In 2025, software delivery speed has become a competitive advantage—but so has resilience. Agile teams are under constant pressure to release faster while facing new security risks in cloud-native architectures, AI-driven pipelines, and distributed infrastructure. The need to integrate protection early and continuously is no longer optional. This is where DevSecOps—the practice of embedding security across every stage of development and operations—plays a decisive role.
Over the past few years, organizations that once treated security as a post-deployment step have shifted toward proactive, integrated models. According to the 2025 State of DevSecOps report by Datadog, teams adopting this approach reduced critical vulnerabilities in production by more than 30% without slowing delivery. It’s a clear sign that embedding security checks within continuous integration and delivery workflows has evolved from a best practice into a business imperative.
For agile teams, the challenge lies in balancing speed and security without adding complexity or friction. Traditional security reviews and manual approvals often break sprint cadence, while modern frameworks enable automation, shared accountability, and continuous verification. This new way of working helps developers, security engineers, and operations teams collaborate seamlessly while maintaining velocity. It’s not just about tools—it’s a cultural and procedural shift aligned with the agile manifesto’s core principles.
Top 5 DevSecOps Best Practices for Agile Teams in 2025 Checklist
- Integrate automated security testing in every CI/CD stage.
- Shift security left with code analysis and dependency scanning.
- Secure infrastructure as code with policy enforcement.
- Implement software supply chain security and SBOM validation.
- Foster a DevSecOps culture where developers own part of the security process.
What Is DevSecOps — Definition, Evolution, and Why It Matters
DevSecOps is the natural evolution of DevOps, designed to integrate security seamlessly into software delivery pipelines. Instead of treating security as an external checkpoint, DSO ensures that every stage of development—from code commit to deployment—includes automated security validation and compliance enforcement. It’s not an additional layer; it’s an architectural principle that defines how modern teams build software safely at scale.
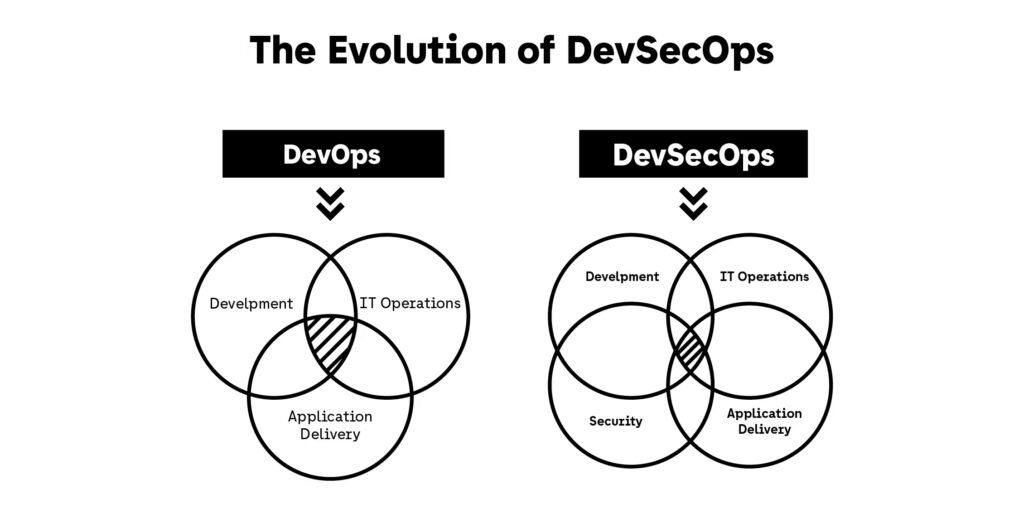
The rise of DevSecOps mirrors the growing complexity of cloud-native systems. Over the past few years, microservices, container orchestration, and infrastructure as code have transformed how teams ship products. Traditional security models, built around manual reviews and post-release testing, simply couldn’t keep up. This gap led to security incidents caused by overlooked dependencies, misconfigured permissions, and unverified third-party packages. DSO emerged as the answer: a continuous, integrated approach where prevention is part of the workflow, not an afterthought.
By 2025, DSO has matured into a measurable discipline. The Datadog 2025 State of DevSecOps report shows that teams adopting full pipeline integration reduced average time to remediate vulnerabilities by 35%. Similarly, the GitLab Global DevSecOps Survey 2025 (www.about.gitlab.com) highlights that over half of respondents now automate security scanning during merge requests, reducing production-stage risks dramatically. These findings confirm that DevSecOps isn’t theoretical—it’s operational reality for high-performing engineering teams.
DevSecOps also represents a cultural realignment. In agile organizations, developers, security engineers, and operations specialists share ownership of code safety. Security tasks become part of sprint planning and continuous improvement cycles, supported by automated tooling and clear visibility. Instead of slowing delivery, this integration increases reliability and reduces friction between teams. Google Cloud’s 2024 Accelerate State of DevOps report emphasizes that cultural maturity—collaboration, automation, and observability—is what differentiates successful DevSecOps teams from those merely running tools.
Ultimately, DSO matters because it makes security continuous, measurable, and adaptive. In an era of AI-generated code, distributed environments, and real-time delivery expectations, static defenses are no longer enough. Embedding security into every iteration enables agile teams to release faster with confidence, maintain compliance by design, and respond swiftly to evolving threats—all without sacrificing velocity or innovation.
Core DevSecOps Practices for Agile Teams
Implementing DevSecOps effectively requires more than adding scanners to pipelines. Agile teams need a cohesive framework that aligns automation, testing, and collaboration. The following five practices form the foundation of modern DevSecOps, enabling continuous delivery without sacrificing security or speed.
1. Shift-Left Security
Shift-left security is the cornerstone of a mature DSO strategy. It refers to integrating security testing and validation earlier in the software delivery lifecycle, moving it “left” on the development timeline. Instead of waiting for penetration tests or compliance reviews at the end, DevSecOps teams embed automated security analysis at every code commit, build, and merge stage. This early integration aligns perfectly with agile principles—catching issues when they are easiest and least expensive to fix.
In a modern DevSecOps pipeline, shift-left practices typically include Static Application Security Testing (SAST), Software Composition Analysis (SCA), and secret scanning tools that run automatically in CI/CD systems. Developers receive feedback within seconds, allowing them to address vulnerabilities before code reaches production. For example, GitHub’s Advanced Security integrates directly into pull requests, alerting contributors to unsafe dependencies or insecure API calls. Similarly, Snyk’s 2025 State of Open Source Security report (www.snyk.io) found that organizations using shift-left security reduced mean remediation time by 42% compared to teams relying on post-deployment fixes.
The benefits of shift-left security within DevSecOps go beyond faster detection. Early validation helps developers internalize secure coding practices. When vulnerabilities are identified at commit time, engineers learn patterns of safe implementation, improving overall code quality. A 2024 study from the Open Source Security Foundation showed that consistent developer feedback loops decreased recurring vulnerabilities by 30% across large agile projects. This aligns with the DevSecOps principle that security must become part of development culture, not an isolated task managed by security teams.
However, implementing shift-left practices requires balance. Overly aggressive or noisy scans can cause alert fatigue and resistance among developers. Mature DevSecOps pipelines address this through context-aware testing, prioritizing findings based on exploitability and impact. Datadog’s Application Security Monitoring exemplifies this approach by correlating vulnerabilities with runtime telemetry, ensuring that developers focus on the most critical risks. This adaptive scanning keeps pipelines fast while maintaining robust coverage.
In 2025, shift-left security represents a fundamental mindset shift within DSO. It enables agile teams to merge velocity and vigilance—catching issues early, improving code health, and fostering shared accountability for security outcomes. By integrating these practices, organizations build resilient pipelines where quality and protection evolve together with every iteration.
2. Continuous Integration and Testing in CI/CD
Continuous integration and continuous delivery pipelines form the backbone of modern DevSecOps implementations. In agile environments where new code is merged several times a day, manual security reviews are too slow and inconsistent. DevSecOps introduces automation directly into these pipelines so that every commit, build, and deployment is subject to continuous validation. This integration transforms security from a one-time gate into an ongoing feedback loop that improves with every iteration.
In a mature DevSecOps pipeline, automated security testing occurs alongside functional and performance testing. Tools such as GitLab Ultimate, CircleCI’s security extensions, and Azure DevOps Security Scans embed scanning stages that evaluate source code, container images, and infrastructure templates in real time. By combining Static Application Security Testing (SAST), Dependency Scanning, and Dynamic Application Security Testing (DAST), DevSecOps teams gain full lifecycle visibility from development to production. This continuous testing ensures that even the smallest code changes adhere to the organization’s security standards.
A 2024 GitLab DevSecOps Survey found that teams embedding automated security scans within CI/CD pipelines detected 60% more critical issues before deployment compared to teams performing ad hoc checks. Similarly, Google Cloud’s 2024 Accelerate State of DevOps report (www.cloud.google.com) highlighted that integrating security into build stages shortened vulnerability remediation time by nearly half. These outcomes demonstrate the measurable efficiency gained when DevSecOps automation replaces fragmented manual assessments.
The technical design of continuous security testing often includes multiple layers of control. Pipeline stages trigger security scans on commits, merge requests, and container builds. When vulnerabilities are detected, the pipeline can automatically fail or flag the build for review, depending on severity. This consistent process enforces compliance while allowing flexibility. DevSecOps teams frequently use tools like OWASP ZAP, Trivy, or Checkov to ensure that runtime images and IaC templates meet both organizational and regulatory benchmarks.
Beyond automation, continuous testing within DSO promotes collaboration. Developers gain immediate, actionable feedback, while security specialists focus on analyzing trends instead of chasing individual alerts. This shared responsibility model aligns perfectly with agile values—ensuring speed without risk. In 2025, organizations using continuous integration and testing as part of their DevSecOps maturity model are leading the way in balancing rapid delivery with security assurance, proving that automation and trust can coexist within every sprint.
3. Runtime and Dynamic Security
Runtime and dynamic security represent the second layer of protection in a mature DevSecOps model. While shift-left security focuses on early detection, runtime security ensures continuous monitoring and response once software is deployed. In modern agile environments, applications are distributed across containers, serverless functions, and hybrid clouds—environments that evolve rapidly. DSO addresses this challenge by embedding tools that monitor behavior, detect anomalies, and respond automatically when threats appear.
At the core of runtime security is the principle of observability. DevSecOps teams leverage Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Runtime Application Self-Protection (RASP) to identify vulnerabilities in live environments. These tools go beyond static scanning by simulating real-world attacks and monitoring application behavior in production. For example, Datadog’s Application Security Monitoring correlates runtime telemetry with known vulnerabilities, allowing teams to prioritize high-impact issues. Similarly, Palo Alto Networks’ Prisma Cloud provides continuous visibility across containerized workloads, ensuring that runtime defenses adapt as infrastructure scales.
The advantage of runtime security in a DevSecOps workflow lies in its real-time responsiveness. By integrating continuous monitoring, teams can detect anomalies such as privilege escalations, malicious API calls, or unexpected process executions as they occur. In 2025, many organizations use AI-enhanced detection models to strengthen this layer of DevSecOps. SentinelOne’s 2025 security report notes that machine learning models trained on runtime data now predict and block potential exploits before execution, reducing mean time to detection by over 45%.
Effective runtime security is not limited to technology—it’s a process integrated into the DevSecOps lifecycle. Alerts generated during production feed back into development pipelines, helping teams refine code and configurations for future releases. This closed-loop feedback system transforms runtime insights into proactive improvement. According to GitLab’s 2024 Global DevSecOps Report, 57% of organizations that combined runtime monitoring with continuous integration pipelines saw faster remediation and stronger compliance alignment. This reinforces the DevSecOps goal of merging security and development through shared visibility and accountability.
In essence, runtime and dynamic security close the loop on the DSO cycle. They allow agile teams to maintain protection after deployment, ensuring that each new release inherits knowledge from previous threats. With adaptive monitoring, automated response, and feedback integration, DevSecOps evolves from a preventive framework into a living, self-improving security ecosystem.
4. Infrastructure as Code and Policy Automation
Infrastructure as Code (IaC) has become a backbone of modern delivery, enabling teams to define infrastructure using version-controlled templates. In DevSecOps, security must follow suit: rather than retrofitting protection after provisioning, teams embed validation directly into the infrastructure definitions. Policy as Code further codifies security and compliance rules, making them enforceable and automated across environments.
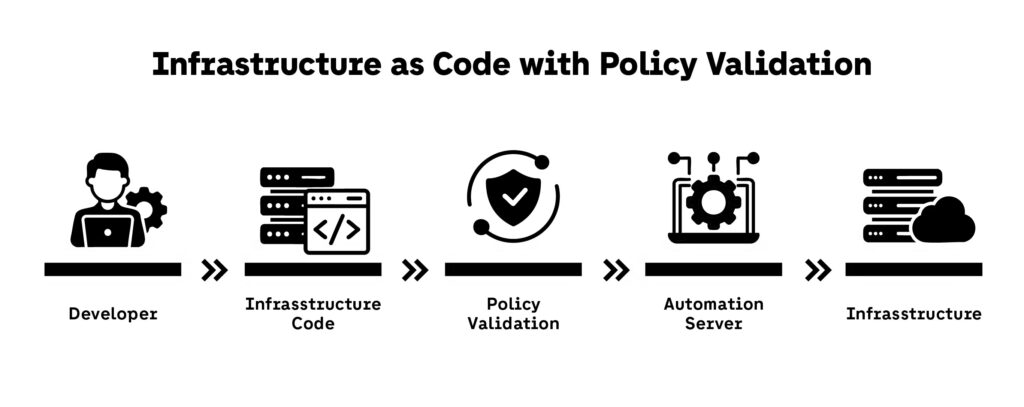
The power of IaC in DevSecOps lies in consistency and reproducibility. Every VM, network rule, or container setup is captured as code, making it auditable, testable, and reproducible. Tools like Terraform and AWS CloudFormation are common choices. DevSecOps teams enhance this by integrating tools like Checkov (Bridgecrew) and tfsec (Aqua Security) into their pipelines to scan IaC definitions and prevent misconfigurations before infrastructure is provisioned.
Puppet’s 2025 blog on DevSecOps automation details how organizations use policy enforcement to catch misconfigurations and enforce governance continuously. According to their analysis, mature teams reduce configuration drift and cloud misconfigurations by up to 50% by automating IaC validation and remediation.
Policy as Code extends this by transforming security or compliance rules into executable logic. Open Policy Agent and HashiCorp Sentinel allow DevSecOps teams to enforce policies before deployment—if a configuration violates a rule (e.g. over-permissive IAM policy, public database), the pipeline halts. This approach removes human error and standardizes enforcement across teams.
From a cultural and workflow standpoint, IaC + Policy as Code align responsibilities. Developers receive feedback on configuration violations early, while security engineers maintain and evolve policy definitions. This shared accountability embodies the spirit of DSO. In Puppet’s 2024 State of DevOps / platform engineering report, many organizations noted how embedding security into platform teams improved consistency and compliance outcomes.
In 2025, IaC and Policy as Code represent some of the most tangible, automatable advances in DevSecOps maturity. Security becomes not a checklist but a living, versioned component of infrastructure. For agile teams, this means faster delivery, lower configuration errors, and stronger control over governance—all essential elements for successful DevSecOps adoption.
5. Software Supply Chain Security
Software supply chain security is rapidly becoming a critical pillar in modern DevSecOps strategies. Applications rely increasingly on open-source libraries, third-party modules, and container images, making every dependency a potential attack vector. DevSecOps addresses this risk by automating visibility, validation, and trust for all components used in the build process.
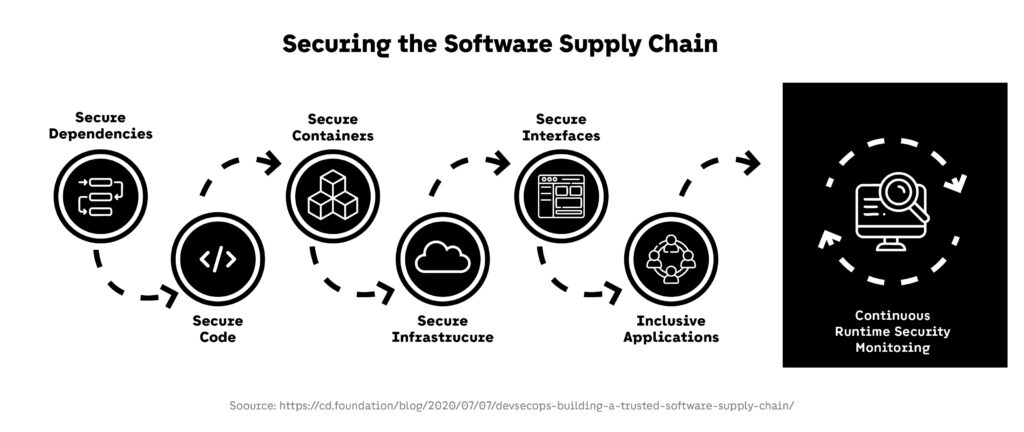
A foundational tool in this domain is the Software Bill of Materials (SBOM), which acts like an ingredient list for software—documenting all components, versions, and dependencies. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published an updated draft of the 2025 Minimum Elements for SBOMs, reflecting current practices and tool maturity. This new guidance helps organizations standardize how SBOMs are generated, consumed, and validated across DevSecOps workflows.
According to the Anchore 2024 Software Supply Chain Security Report, only 1 in 5 organizations say they have full visibility into their open-source components, and 78% plan to increase SBOM usage in the next 18 months (www.anchore.com). This underscores how many teams are still establishing supply chain guardrails. Anchore also noted a 200 % increase in organizations prioritizing software supply chain security over recent years.
In DevSecOps pipelines, SBOMs are generated and validated during the build or containerization stage. Validation includes verifying cryptographic hashes, license compliance, integrity checks, and dependency graphs. Tools like Anchore Enterprise, Sigstore, and SLSA (Supply-chain Levels for Software Artifacts) provide structured frameworks and attestation mechanisms for build transparency. These measures enable artifact provenance and tamper detection—core DevSecOps requirements for secure builds.
Ensuring provenance and secure signing of artifacts is critical. SLSA defines levels of assurance to prevent unauthorized changes to build artifacts. In many DevSecOps practices, CI/CD platforms now support SLSA attestation natively or via integration, allowing teams to verify that an artifact was built under a trusted process. This ensures every component that enters production is traceable and verifiable.
For agile teams, supply chain controls in DevSecOps aren’t just about preventing risk—they’re about resilience. Automating component scanning, enforcing SBOM policies, and verifying build integrity ensure that every release, dependency, and artifact is trustworthy. As development cycles accelerate, these capabilities complete the DevSecOps loop from secure code to secure delivery.
Trends and Future Directions Shaping DevSecOps in 2025
DevSecOps continues to evolve rapidly as organizations balance agility with complex security demands. In 2025, the most forward-looking teams are integrating intelligence, automation, and governance across every phase of delivery. These emerging trends define how DevSecOps is reshaping secure software delivery for the years ahead.
AI-Driven Security and Predictive Analytics
Artificial intelligence has transitioned from a support tool into a central capability within DevSecOps pipelines. In 2025, AI models assist in vulnerability prioritization, anomaly detection, and automated remediation. This shift allows teams to predict and prevent risks rather than reacting after incidents occur.
According to Google Cloud’s 2025 DevOps and AI Integration report, 62% of high-performing teams use AI-powered threat modeling to guide code reviews and patch management. SentinelOne’s adaptive defense engine and Microsoft Defender for Cloud exemplify how real-time telemetry and behavioral analysis detect zero-day exploits before they spread.
For DevSecOps teams, AI-driven security means integrating ML algorithms into CI/CD workflows to learn from build histories and runtime data. Over time, these models fine-tune security baselines and automate triage, reducing false positives and response times. By embedding AI directly into DevSecOps processes, organizations evolve from static rule enforcement to continuous, data-driven resilience.
Zero Trust Architecture Integration
Zero Trust has moved from networking theory to a foundational security model within DevSecOps. The principle—“never trust, always verify”—now extends to every identity, API call, and code interaction within software delivery pipelines.
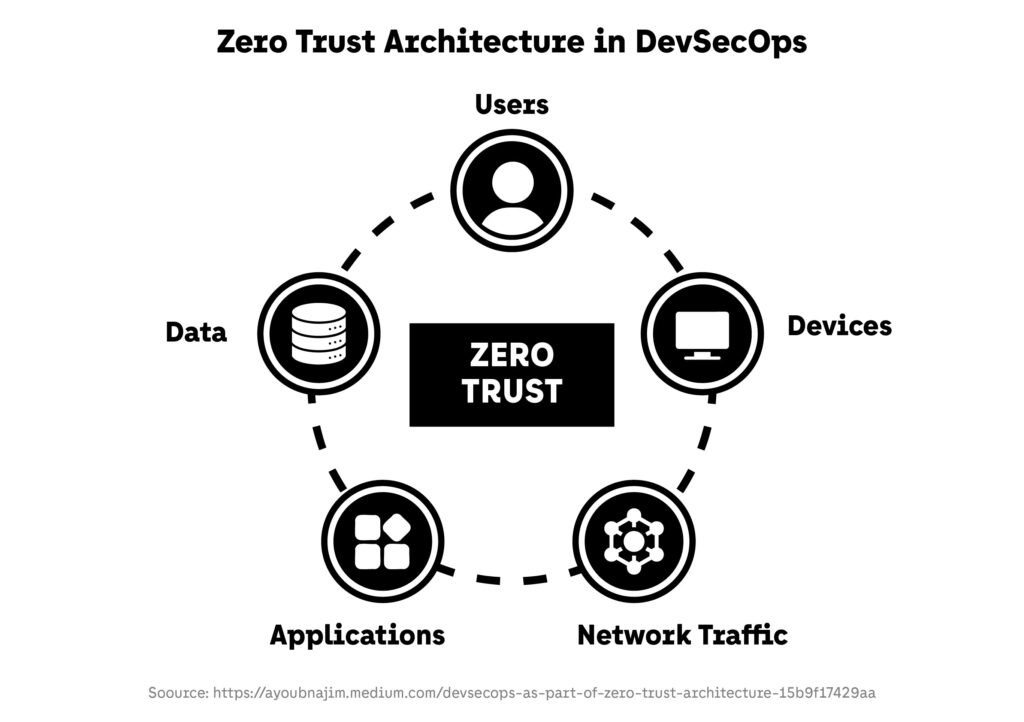
In 2025, GitLab’s Global DevSecOps Report found that teams adopting Zero Trust principles in their build systems reduced unauthorized access incidents by 41%. Integration with identity providers such as Okta and Microsoft Entra ID enables fine-grained permission management and continuous authentication across CI/CD workflows.
For DevSecOps practitioners, this approach means embedding access policies directly into infrastructure and pipeline configuration. Secrets are managed through automated vaults, while token expiration, role-based access control, and continuous verification protect credentials from misuse. In combination with Policy as Code, Zero Trust enforces context-aware authorization automatically, ensuring every user, service, and process operates under least-privilege principles—one of the cornerstones of advanced DevSecOps maturity.
Hyperautomation and Policy Enforcement
Hyperautomation is redefining how DSO teams scale security across expanding environments. Unlike traditional automation, hyperautomation combines orchestration, machine learning, and intelligent policy management to eliminate repetitive tasks and dynamically adapt controls.
Puppet’s DevSecOps Automation Report highlights enterprises that link scanning tools, ticketing systems, and compliance frameworks through orchestration engines—reducing manual intervention by 60%. DevSecOps pipelines now use workflow automation tools like StackStorm or Ansible Automation Platform to chain together security operations, compliance audits, and patch management.
Policy as Code remains central to hyperautomation. With Open Policy Agent, DevSecOps teams encode compliance rules that evolve automatically as infrastructure or configurations change. AI-enhanced rule generation is also emerging, where models analyze environment data and suggest policy updates. The result is a self-regulating ecosystem—DevSecOps pipelines that continuously test, enforce, and remediate without waiting for manual review.
Compliance-as-Code and Continuous Governance
Regulatory compliance is no longer a post-deployment task; it’s an embedded, measurable process. In 2025, DevSecOps teams codify compliance frameworks like ISO 27001, GDPR, and SOC 2 as automated rules that validate every change before it reaches production.
The Cloud Security Alliance reports that organizations adopting continuous compliance automation cut audit preparation time by up to 70%. Tools like Terraform Compliance, Conftest, and Open Policy Agent integrate directly into pipelines to ensure every build meets policy before release. This Compliance-as-Code model reduces audit fatigue while increasing traceability, as every approval and denial is logged automatically.
For agile teams, continuous governance within DevSecOps transforms compliance into a living part of the delivery process. Instead of reacting to audits, teams generate ongoing, verifiable evidence of conformity—turning governance from a bottleneck into a competitive advantage.
The Expansion of DevSecOps Beyond Software
DevSecOps is expanding into new domains beyond traditional application development. As edge computing, IoT, and AI systems grow, they bring unique security challenges—distributed infrastructure, unverified data inputs, and autonomous decision-making.
In 2025, organizations are applying DevSecOps frameworks to secure machine learning pipelines and data flows. The Linux Foundation’s OpenSSF reports that introducing integrity checks and model provenance into ML workflows significantly reduces risks of model tampering and data poisoning. Edge deployments now use DevSecOps-style pipelines to manage updates securely across remote devices, ensuring configuration consistency and trusted firmware.
This expansion underscores a critical evolution: DevSecOps is no longer just about protecting code—it’s about securing entire digital ecosystems. By extending its principles to AI, IoT, and edge systems, DevSecOps becomes a universal approach to resilience, adaptable to any environment where automation and security must coexist.
How Agile Teams Can Implement DevSecOps — Practical Steps & Roadmap
Implementing DevSecOps within an agile organization requires a thoughtful blend of process transformation, automation, and cultural change. Unlike traditional security programs that rely on separate review gates, DevSecOps builds security into every layer of development and delivery. For agile teams, this means rethinking collaboration, redefining “done,” and integrating continuous feedback into every sprint. The roadmap below provides a structured, step-by-step approach to embedding DevSecOps successfully—without disrupting velocity or team cohesion.
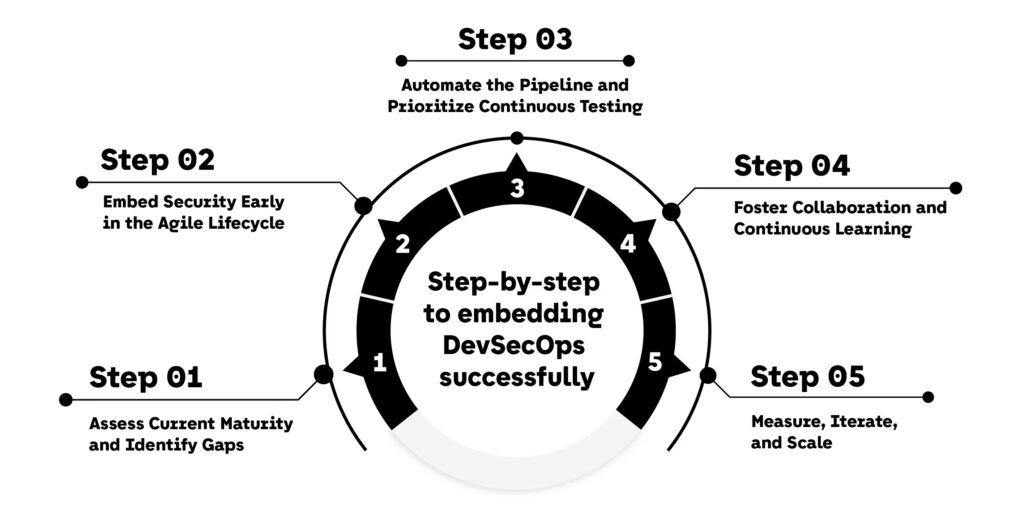
Step 1. Assess Current Maturity and Identify Gaps
Before introducing new tools or processes, teams must first understand where they stand. A DevSecOps maturity assessment helps identify weaknesses across code security, automation coverage, and communication between teams. Frameworks such as the OWASP DevSecOps Maturity Model and GitLab’s DevSecOps Assessment allow organizations to benchmark their readiness.
During this evaluation, agile teams should analyze their existing CI/CD pipelines, code review processes, and response workflows. Are vulnerabilities discovered late in the release cycle? Are incidents tracked but not remediated quickly? These insights form the foundation of an effective DevSecOps roadmap. Teams can then prioritize high-impact improvements—like automating repetitive scans, improving visibility, or defining clear ownership for security incidents.
At this stage, leadership alignment is also critical. DevSecOps requires cross-functional sponsorship, where engineering, product, and security teams agree on goals and shared accountability metrics. Without that alignment, DevSecOps initiatives risk becoming siloed projects rather than cultural shifts.
Step 2. Embed Security Early in the Agile Lifecycle
The most impactful DevSecOps principle is “shift left”—bringing security into the earliest phases of design and development. In agile teams, this translates into integrating security tasks directly into sprint planning and definition of done. Developers should perform vulnerability checks as they write code, not weeks later in QA.
Tools such as Snyk, GitHub Advanced Security, and SonarQube help identify insecure dependencies, misconfigurations, and hard-coded secrets. By integrating these tools into development environments, DevSecOps teams ensure that security findings appear alongside functional bugs—making fixes a natural part of daily work.
Real-world examples support this approach. According to the GitLab 2024 Global DevSecOps Report, teams that integrated static analysis into merge requests reduced critical vulnerabilities by 43%. When security becomes part of agile rituals—standups, retrospectives, and sprint reviews—it shifts perception from “extra work” to “essential quality.” Over time, developers gain ownership of security outcomes, fulfilling the DevSecOps goal of shared responsibility.
Step 3. Automate the Pipeline and Prioritize Continuous Testing
Automation lies at the heart of DevSecOps implementation. Every build, merge, or deployment should trigger consistent, automated security checks. This ensures that vulnerabilities, policy violations, or configuration drifts are detected before production.
In practical terms, teams should integrate Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), dependency scanning, and Infrastructure as Code (IaC) validation into their CI/CD pipelines. Platforms such as Jenkins, GitHub Actions, and GitLab CI/CD all support DevSecOps plug-ins and reusable templates. According to Google Cloud’s 2024 Accelerate State of DevOps report, teams with fully automated pipelines recover from security incidents 45% faster than those with manual review gates.
Automation in DevSecOps doesn’t stop at detection. Tools like HashiCorp Sentinel and Open Policy Agent enable Policy as Code, automatically enforcing compliance rules within builds. Over time, automation evolves into self-healing workflows—where issues are not only detected but remediated automatically. This approach scales DevSecOps efficiently across distributed teams, reducing human error and operational fatigue.
Step 4. Foster Collaboration and Continuous Learning
Cultural alignment remains the defining success factor of DevSecOps. In agile organizations, silos between development, security, and operations can undermine even the best automation strategy. A mature DevSecOps environment replaces friction with collaboration and transparency.
Embedding security engineers into agile squads ensures that security expertise is present from backlog grooming through deployment. These embedded roles help developers interpret findings, prioritize risks, and align security with business goals. Internal training programs, brown-bag sessions, and post-incident reviews help normalize security discussions across all roles.
Puppet’s 2025 DevSecOps Automation Report shows that organizations emphasizing cross-functional training saw a 55% increase in vulnerability remediation efficiency. This outcome reinforces a central truth: DevSecOps is not a toolchain—it’s a mindset. The more teams learn together, the faster they can respond to evolving threats.
Step 5. Measure, Iterate, and Scale
DevSecOps thrives on measurement. Continuous improvement depends on real data, not assumptions. Teams should define metrics such as mean time to detection (MTTD), mean time to remediation (MTTR), and deployment frequency to gauge progress. Tracking these metrics allows agile teams to evaluate whether DevSecOps efforts are improving performance or simply adding complexity.
Reporting and visualization tools integrated into dashboards—such as Grafana or Datadog —can display security and operational KPIs side by side. This transparency reinforces accountability across all stakeholders.
As practices mature, scaling DSO requires expanding automation coverage, strengthening policy enforcement, and embedding advanced capabilities like AI-driven threat detection or Zero Trust validation. Organizations that invest in iterative improvement avoid the stagnation that often follows initial adoption. They evolve their DevSecOps framework continuously, aligning it with the organization’s technology stack and culture.
In 2025, successful DevSecOps implementation is less about deploying the right tools and more about building the right habits. Agile teams that start small—integrating automation, feedback, and training—can scale DevSecOps sustainably across the organization. When fully adopted, DevSecOps transforms from a methodology into a shared language between security, development, and operations: one that accelerates innovation while keeping risk under control.
The Future of DevSecOps: Building Continuous Security for Agile Success
The evolution of DSO marks one of the most important transformations in modern software engineering. For agile teams, it represents a fundamental change in how security, speed, and collaboration coexist. In 2025, organizations that treat this approach not as an optional framework but as an operational mindset are achieving measurable advantages—faster delivery, improved resilience, and greater customer trust.
This modern way of working allows teams to integrate protection seamlessly into development pipelines, automating validation, testing, and governance. It eliminates the old tension between innovation and safety by embedding security directly into continuous integration and delivery. Each iteration becomes a learning opportunity, strengthening defenses while preserving agility. According to GitLab’s Global Report, organizations embracing this model are reducing production incidents and time-to-remediation more effectively than any traditional security approach.
Its true strength lies in adaptability. Whether applied to application development, infrastructure automation, or AI and edge systems, the same principles hold: automate everything, measure continuously, and collaborate without silos. As technology ecosystems grow more complex, this framework provides a structured, scalable way to maintain control without sacrificing innovation. The cultural alignment it creates between developers, security specialists, and operations teams ensures that accountability is shared and success is collective.
For agile organizations, adopting these practices is no longer just about preventing breaches—it’s about enabling continuous assurance. Teams using integrated security frameworks move faster, detect risks earlier, and recover more intelligently when incidents occur. The approach fosters transparency, discipline, and foresight, helping engineering teams make security an integral part of business strategy.
As the industry moves toward increasingly autonomous systems, this methodology will continue to evolve into the default mode of software delivery. The combination of AI-driven detection, Zero Trust enforcement, and compliance automation will make continuous protection the foundation of every high-performing agile organization. Those who invest in this approach today are not just adopting a methodology—they’re building a culture capable of anticipating change, mitigating risk, and delivering innovation with confidence.
At Fyld, we believe that DevSecOps is the foundation of modern digital excellence—empowering agile teams to deliver secure, scalable, and forward-thinking solutions that keep businesses ahead of the curve.


