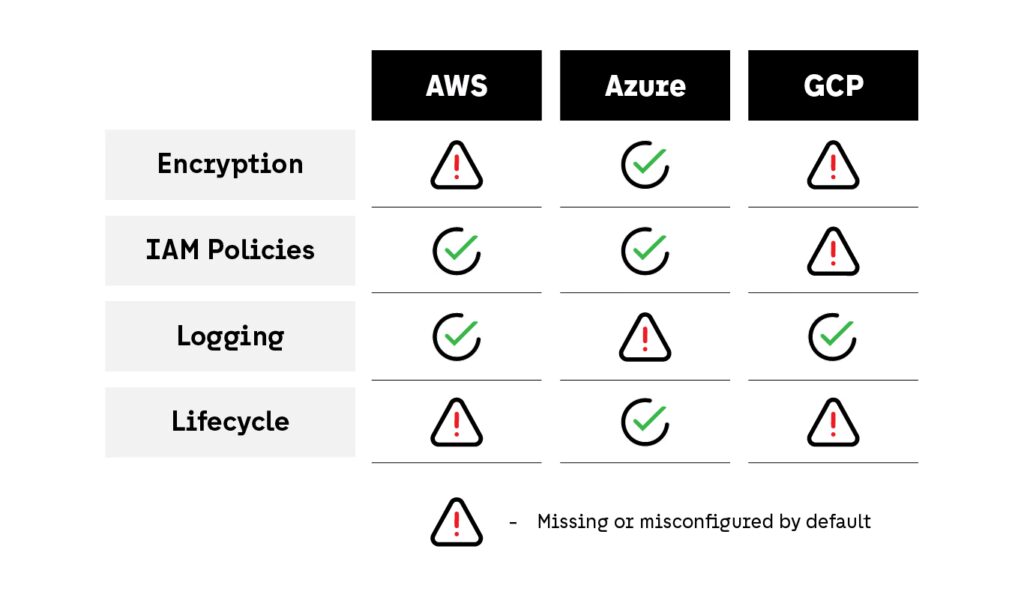
- IAM misalignment: Varying roles, permissions, and policies across platforms
- Logging inconsistencies: Retention periods and audit log destinations differ
- Encryption coverage gaps: One cloud may enforce server-side encryption by default, while another requires explicit configuration
- No unified evidence collection: Reports and audit artifacts live in isolated systems
- Drift in tag standards, retention policies, and access reviews
These issues aren’t just audit flags — they weaken real cloud security by leaving blind spots open to attackers or insider misuse.
How to Unify Compliance and Improve Cloud Security
1. Enforce policy as code across clouds
Use tools like:
- Open Policy Agent (OPA)
- Sentinel (by HashiCorp)
- Conftest
- Terraform with policy modules for each cloud
2. Centralize audit and attestation evidence
Use GRC platforms like:
Pair with SIEMs or data lakes for full cloud log visibility:
3. Assign clear cross-cloud ownership
Designate compliance engineers or platform security leads to manage:
- Encryption enforcement
- Identity policy baselines
- Logging coverage validation
- Regulatory mappings (GDPR, HIPAA, ISO 27001)
Case Study: HSBC’s Continuous Compliance Framework for Multi‑Cloud
In 2024, HSBC was showcased in a case study highlighting its implementation of a multi‑cloud continuous compliance engineering framework, leveraging both AWS and Azure platforms. To codify policies-as-code, HSBC deployed tools such as Terraform and Open Policy Agent (OPA), embedding rule sets defined in high‑level configuration languages. The framework includes automated enforcement of hundreds of controls, centralized monitoring, and ongoing validation to meet regulatory requirements such as GDPR, PCI‑DSS, and UK banking standards.
While the original CIO Applications Europe link is no longer active, HSBC’s deployment is described in Airwalk Reply’s Continuous Compliance Framework case study. Technical approaches involving OPA + Terraform as a mechanism for policy enforcement in multi-cloud IaC pipelines are further detailed in guides like those from InfraLovers and Pluralsight.
Compliance Isn’t Just an Audit Concern — It’s a Cloud Security Pillar
If encryption policies, IAM configurations, and audit trails can’t be enforced across platforms, they can’t be trusted. Regulatory failure becomes a symptom of deeper cloud security misalignment — not just a documentation issue.
Organizations that treat compliance as code and embed it into CI/CD and drift detection systems gain a clear advantage: real-time policy validation and faster audit readiness.
Turning Cloud Security Awareness into Action
The rapid evolution of cloud platforms has reshaped the threat landscape. From identity mismanagement and insecure APIs to insider threats and compliance drift across multi-cloud environments, every layer of modern infrastructure is now a critical security frontier.
What emerges across these risks is a consistent theme: many organizations still treat the cloud as static infrastructure rather than what it truly is—dynamic, distributed, and visible to attackers. Misconfigurations, poor visibility, and reactive incident planning turn normal operations into potential entry points for exploitation.
Microsoft’s Cloud Security Benchmark (CSB v1), released in April 2025, provides a prescriptive framework to address these gaps. It outlines best practices for securing cloud workloads across identity, data, APIs, networks, and incident response, mapped to standards like CIS, NIST, and PCI‑DSS. Key recommendations include:
- Shifting IAM from permission sprawl to least privilege through centralized identity management, strong authentication, and managed identities.
- Treating APIs as frontline attack surfaces, implementing runtime protections like Microsoft Defender for APIs to mitigate OWASP Top 10 threats.
- Embedding continuous compliance by leveraging Microsoft Defender for Cloud’s posture management dashboard, which continuously monitors and remediates risks across multi‑cloud environments.
- Fortifying infrastructure and networks with web application firewalls, DDoS protection, segmentation, and centralized network rule management.
The path to effective cloud security in 2025 isn’t about acquiring more tools—it’s about integrating security into architecture, workflows, developer behavior, and governance. Start by auditing one of your most active environments against the Cloud Security Benchmark. Don’t aim for perfection—aim for clarity: identify gaps, assign ownership, and establish how quickly risks can be detected and addressed.
At Fyld, we help organizations put these principles into practice — turning cloud security benchmarks into actionable strategies. Whether it’s IAM guardrails, API protection, or continuous compliance automation, our team ensures security isn’t just an add‑on, but an integral part of how your cloud operates.
Cloud security maturity doesn’t come from reacting to threats. It comes from building systems that expect them.


