Container security has evolved from a specialized engineering concern into a strategic requirement as organizations prepare for 2026. With containerized workloads now underpinning critical business systems, container security plays a central role in how modern applications are built, deployed, and protected. The continued expansion of Kubernetes, microservices, and API-driven architectures has increased operational speed, but it has also amplified risk when container security is treated as an afterthought.
Threat actors increasingly exploit weaknesses in container environments, including misconfigured clusters, exposed container images, and insufficient isolation at runtime. Container security incidents are no longer limited to development environments; they now directly impact production systems, regulatory compliance, and customer trust. This trend mirrors the broader threat landscape described in this blogpost, where infrastructure-level attacks and software supply chain compromise remain dominant going into 2026. Cloud-focused risks such as lateral movement and insecure workloads, outlined here, further highlight why container security must be addressed as part of a wider cloud security strategy.
Cloud-native platforms further expand the attack surface through lateral movement, insecure workloads, and weak trust boundaries between services. These risks, outlined in more detail here, demonstrate why containerized environments must be secured as part of a wider cloud security strategy rather than treated in isolation.

In 2026, container security extends well beyond scanning images for known vulnerabilities. Effective protection spans the entire application lifecycle, including secure image creation, dependency validation, policy enforcement, and runtime monitoring. Without a mature approach, organizations struggle to maintain visibility and control across fast-moving CI/CD pipelines and highly dynamic infrastructure.
The growing reliance on shared base images and third-party dependencies has also increased systemic risk. A single compromised image can propagate across hundreds of services in minutes. Container security mitigates this risk by enforcing controls early and validating workloads continuously. When these protections are embedded into engineering workflows, teams reduce exposure without sacrificing delivery speed.
This guide focuses on practical implementation for 2026. It examines how tools and techniques are applied in real production environments, from vulnerability scanning and runtime protection to orchestration policies and DevSecOps integration. Each section explains what works, why it works, and where current approaches still face limitations.
By the end of this article, you will have a clear, practical understanding of how to design, implement, and sustain secure containerized platforms using proven techniques aligned with real-world engineering constraints.
Container Vulnerability Scanning
Container vulnerability scanning is a foundational component of container security because it addresses risk at the earliest possible stage. In 2026, container security programs rely on vulnerability scanning to prevent known weaknesses from being embedded into container images and replicated across environments. Since container images are frequently reused across teams and services, a single vulnerability can quickly escalate into a widespread container security issue if it is not detected early.
Why Container Vulnerability Scanning Is Foundational to Container Security
Container security depends on prevention rather than reaction. Containers are designed to be immutable and redeployed frequently, which means vulnerabilities introduced during image creation often persist unchanged throughout the lifecycle. Container vulnerability scanning enables teams to identify insecure packages, outdated libraries, and exposed components before images are promoted to registries or production. Without this control, container security efforts become reactive, increasing the likelihood of emergency patches and service disruption.
What Container Vulnerability Scanning Analyzes and Where It Fits in the Lifecycle
From a technical standpoint, container vulnerability scanning inspects the full contents of a container image. This includes operating system packages, language-specific dependencies such as Java, Python, or Node.js libraries, and transitive dependencies pulled in indirectly. Container security tools compare these components against authoritative vulnerability databases, including NVD, to identify known CVEs.
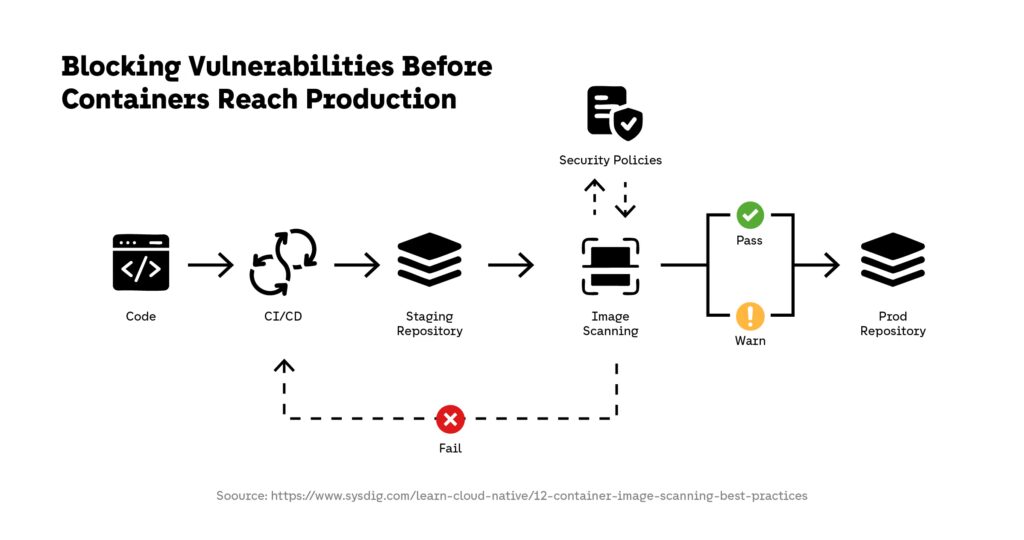
Effective container security requires scanning at multiple points. Build-time scanning prevents vulnerable images from being created. Registry scanning ensures stored images remain compliant as new vulnerabilities are disclosed. Continuous rescanning allows container security teams to detect newly reported risks in images that are already deployed. Open-source tools such as Aqua Trivy are commonly used to automate this process across CI/CD pipelines and container registries.
Real-World Container Security Example: Blocking a Critical Vulnerability
A common real-world container security scenario involves vulnerabilities discovered in widely used system libraries. In late 2025, multiple organizations identified high-severity OpenSSL vulnerabilities in container images built from trusted base images. Container vulnerability scanning detected these flaws during CI runs, automatically blocking image promotion and triggering rebuilds with patched dependencies. By stopping vulnerable images before deployment, container security teams prevented the issue from spreading across production workloads.
Prioritization, Policy, and Governance in Container Security Scanning
Modern container security scanning goes beyond generating lists of vulnerabilities. Effective container security requires prioritization based on severity, exploitability, and reachability. Developer-focused platforms such as Synk Container provide context on whether a vulnerability is actually reachable by running code, helping teams focus on issues that present real risk.
More mature programs also apply policy-based governance. Enterprise container scanning solutions enable organizations to define automated rules that block container images with critical vulnerabilities, unapproved licences, or untrusted sources. For example, Anchore Enterprise provides a mechanism for scanning containerized software for vulnerabilities and security risks across the development process, from CI/CD pipelines to registry and runtime environments, with policy enforcement and remediation workflows.
This approach ensures security standards are enforced consistently across teams and environments. It also allows security teams to automate the application of compliance requirements and reduce manual intervention, strengthening overall container security posture.
Limitations of Container Vulnerability Scanning and the Need for Runtime Security
Despite its importance, container vulnerability scanning has clear limitations. It cannot detect zero-day exploits, malicious behavior introduced after deployment, or attacks that exploit application logic at runtime. False positives may also occur when package metadata is incomplete. For this reason, container vulnerability scanning must be complemented by runtime container security, which monitors container behavior once workloads are running.
Container vulnerability scanning remains essential to container security in 2026 because it reduces risk before containers reach production. When combined with runtime protection and Kubernetes security controls, it forms a layered container security strategy that is both scalable and resilient.
Runtime Container Security
Runtime container security focuses on protecting containerized workloads while they are actively running in production. While vulnerability scanning strengthens container security before deployment, it cannot detect threats that emerge at runtime. In 2026, runtime container security will become a critical layer because attackers increasingly exploit misconfigurations, compromised credentials, and zero-day techniques that only surface once containers are live.
In 2026, protection extends well beyond scanning images for known vulnerabilities. Effective safeguards span the entire application lifecycle, including secure image creation, dependency validation, policy enforcement, and runtime monitoring. Without a mature approach, organizations struggle to maintain visibility and control across fast-moving CI/CD pipelines and highly dynamic infrastructure.
Why Runtime Container Security Is Essential
Strategies that rely solely on image scanning and deployment-time controls assume that workloads remain static once they are running. In reality, containers operate in highly dynamic environments where scaling events, service discovery, and external integrations continuously change runtime behavior. Credentials can be exposed, APIs can be abused, and previously trusted services can become attack vectors. Without runtime container security, these changes remain invisible, leaving container security controls blind once applications are live.
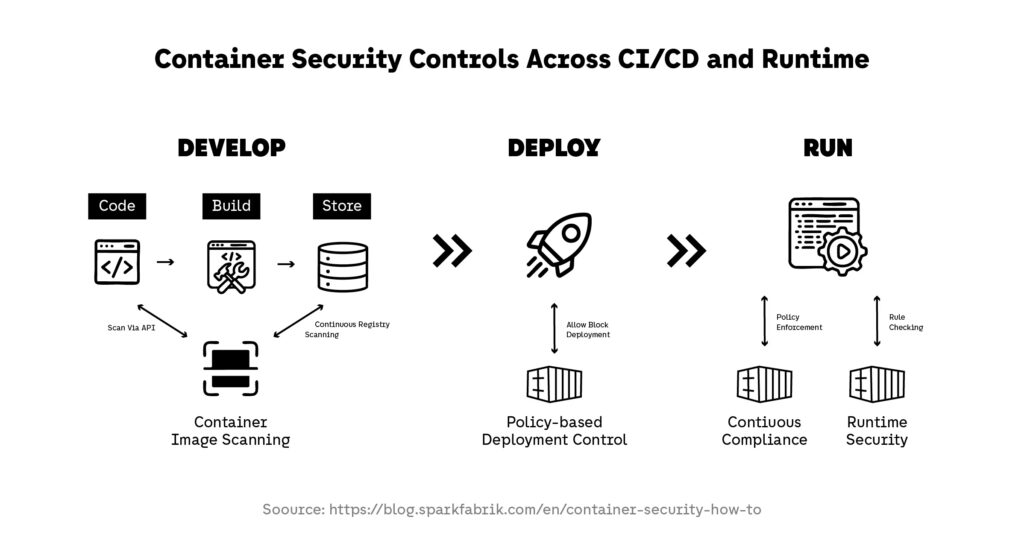
Runtime container security restores visibility during execution by continuously monitoring how containers behave in production. By tracking process execution, file access, and network activity, runtime container security detects deviations from expected behavior that indicate compromise. This real-time insight allows security teams to respond quickly, contain threats, and preserve the integrity of containerized workloads. In 2026, this continuous monitoring is no longer optional; it is a necessary component of any effective container security strategy.
How Runtime Container Security Works in Practice
From a technical perspective, runtime container security tools integrate closely with the host operating system and container runtime. They observe system-level events such as process creation, file modifications, and network activity using kernel-level signals. These events are evaluated against predefined rules or behavioral models to identify suspicious activity. Open-source projects like Falco are commonly used to detect unexpected behavior in Kubernetes environments through rule-based monitoring, as documented in the Falco rules repository.
In more advanced deployments, runtime container security solutions enrich detection with contextual data such as namespace, workload identity, and Kubernetes metadata. This context helps security teams distinguish between legitimate operational activity and genuine threats, reducing false positives while maintaining strong container security coverage.
Real-World Runtime Container Security Example
A practical runtime container security scenario involves detecting malicious command execution inside a running container. In several documented Kubernetes incidents during 2025, attackers gained access through exposed services and attempted to deploy cryptocurrency mining software within containers. Runtime tools detected abnormal process execution patterns and unexpected outbound network connections, triggering alerts and enabling rapid containment. Without runtime monitoring, these activities would have remained invisible to image-based container security controls.
Balancing Detection and Performance
One concern often raised about runtime container security is performance overhead. Modern runtime container security tools are designed to minimize impact by focusing on security-relevant events rather than full system tracing. Properly tuned rules and policies are essential to avoid excessive alerting. When implemented correctly, runtime container security provides high-fidelity detection with minimal performance tradeoffs.
Limitations and Integration with Other Container Security Controls
Runtime security is not a replacement for vulnerability scanning or Kubernetes security controls. It cannot prevent insecure images from being deployed or misconfigurations from being introduced. Instead, it complements other container security layers by detecting threats that emerge during execution. A layered container security strategy combines runtime monitoring with scanning, policy enforcement, and network controls to achieve defense in depth.
Runtime security plays a critical role in protecting modern containerized environments in 2026. By monitoring live workloads and detecting suspicious behavior in real time, it ensures that container security remains effective even as threats evolve. In the next section, we will explore how Kubernetes security and policy enforcement strengthen container security at the orchestration layer.
Kubernetes Security and Policy Enforcement
Kubernetes security plays a defining role in how containerized workloads behave in production. While image scanning and runtime monitoring protect individual containers, Kubernetes determines how those containers are scheduled, connected, and granted access to shared resources. In 2026, many container security failures originate not from vulnerable code, but from orchestration-level misconfigurations that expose workloads unnecessarily.
Kubernetes acts as the control plane for containerized environments. Decisions made at this layer affect isolation boundaries, identity management, network access, and privilege levels. As a result, Kubernetes security is inseparable from container security. If orchestration policies are weak or inconsistently applied, even well-scanned and well-monitored containers can become exploitable.
Why Kubernetes Is Central to Container Security
Kubernetes security defines the conditions under which containers run. It controls which images are allowed to execute, which permissions workloads receive, and how services communicate. Misconfigured Kubernetes clusters often allow containers to run with excessive privileges, access sensitive namespaces, or communicate freely across the environment. These issues undermine container security by expanding the blast radius of any compromise.
In resilient architectures, Kubernetes security acts as a gatekeeper rather than a passive scheduler. Organizations that design resilient backend platforms emphasize strict defaults, workload isolation, and automated controls at the orchestration layer.
Policy Enforcement at the Orchestration Layer
Policy enforcement is one of the most effective ways to improve Kubernetes security at scale. Admission controls allow teams to validate or reject workloads before they are deployed. Policies can enforce requirements such as non-root execution, restricted capabilities, approved image sources, and mandatory resource limits. By embedding these rules into the cluster, teams ensure consistent enforcement without relying on manual reviews.
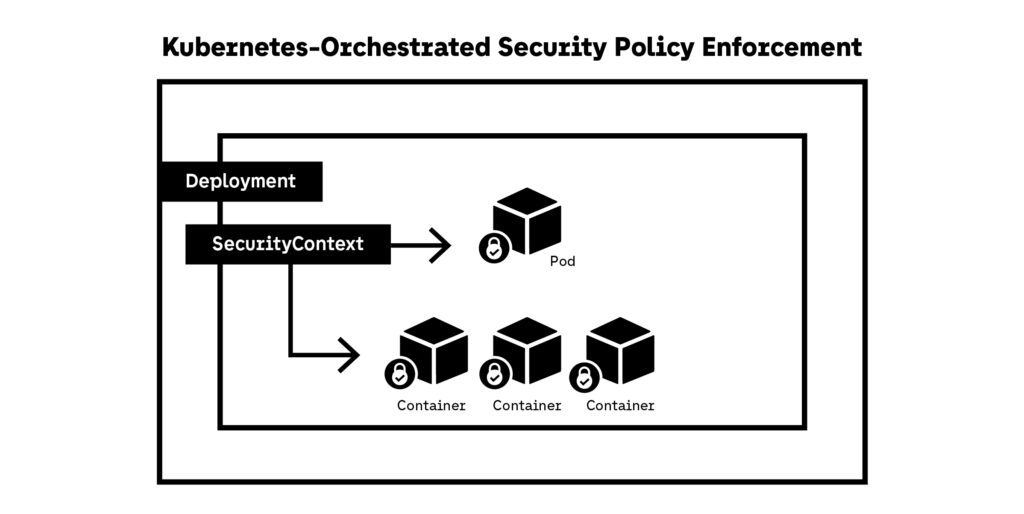
Policy-as-code approaches make Kubernetes security repeatable and auditable. Policies are versioned, tested, and applied automatically, reducing configuration drift. This strengthens container security by preventing insecure workloads from ever reaching runtime, even in fast-moving environments with frequent deployments.
Real-World Kubernetes Security Example: Preventing Privilege Escalation
A common real-world Kubernetes security issue involves privilege escalation through overly permissive pod configurations. In several production incidents reported in 2025, containers were allowed to run as root with access to host-level resources. Attackers exploited these configurations to escape container boundaries and access sensitive data.
Organizations mitigated this risk by enforcing Kubernetes policies that blocked privileged pods and restricted service account permissions. When misconfigured workloads were submitted, the cluster rejected them automatically. This orchestration-level control prevented insecure deployments and reinforced container security without requiring developers to manually interpret security guidelines.
Kubernetes Security Tradeoffs and Operational Reality
While Kubernetes security policies are powerful, they introduce operational complexity. Poorly designed policies can block legitimate workloads, slow delivery, or create friction between platform and development teams. Effective Kubernetes security requires collaboration, clear documentation, and gradual enforcement.
Successful teams treat Kubernetes security as an evolving system. Policies are introduced in audit mode, refined based on feedback, and enforced progressively. This approach balances control with velocity and ensures that container security improves without disrupting delivery.
Kubernetes security and policy enforcement form a critical layer in a defense-in-depth strategy. When orchestration controls are aligned with image scanning and runtime monitoring, organizations gain consistent, scalable container security that supports both resilience and speed.
Container Image Scanning and Software Supply Chain Security
Container image scanning and software supply chain security address one of the most persistent sources of risk in modern platforms: trust in what gets built and shipped. As organizations move toward 2026, container security is increasingly shaped by the integrity of container images and the dependencies they include. Even well-configured clusters and strong runtime controls can be undermined if container images themselves are compromised.
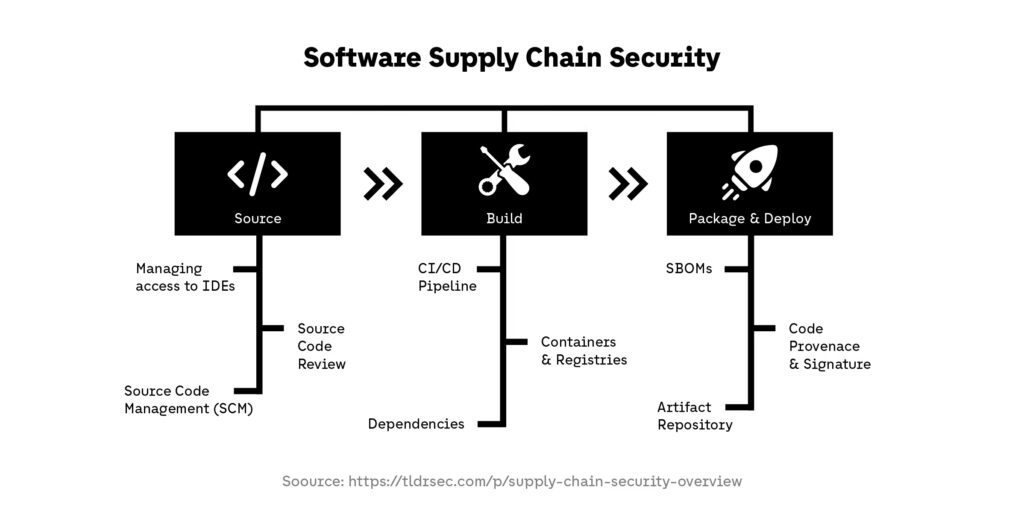
Container images are rarely built entirely from scratch. Most are assembled from base images, open-source libraries, and third-party components maintained outside the organization. This dependency chain introduces supply chain risk, where a vulnerability or malicious change upstream can silently propagate downstream. Container security practices must therefore extend beyond internal code and account for the full origin and composition of container images.
Why Container Images Are a Supply Chain Risk
From a container security perspective, container images represent a snapshot of code, configuration, and dependencies frozen at build time. If a base image contains a vulnerable package or an embedded secret, every downstream image inherits that risk. In several high-profile incidents between 2024 and 2025, attackers targeted popular base images and build tooling, knowing that a single compromise could affect thousands of deployments.
This is why container security teams increasingly treat container images as supply chain artifacts rather than simple deployment units. Image provenance, source verification, and dependency transparency have become essential to maintaining trust in containerized workloads.
How Container Image Scanning Strengthens Container Security
Container image scanning focuses on analyzing images before they are deployed, but with a broader scope than traditional vulnerability scanning. In addition to identifying CVEs, image scanning tools assess package sources, detect embedded credentials, and flag configuration issues such as unnecessary packages or excessive privileges. These checks strengthen container security by reducing the attack surface before workloads ever run.
Many organizations integrate image scanning directly into build pipelines and container registries. For example, Google Cloud Container Analysis provides image scanning and metadata tracking that helps teams understand what is inside their images and how risk evolves over time. This type of visibility supports container security by making image contents auditable and traceable.
Software Bills of Materials and Image Transparency
A growing focus in container security is the use of Software Bills of Materials, or SBOMs. An SBOM is a structured inventory of all components included in a container image. By generating SBOMs at build time, organizations gain transparency into their software supply chain and can quickly assess exposure when new vulnerabilities are disclosed.
SBOMs also support regulatory and compliance requirements that are becoming more common across industries. From a container security standpoint, they enable faster risk assessment and more targeted remediation, reducing the need for broad, disruptive rebuilds.
Real-World Example: Preventing a Compromised Image from Reaching Production
A common real-world scenario involves detecting untrusted components introduced through base image updates. In 2025, several engineering teams identified unexpected package changes in updated base images that were not aligned with internal security standards. Container image scanning flagged these deviations during registry checks, preventing the images from being promoted to production. By enforcing image trust policies, teams avoided deploying workloads built on compromised foundations and maintained consistent container security controls.
Limitations and the Need for Layered Controls
While container image scanning and supply chain security are critical, they are not sufficient on their own. Image scanning cannot detect attacks that occur after deployment or abuses of legitimate functionality. It also depends on accurate metadata and timely vulnerability disclosures. For this reason, container security programs must combine image scanning with Kubernetes security controls and runtime monitoring to achieve defense in depth.
Container image scanning strengthens container security by establishing trust in what is deployed. When combined with supply chain transparency and layered enforcement, it helps organizations reduce risk without sacrificing the speed and flexibility that containers provide.
Integrating Container Security into DevSecOps Pipelines
Integrating container security into DevSecOps pipelines is what turns isolated controls into a cohesive, operational security strategy. By 2026, organizations that treat container security as a separate, post-deployment activity struggle to keep up with deployment velocity. In contrast, teams that embed container security directly into CI/CD workflows are able to prevent risk early while maintaining rapid delivery.
DevSecOps pipelines provide the automation layer that container security depends on. Every code commit, image build, and deployment event becomes an opportunity to enforce security controls consistently. When container security is integrated into these pipelines, checks are applied automatically and repeatedly, reducing reliance on manual reviews and minimizing configuration drift.
Shifting Container Security Left Without Slowing Delivery
A key principle of DevSecOps is shifting security left, closer to developers. In practice, this means container security checks run as part of the same workflows developers already use. Image scanning, policy validation, and configuration checks are triggered during pull requests or build stages, providing fast feedback before changes are merged.
Modern CI/CD platforms make this integration straightforward. For example, GitHub Actions allows teams to run container scanning and policy checks automatically on every build using reusable workflows. By surfacing container security issues early, teams reduce costly rework and avoid late-stage deployment blockers.
Automating Policy Enforcement Across Pipelines
Automation is essential to scaling container security across multiple teams and services. In DevSecOps pipelines, policies can be enforced programmatically to ensure that only compliant container images are deployed. These policies might include vulnerability thresholds, approved base images, or mandatory security configurations.
When policies are enforced automatically, container security becomes predictable and measurable. Teams no longer rely on informal guidelines or tribal knowledge. Instead, security expectations are encoded into the pipeline itself, ensuring consistent outcomes regardless of who builds or deploys an application.
Real-World DevSecOps Integration Example
A common real-world DevSecOps pattern involves integrating container security checks into a multi-stage pipeline. In 2025, several platform teams adopted pipelines where container images were scanned during build, validated again when pushed to registries, and rechecked before deployment. If a scan failed or a policy was violated, the pipeline blocked promotion automatically.
This approach allowed teams to deploy frequently without compromising container security. Developers received immediate feedback, security teams gained consistent enforcement, and operations teams reduced the number of high-risk deployments reaching production.
Balancing Developer Experience and Container Security
One of the main challenges in DevSecOps is balancing strong container security with developer experience. Overly strict controls or slow scans can frustrate teams and encourage workarounds. Successful organizations address this by tuning policies carefully, prioritizing high-impact risks, and providing clear remediation guidance.
When container security tools are fast, predictable, and integrated into existing workflows, developers are more likely to engage with them positively. This collaboration is critical to sustaining container security over time.
Integrating container security into DevSecOps pipelines ensures that security scales with delivery. By automating checks, enforcing policies, and providing early feedback, organizations build container security into the fabric of their software lifecycle rather than treating it as an external constraint.
Zero Trust and Container Network Security
Zero trust and container network security focus on limiting how workloads communicate once they are running. As containerized environments scale, unrestricted network access becomes one of the most common paths for lateral movement. In 2026, many container security incidents do not begin with a sophisticated exploit, but with an attacker moving freely between services after gaining an initial foothold.
Traditional network models assume that traffic inside a cluster is trustworthy. Zero trust challenges this assumption by treating every connection as untrusted by default. Applied to container environments, this means container-to-container communication is explicitly defined, continuously verified, and tightly scoped. Container network security becomes a critical control for reducing blast radius and containing breaches.
Why Network Controls Matter for Container Security
Containers are highly connected by design. Microservices communicate through APIs, message queues, and service meshes, often across namespaces and clusters. Without strong network controls, a compromised container can scan the internal network, access sensitive services, or exfiltrate data without triggering alarms. This is why container security strategies increasingly emphasize network segmentation alongside scanning and runtime detection.
Zero trust networking strengthens container security by enforcing least-privilege communication. Containers are only allowed to talk to the services they explicitly need. Everything else is denied by default. This approach dramatically reduces lateral movement and makes attacks noisier and easier to detect.
Enforcing Zero Trust with Kubernetes Network Policies
Kubernetes provides native mechanisms for defining network policies that control traffic between pods and namespaces. These policies allow teams to specify which workloads can communicate and on which ports. When applied consistently, Kubernetes network policies form the foundation of container network security.
In practice, many organizations adopt advanced networking solutions to simplify policy management and observability. For example, Cilium uses eBPF to enforce fine-grained network policies and provide deep visibility into container traffic, as described here. This level of insight helps teams validate that network behavior matches intended design, strengthening overall container security.
Service Meshes and Identity-Based Networking
Service meshes extend container network security by introducing identity-aware communication. Instead of relying solely on IP addresses, services authenticate each other using certificates or identities. This makes network policies more resilient to dynamic scaling and redeployments.
Platforms such as Istio provide mutual TLS, traffic authorization, and observability features that support zero trust principles, as outlined in this concept documentation. By combining identity, encryption, and policy enforcement, service meshes help ensure that only authenticated and authorized services can communicate, even inside the cluster.
Real-World Example: Containing a Breach with Network Segmentation
A common real-world scenario involves an exposed service that allows an attacker initial access to a single container. In several production incidents reported in 2025, organizations without network segmentation experienced rapid lateral movement across internal services. In contrast, teams that enforced zero trust network policies were able to contain the breach to a single workload. Unauthorized connection attempts were blocked automatically, limiting impact and simplifying incident response.
Tradeoffs and Operational Considerations
While zero trust networking significantly improves container security, it introduces operational complexity. Designing and maintaining network policies requires a clear understanding of service dependencies. Poorly defined rules can break legitimate traffic or slow deployments. Successful teams adopt network controls incrementally, starting with visibility and audit modes before enforcing strict policies.
Zero trust and container network security complete the layered defense strategy. When combined with image scanning, Kubernetes policy enforcement, runtime monitoring, and DevSecOps automation, network segmentation ensures that container security remains effective even when individual controls fail.
Building Effective Container Security for 2026
Modern platforms are no longer protected by a single control or tool. Security outcomes are shaped by how prevention, enforcement, and detection work together across the application lifecycle. Vulnerability management, software supply chain integrity, runtime monitoring, orchestration policies, and network segmentation must operate as a coordinated system rather than isolated safeguards.
Organizations that succeed focus on reducing risk early, limiting exposure during execution, and responding quickly when controls fail. This requires automation, clear ownership, and security mechanisms that align with how teams build and deploy software. When security controls are predictable and integrated into everyday workflows, they support resilience instead of slowing delivery.
In 2026, container security is most effective when treated as a continuous capability rather than a point solution. By combining layered controls with practical implementation and ongoing enforcement, teams can protect modern workloads while maintaining the speed and flexibility that containerized environments demand.


