Cybersecurity has entered a phase where incremental improvements are no longer sufficient. The combination of cloud-native architectures, identity-driven access models, and highly interconnected software ecosystems has fundamentally altered how risk is created and exploited. As organizations look ahead, cybersecurity trends are no longer shaped by isolated technologies or individual threat actors, but by structural changes in how digital systems are built and operated.
By 2026, many of the shifts that began earlier in the decade have reached a point of maturity. Artificial intelligence is now embedded in both offensive and defensive capabilities, software supply chains span hundreds of dependencies, and traditional network boundaries have largely dissolved. Recent analyses of major cybersecurity incidents, including FYLD’s prior examination of the most common threats organizations faced in 2025, show that these changes increasingly expose weaknesses in identity, integration, and governance rather than in individual systems.
This article examines the most consequential cybersecurity trends shaping organizations as they plan for 2026 and beyond. Rather than cataloguing tools or predicting short-lived tactics, it focuses on underlying patterns: how attackers adapt to modern environments, why legacy security models struggle to keep pace, and which strategic responses are gaining traction across industries. The goal is to help decision-makers interpret change, not react to noise.
To maintain that focus, this analysis deliberately avoids step-by-step implementation guidance, vendor comparisons, or deep technical configuration details. Those topics are better addressed in targeted follow-up articles. Instead, this pillar provides a high-level framework for understanding why cybersecurity trends are evolving as they are, and what those changes mean for organizations responsible for managing risk in increasingly complex digital systems. Viewed together, these cybersecurity trends point toward a fundamental shift in how organizations must think about digital risk, accountability, and trust in complex digital environments.
The Evolving Cyber Threat Landscape
Expanding Attack Surfaces in Modern Environments
The current cybersecurity environment is defined less by isolated incidents and more by systemic change. One of the most significant cybersecurity trends shaping organizations today is the continued expansion of the attack surface beyond traditional networks and endpoints. Modern enterprises operate across cloud platforms, third-party services, distributed development pipelines, and identity-driven access models, creating environments where security boundaries are increasingly fluid. This expansion is not the result of a single technology shift, but of cumulative architectural decisions. Cloud adoption, SaaS integration, and remote access have collectively increased the number of entry points attackers can target, often without triggering traditional security controls.
The Decline of Perimeter-Based Security Models
For years, cybersecurity strategies focused on defending infrastructure. Networks, servers, and data centers were treated as the primary assets requiring protection, with access tightly controlled at clearly defined entry points. This model assumed stability: predictable users, known systems, and limited external dependencies. Those assumptions no longer reflect operational reality. Applications are deployed continuously, infrastructure is abstracted through cloud services, and access is granted dynamically based on identity rather than location. As a result, attackers no longer need to breach a hardened perimeter. Instead, they exploit misconfigured resources, weak credentials, exposed APIs, or trusted integrations already inside the environment. This shift reflects broader cybersecurity trends in which trust relationships themselves become the primary target.
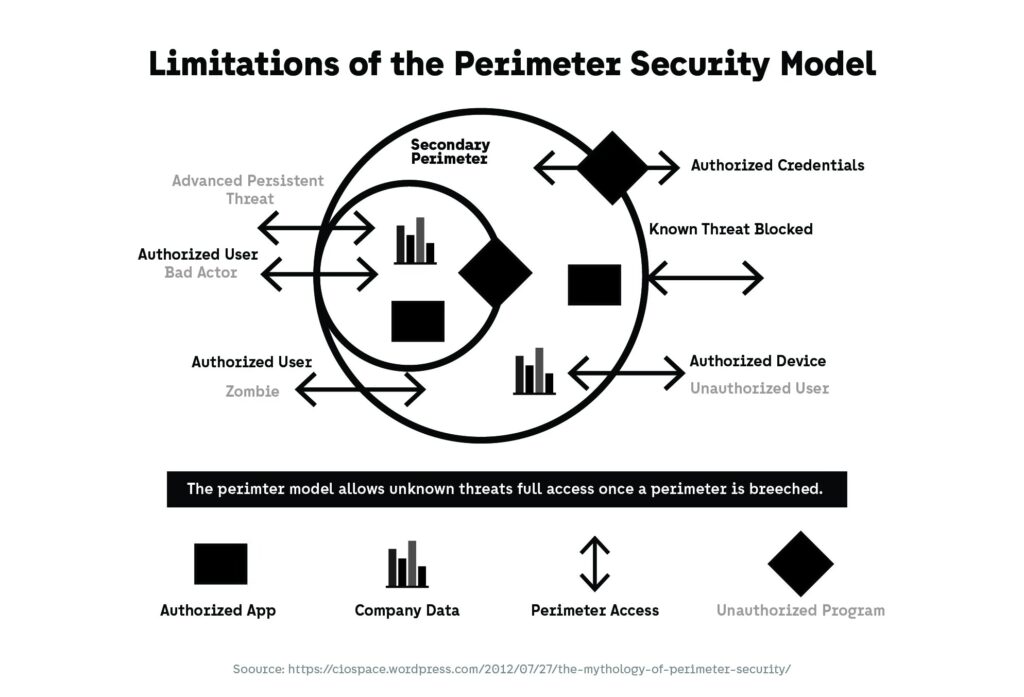
Once access is granted under a perimeter-based model, internal activity is often treated as inherently trustworthy. This creates an environment where attackers can move laterally with limited resistance, especially when identity, device, and application trust are loosely coupled. Even when security controls exist inside the perimeter, they are frequently optimized for detection rather than prevention, allowing malicious activity to persist undetected for extended periods. This dynamic explains why many modern incidents are not the result of perimeter failure alone, but of security models that assume trust where continuous verification is required.
Identity and Legitimate Access as Primary Attack Vectors
Industry reporting from 2024 onward shows that many high-impact incidents originate from legitimate access paths rather than direct exploitation of software vulnerabilities. According to recent analysis by the World Economic Forum, identity compromise and third-party access are now among the most common initial attack vectors in major breaches. These attacks often operate within expected system behavior, making them difficult to detect using traditional signature-based or perimeter-focused controls. As identity becomes the dominant control plane, weaknesses in access governance increasingly translate into systemic risk.
Automation and the Acceleration of Threat Activity
Attacker behavior has evolved alongside environmental complexity. Threat actors are more patient and increasingly focused on persistence rather than immediate disruption. Instead of deploying overt malware, many attacks prioritize long-term access, lateral movement, and gradual data exfiltration. Automation amplifies this approach. Automated reconnaissance tools continuously scan cloud environments, source code repositories, and exposed services, identifying weaknesses faster than most organizations can remediate them. In this context, cybersecurity trends are defined less by novel techniques and more by the speed, scale, and efficiency with which existing methods are applied across interconnected systems.
Supply Chain Dependencies and Shared Risk
Another defining characteristic of the modern threat landscape is the erosion of clear distinctions between internal and external risk. Third-party services, open-source components, and managed platforms are now integral to most systems. While these dependencies accelerate development and deployment, they also introduce shared risk that is difficult to fully assess or control. Increasingly, security incidents propagate through software supply chains rather than originating from direct attacks on a single organization, reinforcing the need to view risk as a systemic property rather than an isolated failure.
Taken together, these shifts show that the modern threat landscape is shaped less by individual vulnerabilities and more by structural change. Understanding how risk emerges across identities, platforms, and dependencies is essential, because the most impactful cybersecurity trends reflect how systems are designed and interconnected, not simply how attackers innovate.
AI-Powered Attacks and Defensive Challenges
AI as a Force Multiplier for Attackers
Artificial intelligence has lowered the barrier to entry for sophisticated attacks while simultaneously increasing their speed and scale. One of the most disruptive cybersecurity trends in recent years is the use of AI to automate reconnaissance, social engineering, and vulnerability discovery. Tasks that once required time, expertise, and manual effort can now be executed continuously and at scale, allowing attackers to adapt faster than traditional security processes.
Machine learning models are increasingly used to analyze large datasets harvested from breached systems, public repositories, and social platforms. This enables attackers to tailor phishing campaigns, identify high-value targets, and refine attack paths with greater precision. Rather than relying on generic techniques, AI-driven attacks are often context-aware, making them harder to distinguish from legitimate activity.
AI-Enhanced Phishing and Social Engineering
Phishing remains one of the most effective initial access techniques, and AI has significantly increased its effectiveness. Natural language generation allows attackers to produce convincing, grammatically accurate messages that adapt tone, context, and timing to specific targets. Voice synthesis and deepfake technologies further blur the line between legitimate communication and deception.
Recent reporting from 2024 highlights how generative AI has been used to scale targeted phishing campaigns across multiple industries, increasing success rates while reducing attacker effort. These developments demonstrate how cybersecurity trends driven by AI are amplifying long-standing attack methods rather than replacing them.
Accelerated Vulnerability Discovery and Exploitation
Beyond social engineering, AI is increasingly applied to technical attack workflows. Automated tools can scan codebases, APIs, and cloud configurations to identify weaknesses faster than manual review processes. When combined with continuous deployment environments, this creates a persistent race condition between attackers discovering flaws and organizations deploying fixes.
This acceleration challenges traditional vulnerability management models, which often rely on periodic scanning and delayed remediation. As systems grow more complex, AI-enabled attackers can exploit small windows of exposure that were previously considered low risk. This shift underscores how cybersecurity trends are reshaping not only attack techniques, but the timelines on which security teams must operate.
Defensive Limitations in an AI-Driven Threat Environment
While defenders also use AI for detection and response, the asymmetry between attackers and organizations remains significant. Security teams must operate within regulatory, operational, and ethical constraints, while attackers face few limitations. As a result, AI-driven defensive tools often lag behind the creativity and adaptability of malicious use cases.
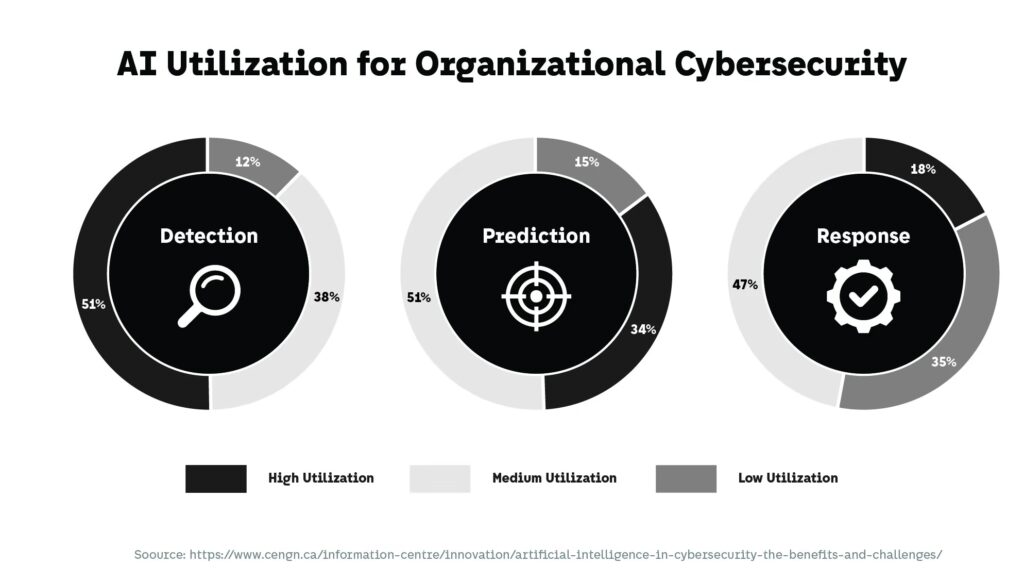
Many detection systems remain optimized for known patterns and historical data. AI-powered attacks, however, can continuously modify behavior to evade static rules and thresholds. This creates blind spots where malicious activity blends into normal system behavior, reinforcing the need to rethink assumptions about visibility and control.
Strategic Implications for Organizations
The growing role of AI in cyber attacks does not represent a single threat category, but a shift in how attacks are developed and executed. Among current cybersecurity trends, AI stands out not because it introduces entirely new risks, but because it accelerates existing ones beyond the capacity of legacy security models.
For organizations, the challenge is not simply adopting AI-based defenses, but understanding how automation changes the balance between offense and defense. Addressing this shift requires strategic responses that account for speed, scale, and adaptability—topics that connect directly to identity-centric security models and Zero Trust approaches explored later in this analysis. Among current cybersecurity trends, the growing role of AI illustrates how speed and automation are reshaping the balance between offense and defense.
Zero Trust as a Strategic Response
Why Zero Trust Is Gaining Strategic Relevance
As digital environments grow more distributed, organizations are re-evaluating security models built around implicit trust. One of the most consequential cybersecurity trends shaping enterprise strategy is the move away from perimeter-based assumptions toward continuous verification. Zero Trust has gained relevance not because it introduces new technology, but because it aligns more closely with how modern systems operate across cloud platforms, SaaS environments, and third-party integrations.
In environments where users, devices, and workloads change constantly, static trust decisions become obsolete almost immediately. Zero Trust reframes security around verification rather than location, requiring access decisions to be evaluated continuously based on context, risk, and behavior. This shift reflects a broader recognition that trust cannot be granted once and assumed indefinitely.
Identity as the New Security Perimeter
At the core of Zero Trust is the idea that identity—not network location—defines access. Users, service accounts, applications, and automated processes all operate under identities that can be compromised, misused, or overprivileged. As a result, identity has become one of the most critical control points in modern security architectures.
This focus on identity connects directly to earlier cybersecurity trends discussed in this article, particularly the rise of attacks that abuse legitimate credentials rather than exploit software vulnerabilities. Industry analysis from 2024 reinforces this shift, with recent guidance from the U.S. Cybersecurity and Infrastructure Security Agency emphasizing identity-centric controls as foundational to Zero Trust adoption. When identity is treated as the primary perimeter, access decisions must account for authentication strength, device posture, and least-privilege enforcement rather than relying on static network boundaries.
Zero Trust Is a Strategy, Not a Product
A persistent misconception is that Zero Trust can be implemented by purchasing a specific tool or platform. In practice, Zero Trust is an operating model that influences architecture, governance, and organizational decision-making. Tools may support this model, but they do not define it.
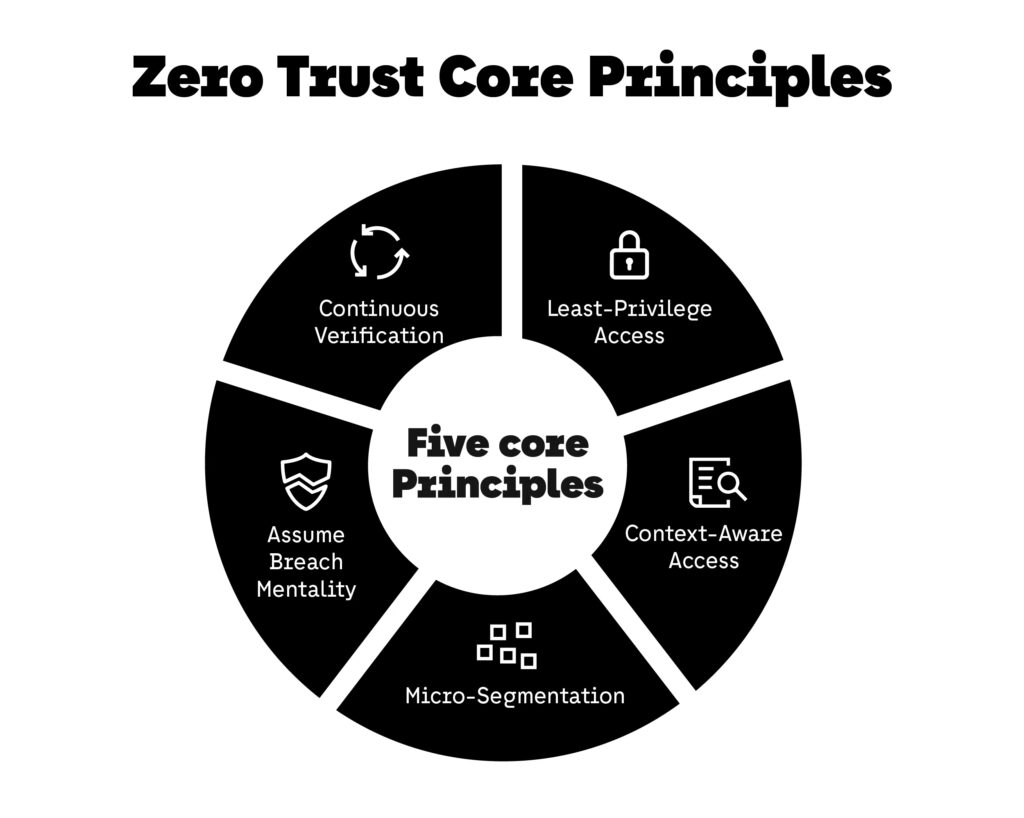
Organizations that approach Zero Trust as a product often struggle to achieve meaningful risk reduction. Partial implementations—such as enforcing stronger authentication without addressing access sprawl or third-party identities—create a false sense of security. This is why Zero Trust-related cybersecurity trends should be understood as strategic shifts rather than technology upgrades.
Why Partial Adoption Often Fails
Zero Trust initiatives frequently fail when applied inconsistently across systems and teams. Improving user authentication while leaving service accounts unmanaged, or securing internal users while ignoring partner access, preserves many of the same weaknesses attackers exploit. These gaps are especially problematic in environments with complex supply chains and automated workloads.
Successful adoption requires alignment across identity governance, access management, and policy enforcement. Without this alignment, organizations increase operational complexity without reducing exposure. This challenge explains why Zero Trust remains difficult to operationalize, even as it becomes a central theme in cybersecurity trends shaping enterprise security planning.
Software Supply Chain and Cloud-Native Risks
Why the Software Supply Chain Has Become a Primary Attack Vector
Modern software is assembled rather than built in isolation. Applications routinely depend on open-source libraries, third-party services, APIs, and managed platforms that are developed and maintained outside the organization. One of the most consequential cybersecurity trends emerging from this reality is the shift of risk from owned infrastructure to shared software ecosystems.
Attackers increasingly target these ecosystems because they offer scale. Compromising a widely used dependency or service can provide indirect access to hundreds or thousands of downstream organizations. This dynamic changes how risk propagates, making it harder for individual teams to assess exposure based solely on their own code or systems.
Open-Source Dependencies and Transitive Risk
Open-source software plays a critical role in modern development, but it also introduces transitive risk that is often poorly understood. Vulnerabilities may originate several layers deep in a dependency tree, well outside the direct visibility of development or security teams. When flaws are discovered, organizations may struggle to determine whether they are affected, where vulnerable components are used, and how quickly remediation is possible.
Recent guidance from the U.S. National Institute of Standards and Technology highlights the growing importance of software supply chain security and transparency, emphasizing practices such as software bills of materials and provenance tracking as foundational controls. These recommendations reflect broader cybersecurity trends in which understanding dependency relationships becomes as important as securing proprietary code.
CI/CD Pipelines as an Expanded Attack Surface
Continuous integration and deployment pipelines have dramatically improved delivery speed, but they also represent a high-value target. Build systems often hold privileged credentials, signing keys, and access to production environments. When compromised, they allow attackers to inject malicious code or modify artifacts before deployment, bypassing many downstream security controls.
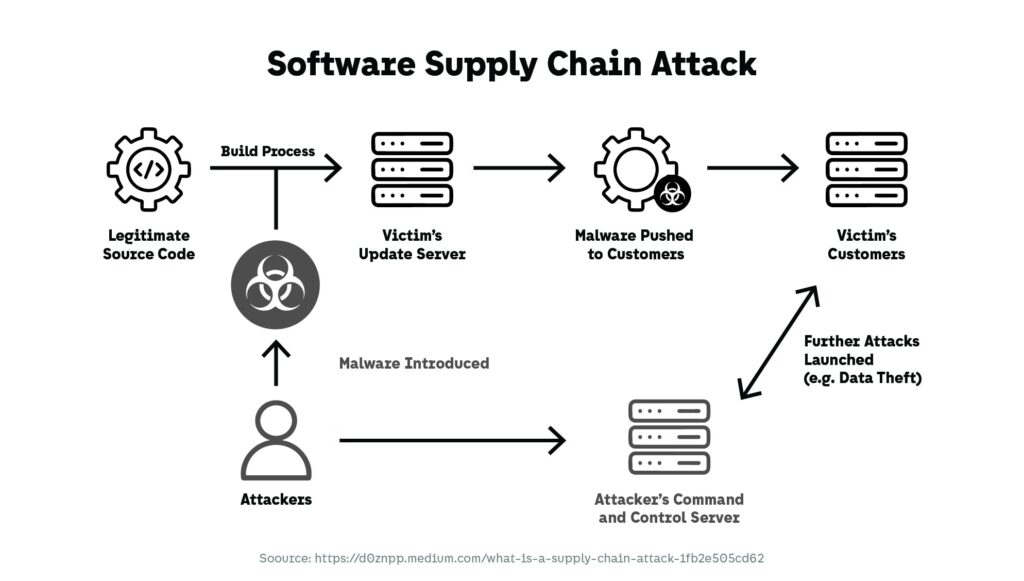
The risk here is structural rather than procedural. Pipelines are designed for automation and trust, not scrutiny. As environments become more automated, cybersecurity trends increasingly reflect the tension between speed and control, particularly wh en security ownership is fragmented across development, operations, and platform teams.
Cloud Misconfiguration and Shared Responsibility Gaps
Cloud-native environments introduce flexibility, but they also rely heavily on correct configuration and clear ownership. Misconfigured storage, overly permissive identities, and exposed management interfaces remain common causes of cloud-related incidents. These issues persist not because of a lack of tooling, but because responsibility is often diffuse.
In multi-cloud and hybrid environments, this complexity compounds. Differences in identity models, logging, and access controls make consistent governance difficult to maintain. These challenges illustrate how cybersecurity trends are increasingly shaped by organizational and architectural decisions rather than isolated technical failures.
From Isolated Failures to Systemic Risk
Taken together, supply chain exposure, pipeline trust, and cloud misconfiguration point to a common theme: risk is no longer confined to individual components. Instead, it emerges from how systems, services, and teams are connected. Incidents in these environments often appear sudden, but they are usually the result of latent weaknesses accumulating over time.
This perspective is essential for interpreting cybersecurity trends related to software and cloud-native systems. The most impactful failures are rarely caused by a single vulnerability; they arise from systemic conditions that allow small issues to cascade across interconnected environments.
DevSecOps and Security Ownership Shifts
Why Security Teams Can No Longer Scale Alone
As software delivery accelerates, the gap between security responsibility and security capacity continues to widen. One of the most persistent cybersecurity trends affecting modern organizations is the mismatch between how fast systems change and how slowly centralized security teams can respond. Traditional models assume security teams can review, approve, and monitor change, but that assumption breaks down in highly automated environments.
Development and platform teams now make decisions that directly affect risk on a daily basis. Infrastructure is provisioned through code, permissions are embedded in pipelines, and deployments occur continuously. In this context, treating security as a downstream checkpoint is no longer viable.
DevSecOps as an Operating Model, Not a Toolchain
DevSecOps is often misunderstood as a collection of tools bolted onto existing workflows. In reality, it represents a shift in how responsibility for risk is distributed across the organization. Rather than isolating security expertise within a single team, DevSecOps embeds security considerations into engineering, platform, and delivery processes.
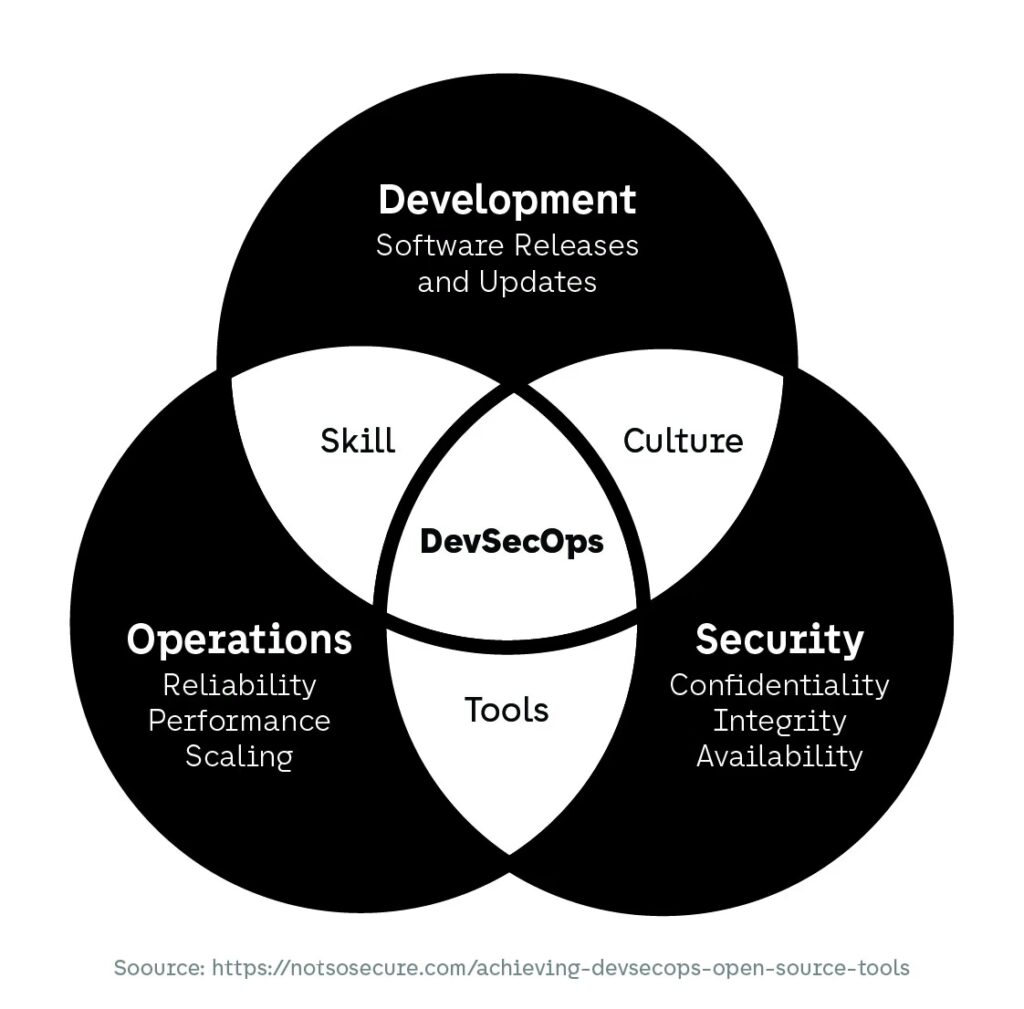
This shift aligns with broader cybersecurity trends that emphasize early risk identification and shared accountability. Security controls become part of how systems are designed and operated, not just how incidents are detected. External research published in 2024 by Google highlights how organizations adopting DevSecOps practices focus less on tooling and more on cultural alignment, automation standards, and ownership clarity.
Shifting Responsibility Without Diluting Accountability
A common failure mode in DevSecOps initiatives is the assumption that distributing responsibility means removing accountability. When security expectations are not clearly defined, teams may inherit risk without the authority or context to manage it effectively. This creates gaps rather than resilience.
Successful implementations balance shared responsibility with centralized governance. Security teams still define policy, standards, and risk tolerance, but enforcement is increasingly automated and distributed. FYLD has previously examined this balance in its analysis of DevSecOps adoption and its implications for agile teams. This model allows organizations to scale security practices without losing strategic oversight.
Cultural and Process Barriers to Adoption
The challenges associated with DevSecOps are often cultural rather than technical. Engineering teams may perceive security requirements as friction, while security teams may struggle to trust decentralized controls. Without alignment, automation alone cannot resolve these tensions.
These barriers explain why DevSecOps adoption remains uneven, despite its prominence in cybersecurity trends discussions. Organizations that succeed treat DevSecOps as a long-term organizational change, supported by leadership, incentives, and shared metrics rather than isolated initiatives.
Measuring Outcomes Instead of Activity
Another common pitfall is measuring success based on activity rather than outcomes. Metrics such as the number of scans performed or vulnerabilities detected provide limited insight into actual risk reduction. In mature DevSecOps environments, success is measured by factors such as reduced exposure windows, consistent policy enforcement, and improved recovery times.
This outcome-focused perspective reinforces a central theme across cybersecurity trends: resilience depends less on individual controls and more on how effectively organizations align people, processes, and systems around shared risk objectives.
What Organizations Must Prioritize in 2026
Moving from Tools to Strategic Focus
As organizations look ahead, the challenge is no longer identifying individual risks, but deciding where to focus limited attention and resources. One of the defining cybersecurity trends for 2026 is the growing gap between security activity and security impact. Many organizations deploy more controls than ever, yet still struggle to reduce meaningful exposure.
This disconnect reflects a broader need to shift from reactive investment toward strategic prioritization. Instead of asking which tools to buy next, leaders must ask which risks matter most and which capabilities genuinely reduce systemic vulnerability. Recent analysis from the World Economic Forum highlights that many organizations continue to overinvest in fragmented controls while underinvesting in governance, skills, and systemic risk reduction, reinforcing the need to interpret cybersecurity trends through a strategic rather than tool-centric lens.
Identity and Access as a Foundational Control
Across every major risk discussed so far, identity plays a central role. Compromised credentials, excessive permissions, unmanaged service accounts, and third-party access remain common failure points. As a result, strengthening identity and access management is no longer a tactical improvement but a strategic necessity.
Among current cybersecurity trends, identity-centric security stands out because it influences every layer of the environment—from cloud infrastructure and applications to supply chains and automated pipelines. Organizations that fail to establish consistent identity governance often find that other security investments deliver diminishing returns.
Visibility, Observability, and Context
Effective prioritization depends on visibility. Without reliable insight into how systems are accessed, how data flows, and how controls behave in practice, organizations are forced to operate on assumptions. This lack of context is a recurring theme across cybersecurity trends, particularly in highly distributed environments.
Modern security visibility is less about collecting more logs and more about understanding relationships: which identities access which resources, under what conditions, and with what level of risk. Observability enables earlier detection of abnormal behavior and supports faster, more confident decision-making when incidents occur.
Governance, Accountability, and Decision Rights
Technology alone cannot resolve ambiguity around ownership. Clear governance structures—defining who owns risk, who approves exceptions, and who is accountable for outcomes—are essential. Many security failures occur not because controls are absent, but because decision rights are unclear or misaligned.
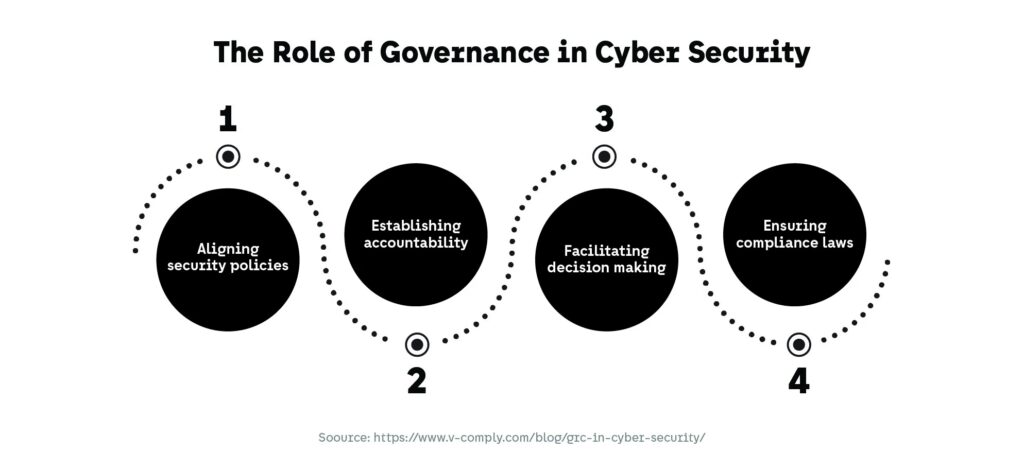
This challenge appears repeatedly across cybersecurity trends related to DevSecOps, cloud adoption, and third-party risk. Organizations that succeed establish governance models that scale with automation, ensuring that accountability remains intact even as execution becomes decentralized.
Organizational Readiness and Skills
Finally, prioritization must account for human capability. Security strategies that assume perfect execution or unlimited expertise are unlikely to succeed. Skills gaps, cognitive overload, and competing incentives all shape how controls perform in reality.
Preparing for future cybersecurity trends requires investment not only in technology, but in training, process maturity, and cross-functional collaboration. Organizations that align skills, incentives, and expectations are better positioned to translate strategy into sustained resilience.
When Security Transformation Fails
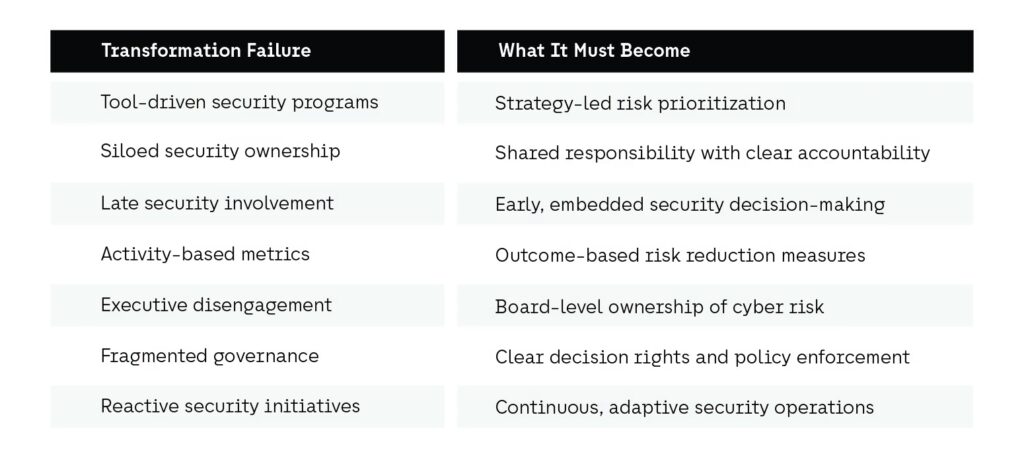
Over-Reliance on Tools Instead of Strategy
Many security transformation efforts begin with good intentions but falter when execution becomes tool-driven rather than strategy-led. One of the recurring cybersecurity trends observed across industries is the assumption that deploying new technologies automatically leads to better security outcomes. In practice, tools often amplify existing problems when underlying priorities, governance, and ownership are unclear.
Organizations may accumulate overlapping controls, dashboards, and alerts without addressing fundamental questions about risk tolerance or decision-making authority. This results in environments that are operationally complex but strategically fragile, where teams struggle to distinguish meaningful signals from noise.
Lack of Executive Alignment and Sponsorship
Security transformation rarely succeeds without sustained executive involvement. When cybersecurity is treated as a technical issue rather than a business risk, initiatives tend to stall or fragment. Leadership misalignment often leads to unclear priorities, inconsistent enforcement, and underinvestment in foundational capabilities.
Recent global analysis highlights that cyber risk is increasingly a leadership and governance challenge, with boards and senior executives expected to take a more active role as threats such as AI-driven attacks and software supply chain exposure continue to expand. This reinforces broader cybersecurity trends showing that governance and leadership matter as much as technical controls.
Poor Integration with Engineering and Platform Teams
Another common failure point is weak integration between security teams and the groups responsible for building and operating systems. When security requirements are introduced late or communicated poorly, they are often perceived as obstacles rather than enablers. This dynamic leads to workarounds, exceptions, and erosion of trust.
Security models that fail to account for engineering realities tend to degrade over time. As delivery pressure increases, controls are bypassed or inconsistently applied. This pattern appears repeatedly in cybersecurity trends related to DevSecOps adoption, where success depends less on tooling and more on collaboration and shared understanding.
Measuring Activity Instead of Outcomes
Metrics shape behavior, but many organizations track the wrong indicators. Counting vulnerabilities identified, scans performed, or controls deployed provides limited insight into actual risk reduction. These activity-based metrics can create a false sense of progress while masking persistent exposure.
More mature organizations focus on outcome-oriented measures, such as reduced exposure windows, improved detection-to-response times, and consistency of policy enforcement. Shifting measurement in this direction is difficult, but it is essential for interpreting cybersecurity trends accurately and avoiding superficial transformation efforts.
Why Failure Patterns Repeat
The most striking aspect of failed security transformations is how predictable they are. Despite differences in industry, technology, and threat profile, many organizations encounter the same obstacles: unclear ownership, fragmented priorities, and misaligned incentives. These failures are rarely caused by a lack of knowledge; they stem from structural and organizational blind spots.
Understanding these patterns is critical, because cybersecurity trends are shaped as much by organizational behavior as by attacker innovation. Recognizing why transformations fail is a prerequisite for designing strategies that endure.
Cybersecurity Trends as a Measure of Organizational Readiness
Cybersecurity trends are often discussed as external forces driven by attackers, technologies, or regulatory change. In reality, they are just as much a reflection of organizational readiness. The patterns examined throughout this article—from identity abuse and AI-driven attacks to supply chain exposure and governance failures—show that risk increasingly emerges from how systems are designed, operated, and managed.
What distinguishes resilient organizations is not their ability to predict every new threat, but their ability to adapt structurally. This includes treating identity as a foundational control, aligning security ownership with delivery speed, and ensuring that governance keeps pace with automation. Interpreting cybersecurity trends through this lens shifts the conversation away from short-term reactions and toward long-term capability building.
As security models evolve, the most effective strategies prioritize clarity over complexity. Clear decision rights, consistent accountability, and outcome-focused measurement matter more than the volume of tools deployed. Organizations that succeed recognize that cybersecurity trends signal where assumptions are breaking down, not which technologies are fashionable.
Looking ahead, resilience will depend on whether organizations can translate insight into sustained change. Cybersecurity trends will continue to evolve, but the underlying challenge remains constant: aligning people, processes, and systems around shared risk objectives. Those that address this challenge directly are better positioned to navigate uncertainty without overreacting to it.


