Why API Security in 2025 Is a Developer’s Frontline Responsibility
APIs have become the backbone of modern software ecosystems, powering everything from mobile apps and SaaS platforms to IoT devices and AI systems. But as companies accelerate digital integration, the attack surface has exploded—and so has the interest of attackers. In 2025, API security is no longer just a backend concern; it’s a core part of product integrity and user trust.
Recent incidents make the stakes painfully clear. In late 2023, T-Mobile disclosed a breach caused by an exposed API that led to the compromise of customer data. Earlier that same year, Optus, one of Australia’s largest telecom providers, suffered a major data leak linked to unauthenticated API access. These are not edge cases—they reflect a pattern of API security failures that continue to surface across industries.
That’s why API security in 2025 requires a proactive, developer-first mindset. It’s not just about tools or audits—it’s about building secure APIs by design, not patching vulnerabilities after a breach. This playbook lays out ten essential API security practices to help teams defend against modern threats, stay aligned with evolving standards like the OWASP API Top 10, and embed API security into their daily development workflow.
We’ll also suggest where these practices intersect with broader topics like DevSecOps, API observability, and platform architecture. For a deeper dive into infrastructure-level controls, see our overview on API gateways and secure-by-default patterns.
Let’s get into the core techniques every developer should follow in 2025.
1. Use Strong Authentication and Authorization for Every API Endpoint
Modern APIs often serve as the gateway to critical business logic, databases, and user data. Yet, in 2025, many API security breaches still stem from one root cause: developers treating authentication as a frontend responsibility and authorization as a backend afterthought.
To protect APIs against increasingly automated and targeted attacks, every endpoint must enforce strong authentication and context-aware authorization—no exceptions.
Why It Matters
APIs are inherently exposed to the internet and often serve sensitive operations. Weak authentication allows attackers to impersonate users, while weak authorization allows them to perform actions or access data they shouldn’t.
The OWASP API Security Top 10 (2023 edition) highlights Broken Object Level Authorization (BOLA) and Broken Function Level Authorization (BFLA) as the two most exploited categories in real-world attacks.
A Cloudflare API Security Trends Report (2023) found that over half of surveyed enterprises experienced an API-related incident in the past 12 months, with authorization gaps being the primary cause.
What Developers Should Implement in 2025
1. Authentication
- OAuth 2.1 + OpenID Connect: Always validate tokens server-side. OAuth 2.1 formalizes secure practices by removing outdated flows and enforcing PKCE.
- Mutual TLS (mTLS): Strongly recommended for internal service communication.
- API keys ≠ authentication: Use them only for quota enforcement or billing—not access control. Know more about the difference between API keys and authentication here.
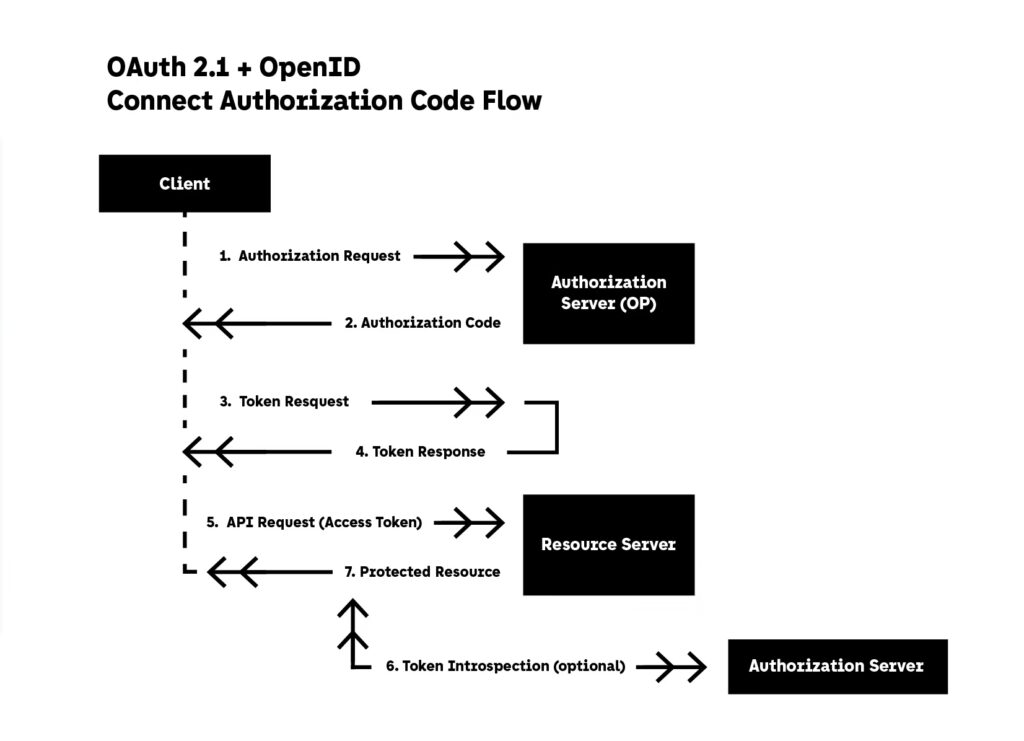
2. Authorization
- RBAC: Enforce role-specific permissions at each route or controller level.
- ABAC: Evaluate context (location, device, IP) alongside roles.
- JWT: Use signed, time-limited tokens with granular scopes (invoice:read, not read_all).
The NIST publication 800-162 outlines recommended models for combining RBAC and ABAC in enterprise-grade systems.
Real-World Example
In T-Mobile’s January 2023 API breach, attackers accessed 37 million customer records through an unauthenticated or improperly scoped API. T-Mobile filed an official breach disclosure with the SEC.
Also in 2023, Toyota Connected leaked internal vehicle data due to hardcoded API credentials and overly broad access permissions. Click here and know more about this leak.
These cases underscore why API security in 2025 must shift left—security should be enforced at design time, not after a breach.
Best Practice in Action
- A mobile app uses OAuth2 with PKCE to request scoped tokens
- A backend API validates JWTs, checking scopes and session validity
- Internal services use mTLS for mutual identity verification across a service mesh
- An API gateway handles rate limiting, header validation, and token inspection before routing requests
Tradeoffs
- JWTs are stateless but hard to revoke; short TTLs and refresh tokens are mandatory
- RBAC is simple but rigid; ABAC adds complexity but supports dynamic rules
- mTLS adds overhead in certificate management but drastically reduces spoofing risk
2. Implement Rate Limiting and Throttling to Prevent Abuse
Even the most secure authentication system can be bypassed or overloaded if your API accepts unlimited traffic. In 2025, rate limiting and throttling are not optional—they’re baseline defenses against abuse, brute-force attacks, and accidental overuse.
Why It Matters
APIs without traffic control are vulnerable to:
- Credential stuffing (automated login attempts)
- Denial-of-Service (DoS) attacks
- Data scraping and exfiltration
- Cost spikes on pay-per-use infrastructure
Attackers frequently probe APIs to detect behavioral patterns, pricing logic, or authentication weaknesses. Without built-in request controls, even valid credentials can be abused to overwhelm your system.
According to The State of API Security in 2024 by Imperva, business logic abuse accounted for 27% of all API attacks in 2023, highlighting how attackers increasingly target application design rather than traditional vulnerabilities.
What Developers Should Implement in 2025
1. IP-Based Rate Limiting
Set hard limits on requests per IP per minute. This works well for public APIs with anonymous traffic or token-less endpoints (like pricing pages or public catalogs).
- Example: 60 requests per IP per minute (burst) with a 10-minute rolling window.
2. Authenticated User Throttling
Apply stricter, user-specific rate limits to authenticated API consumers—particularly for endpoints like /login, /reset-password, /checkout, and /graphql.
- Example: 10 POST requests to /auth/token per hour, per user ID.
3. Behavior-Aware Quotas
For paid plans or B2B customers, use dynamic quotas based on request type or cost units.
- Example: 5000 requests/day for Free tier, 100,000 for Enterprise, enforced via API key metadata.
The Cloudflare API Gateway documentation (updated in 2024) explains how to apply rate limiting at multiple levels, including IP, user, and origin.
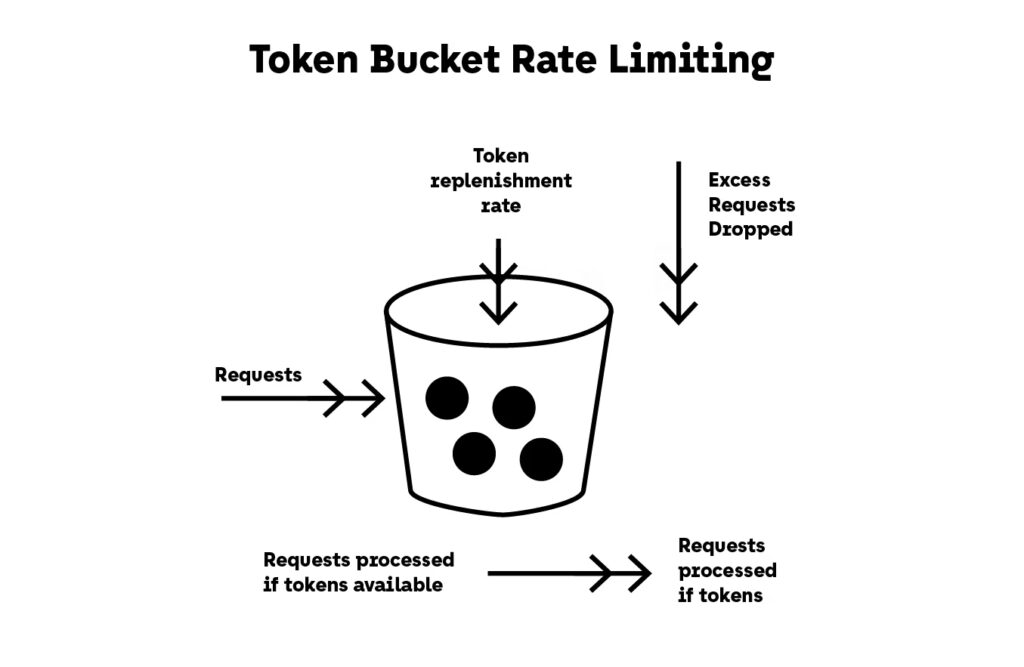
4. Token Bucket and Leaky Bucket Algorithms
Use proven algorithms to manage bursts and steady traffic flows. Many API gateways (e.g., Kong, Apigee, Envoy) support this natively.
- Token Bucket allows short bursts
- Leaky Bucket smooths traffic over time
For deeper algorithm references, the AWS API Gateway documentation includes updated guidance on implementing throttling logic.
Real-World Example
In 2023, Shopify engineers published a detailed breakdown of how they scaled their API traffic controls across millions of merchants. They implemented rate limits per store, per endpoint, and by API scope to ensure fair usage and prevent scraping.
Additionally, GitHub’s API rate limiting policy, updated in late 2023, now adjusts dynamically based on token scopes and endpoint sensitivity—reducing abuse while supporting high-usage workflows.
Best Practice in Action
- Apply default global limits at the API gateway level to support baseline API security controls
- Customize limits by endpoint, method, and user type
- Return 429 Too Many Requests with Retry-After headers for transparency
- Log and alert on abnormal spikes or throttling violations
Tradeoffs
- Aggressive limits may block legitimate high-traffic users
- Requires testing to avoid breaking client integrations
- Throttling logic must scale horizontally in distributed systems to maintain performance without compromising API security
3. Validate All Input — and Never Trust Client Data
Whether it comes from a browser, mobile app, IoT device, or third-party integration, API input is always a potential attack vector. In 2025, with APIs serving more channels than ever before, input validation is a core API security layer—not just a coding hygiene step.
Why It Matters
Failing to validate or sanitize input can lead to:
- Injection attacks (SQL, NoSQL, Command, or LDAP)
- Mass assignment vulnerabilities
- Unexpected behavior in downstream systems
- Authentication bypass or privilege escalation
In APIs, input is especially dangerous when it’s JSON-based—developers often assume well-formed payloads, but attackers routinely craft malicious structures or unexpected types to manipulate logic.
The OWASP API Security Top 10 (2023) ranks Improper Input Validation at position #4, highlighting its prevalence across REST and GraphQL APIs.
What Developers Should Implement in 2025
1. Schema Validation on All Payloads
Use strict JSON schema validation libraries to reject requests that are malformed, missing required fields, or contain unexpected types—an essential step for enforcing API security at the input layer.
- Node.js: ajv
- Python: pydantic
- Java: javax.validation or Spring Boot @Valid
Include enum constraints, required fields, and pattern matching in your schemas. Reject extra fields unless explicitly whitelisted.
2. Mass Assignment Protection
Never bind incoming JSON objects directly to model instances (e.g., user.update(req.body)). Use whitelists to control which fields can be updated.
- In Ruby on Rails, use strong_parameters
- In Express.js, sanitize req.body manually or with a DTO mapping layer
3. Sanitize Input for Injection Prevention
For all user-controlled input:
- Escape or parameterize values in database queries
- Reject input with unexpected structure (e.g., array instead of string)
- Normalize and sanitize any content stored or rendered
The PortSwigger Web Security blog published a 2023 breakdown of modern NoSQL injection examples in MongoDB and Firebase, showing how simple JSON manipulation can bypass auth.
4. Use OpenAPI or AsyncAPI Specifications
Define request and response structures clearly—and enforce them with tooling like Swagger, Spectral, or Stoplight.
GitHub’s public GraphQL API is a good reference for strict schema enforcement and version negotiation.
Real-World Example
In 2023, Lazada, a large e-commerce platform in Southeast Asia, suffered a partial account takeover vulnerability due to improper validation of input sent to its API password reset flow. Researchers demonstrated that sending a null email value and modifying request timing allowed privilege escalation—highlighting a common API security failure rooted in weak input validation.
In another case, researchers uncovered that many mobile banking apps failed to validate input on the backend, relying only on mobile-side checks. These were easily bypassed by sending modified requests via tools like Burp Suite, further exposing gaps in API security architecture.
Best Practice in Action
- Enforce schema validation at the API gateway or controller level
- Strip unknown fields and reject unexpected types
- Implement logic-layer guards to ensure business rule compliance
- Monitor logs for parsing errors and rejected payloads
Tradeoffs
- Strict schemas can block poorly implemented clients (versioning helps)
- Some frameworks require custom middlewares for full schema enforcement
- Validation adds processing time, but prevents far greater API security risks
4. Encrypt Sensitive Data in Transit and at Rest
Encryption is not just a compliance checkbox—it’s a foundational defense. In 2025, as APIs increasingly exchange personal, financial, and health-related data, encryption is a mandatory pillar of API security, critical to maintaining confidentiality, integrity, and trust.
Why It Matters
Without proper encryption, APIs are vulnerable to:
- Man-in-the-middle (MITM) attacks
- Credential theft via packet sniffing or proxy compromise
- Plaintext data exposure in logs, backups, or databases
- Regulatory violations (e.g., GDPR, HIPAA, PCI DSS)
A study by IBM X-Force in 2023 reported that 45% of API-based incidents involved unencrypted sensitive data—either over the wire or stored without encryption-at-rest.
What Developers Should Implement in 2025
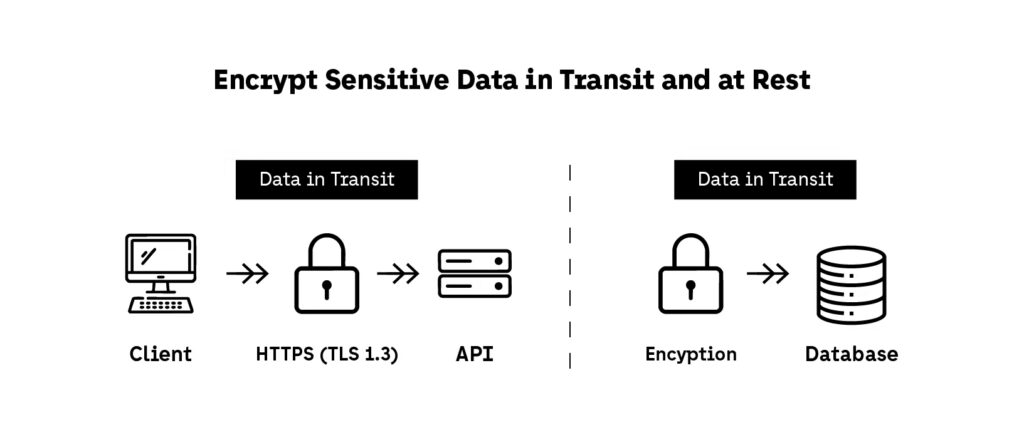
1. HTTPS with TLS 1.3 for All API Traffic
- Enforce HTTPS by default with TLS 1.3
- Reject deprecated protocols like TLS 1.0/1.1
- Use HSTS headers and ensure strong forward secrecy (e.g., ECDHE)
Let’s Encrypt offers free TLS certificates with automated renewal.
2. Encrypt Data at Rest Using Proven Libraries
- Apply AES-256 or ChaCha20 encryption
- Use envelope encryption with a key management system (KMS)
- Avoid homegrown cryptography or outdated algorithms
OWASP’s updated Cryptographic Storage Cheat Sheet (2023) outlines strong patterns.
3. Mask and Minimize Data Exposure
- Truncate or redact sensitive fields like account numbers or tokens
- Remove secrets from logs before ingestion
- Tokenize or pseudonymize identifiable values (especially under GDPR)
ENISA’s 2022 Data Protection Engineering Report underlines that anonymisation, pseudonymisation, and other PETs should be used to limit data exposure — even when encryption is in place — to achieve effective data minimization principles under GDPR.
4. Use JSON Web Encryption (JWE) for Extra-Sensitive Payloads
JWE protects data even if HTTPS is compromised—particularly important for industries like finance and healthcare.
Verified Real-World Example
In 2023, SecurityTrails researchers discovered that several public GraphQL APIs—across retail and social platforms—leaked sensitive user data via introspection endpoints and verbose logs. These APIs revealed phone numbers, addresses, and tokens in plaintext.
Also in 2023, the Toyota Connected API breach exposed internal vehicle telemetry data due to hardcoded credentials and poorly configured endpoints. Data could be accessed in plaintext from improperly secured APIs.
Best Practice in Action
- All API traffic forced through HTTPS (TLS 1.3)
- Fields encrypted at rest using KMS-backed envelope encryption
- Secrets and tokens removed from logs by default
- Role-based access control enforced before decrypting payloads
Tradeoffs
- Encryption adds processing latency and operational complexity, but remains essential for API security
- Key management must be secured separately (a new attack surface)
- Debugging and telemetry require special handling for encrypted fields
5. Monitor and Log API Activity with Context
You can’t protect what you don’t see. In 2025, modern APIs must be continuously observed—not just for uptime, but for security signals like anomalous behavior, abuse patterns, or misuse of credentials.
Real-time visibility into API usage is critical for both breach detection and post-incident forensics. Without contextual logs and structured monitoring, threats go undetected until it’s too late.
Why It Matters
APIs are high-throughput, data-rich, and exposed—making them prime targets for API security threats. And yet, many teams still:
- Don’t log failed auth attempts
- Miss traffic anomalies (e.g., one user hitting 100 endpoints per second)
- Lack structured logs with user and token context
- Can’t correlate activity across services
According to Salt Security’s State of API Security Report 2022, 62% of organizations lacked adequate visibility into their APIs—leading to abuse that often went undetected for extended periods. This lack of observability remains one of the most common weaknesses in modern API security.
What Developers Should Implement in 2025
1. Centralized, Structured Logging
- Use JSON-formatted logs with metadata: user ID, request ID, endpoint, auth method, latency — critical for maintaining API security visibility
- Include geo-IP, token scope, and device info where possible
- Avoid dumping full request bodies—log fields selectively
Logging pipelines should aggregate to platforms like OpenSearch, Datadog, Loki, or ELK. Add alerting layers for key risk indicators.
2. Real-Time Monitoring and Anomaly Detection
Use API-aware platforms or build custom alerts around:
- Unusual spikes in traffic
- High volume of 401 or 403 responses
- Token re-use or expired token access
- Access patterns outside normal hours or geographies
By embedding these practices, teams strengthen API security through both proactive detection and actionable visibility, reducing time to respond and the likelihood of silent failure.
The Cloudflare API Gateway (2024 version) includes anomaly detection at the edge, flagging token abuse and pattern shifts.
3. Trace Correlation and Distributed Context
Adopt tracing tools like OpenTelemetry or Jaeger to track requests across services. Correlate API calls with downstream effects in DBs, queues, or storage layers.
GitHub’s engineering team detailed how they use OpenTelemetry with GraphQL to trace API behavior by org, scope, and region.
4. Audit Logs for Security and Compliance
Retain long-term, tamper-proof logs of key actions:
- Auth events
- Permission changes
- Data access (especially for PII or financial data)
For financial or healthcare applications, logs must support audit trails under regulations like PCI DSS, HIPAA, and GDPR.
The AWS Security Audit Logging Best Practices Guide (2023) gives strong patterns for secure, compliant API logging.
Real-World Example
In early 2023, Peloton suffered an exposure where its API returned detailed user profile data without proper authorization. Logs and monitoring were not in place to catch repeated scraping, and the issue was disclosed by a security researcher.
Best Practice in Action
- API Gateway enforces logging of all incoming requests to support API security monitoring
- Logs include token type, user ID, IP, latency, and location
- Anomaly detection flags login abuse and access pattern shifts
- Alerting pushes security events into SIEM or Slack channels
Tradeoffs
- Over-logging can inflate costs and make root-cause harder to trace
- Token data must be anonymized or masked for privacy and API security compliance
- Distributed tracing adds operational overhead but unlocks visibility critical for securing APIs at scale
6. Use API Gateways to Enforce Security Policies
In 2025, API gateways are more than just reverse proxies. They are critical enforcement points for authentication, rate limiting, validation, observability, and traffic shaping. Without them, API security logic ends up duplicated—or worse, skipped entirely—across services.
A well-configured API gateway reduces developer overhead while ensuring consistency across APIs—public or internal.
Why It Matters
APIs grow quickly, and without a centralized enforcement layer, they become inconsistent and vulnerable. Common risks addressed by gateways include:
- Inconsistent authentication
- Missing rate limits
- Lack of input validation or schema enforcement
- Unsafe exposure of internal routes
According to Gartner’s 2023 API Security Market Guide, 85% of successful API attacks exploited gaps in enforcement rather than logic flaws. Gateways reduce that attack surface by standardizing traffic entry points.
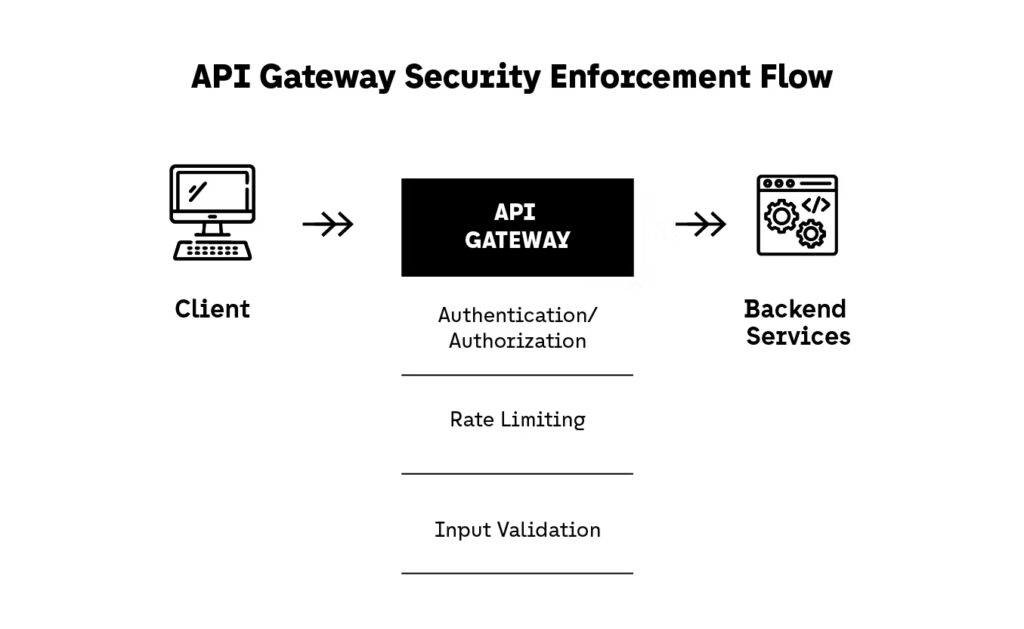
What Developers Should Implement in 2025
1. Authentication and Authorization Offload
Use the gateway to:
- Validate JWTs and token scopes before reaching the app
- Enforce OAuth2 client credentials or API keys
- Strip or inject headers to normalize identity data (e.g., x-user-id, x-org-id)
Example: Kong, Apigee, or Envoy with built-in JWT plugins.
2. Rate Limiting and Throttling at the Edge
Apply IP-, user-, and method-based rate limits before requests hit backend services. This prevents abuse and preserves infrastructure.
See the AWS API Gateway throttling guide (2024 update) for practical limits and configurations.
3. Input Validation and Schema Enforcement
Integrate with OpenAPI specs to reject invalid requests at the gateway:
- Validate request size, shape, method, headers
- Enforce content types and required parameters
- Block malformed JSON or unsupported encodings
The Kong Gateway Plugin Hub provides schema validation plugins for REST and GraphQL as of their 2023 release.
4. Route Control and Microservice Security
Gateways can:
- Hide internal services
- Enforce mTLS between edge and cluster
- Version APIs cleanly (e.g., /v1, /v2)
- Prevent direct access to business-critical endpoints
According to Cloudflare’s API Gateway architecture whitepaper (2024), service segmentation is one of the top three use cases for secure gateway deployment.
Real-World Example
Stripe’s public API architecture relies heavily on gateway-level enforcement. They validate JWTs, limit request size, reject invalid input formats, and shape traffic before any service logic is invoked—demonstrating a mature, scalable approach to API security. This model has been widely referenced in modern API gateway case studies.
In a 2023 incident reported by researchers at Wallarm, an exposed admin route in a fintech API was publicly accessible due to lack of API gateway controls. The system assumed all clients came from a trusted network—an assumption that failed under load testing.
Best Practice in Action
- API gateway terminates TLS, validates tokens, enforces quotas to support consistent API security policies
- Malformed requests are rejected before app logic runs
- Sensitive routes are blocked from public access
- Traffic is monitored and logged at the edge
Tradeoffs
- Improperly configured gateways can still leak sensitive routes and introduce API security gaps
- Requires team expertise in traffic routing and observability
- Adds latency, but often improves reliability and debuggability
7. Apply the Principle of Least Privilege to Data and Operations
In 2025, API security isn’t just about who can access an API—it’s about what they can access and do once authenticated. The principle of least privilege (PoLP) ensures that users, systems, and services only have the minimum permissions needed to perform their role.
This limits damage from compromised credentials, abused tokens, or misconfigured integrations.
Why It Matters
Excessive permissions are one of the top causes of overexposure in production APIs. This includes:
- Broad admin access for standard users
- APIs returning full records when partial would suffice
- Insecure defaults in access tokens and API keys
- Frontends revealing more data than needed for the current view
According to the Google Cloud Security Whitepaper, implementing least privilege and proper access controls is essential to reduce the attack surface and prevent API abuse in enterprise environments.
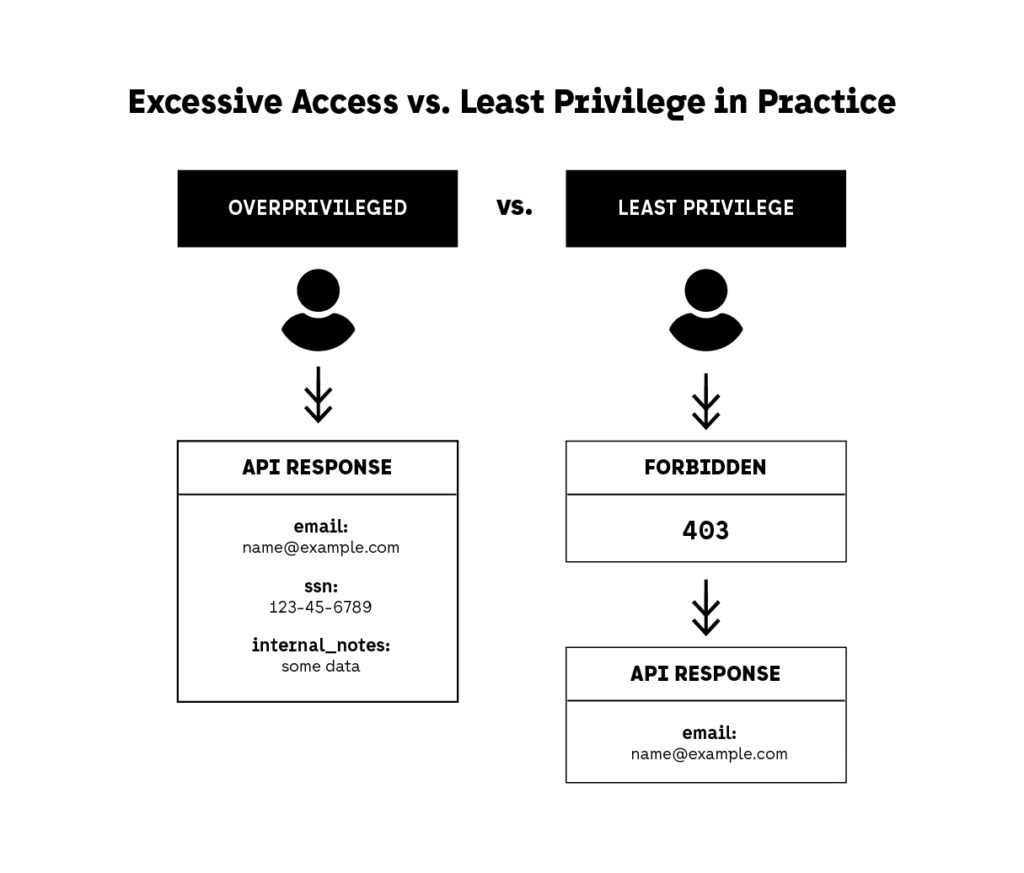
What Developers Should Implement in 2025
1. Granular Permissions at the Endpoint Level
- Separate read vs write routes (e.g., GET /users/me vs POST /users/update)
- Use route-level auth middleware that checks token scopes or permissions to enforce API security boundaries
- Prevent privilege escalation by checking the subject of a request matches the authenticated user
2. Fine-Grained Scopes in Access Tokens
- Avoid global scopes like read_all or admin unless absolutely required
- Use business-aligned scopes like project:read, payment:refund, invoice:approve
- Enforce scope validation in middleware or at the API gateway
Auth0’s 2023 blog post explains how to implement scope-based authorization with JWTs and middleware in Node.js, Python, and Go.
3. Data Minimization by Role or Context
- Only return fields needed for the requestor’s role to reduce API security exposure
- Mask sensitive fields for non-admin users (e.g., partial account numbers)
- Don’t return nested related entities unless explicitly requested
Stripe and GitHub both use “expandable fields” in their APIs to control overfetching. This design pattern limits exposure by default.
4. Rotate and Expire Access Credentials
- Rotate API keys and tokens regularly
- Set short-lived access for temporary credentials (contractors, test apps)
- Revoke unused tokens automatically
The CNCF Security Technical Advisory Group (TAG Security) released a 2023 paper on credential rotation policies in microservices environments.
Real-World Example
In 2023, a misconfigured AWS Lambda API allowed any user with a basic auth token to trigger administrative actions, such as deleting user records and modifying IAM roles. The issue stemmed from a single endpoint that bypassed scope validation and relied solely on method-based checks. The case was disclosed by researchers at Mitiga.
Best Practice in Action
- JWT scopes are mapped to roles in the API middleware
- API responses are trimmed to match the caller’s privilege
- Admin routes are separated and require distinct tokens
- Credential usage is logged and rotated every 30–90 days
Tradeoffs
- Granular access control increases code complexity
- Requires clear mapping between roles, scopes, and data
- Can break apps if scopes or field access are too restrictive during refactoring
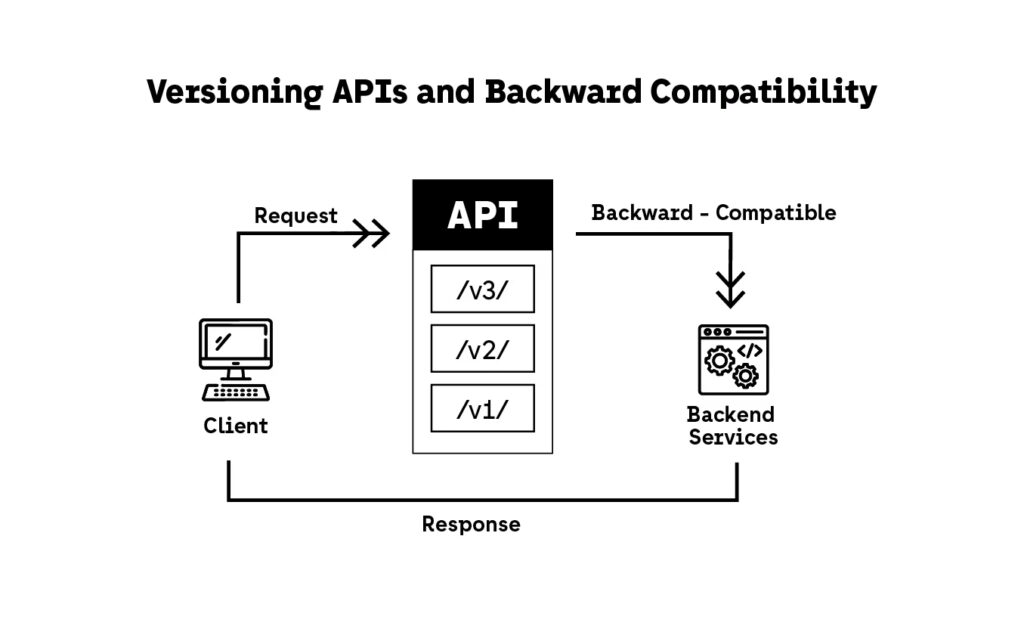
8. Keep APIs Versioned and Backward-Compatible for Security Evolution
In API security, stability is not the same as safety. As threats evolve, you need to roll out breaking changes—rate limits, stricter validation, or auth model shifts—without disrupting users. That’s why versioning is essential for maintaining secure and flexible APIs in 2025.
Without proper versioning, any API security improvement risks breaking dependent clients or exposing legacy behavior that attackers can exploit.
Why It Matters
Many API breaches happen because legacy endpoints are:
- No longer actively maintained
- Exempt from new security checks
- Lacking modern validation or auth requirements
- Still exposed in production
According to the Postman State of the API Report (2023), 40% of API-producing teams maintain two or more versions in production. Yet, fewer than half of them regularly audit those versions for security regressions.
What Developers Should Implement in 2025
1. Version in the URL or Header
Common approaches:
- URI path: api/v1/resource
- Custom header: X-API-Version: 2
- Content negotiation: Accept: application/vnd.company.v1+json
Avoid query param versioning (?version=1)—it’s harder to cache and secure.
The Microsoft REST API Guidelines recommend path-based versioning for clarity and maintainability.
2. Deprecate Old Versions Gracefully
- Announce deprecations clearly in response headers (e.g., Deprecation: true)
- Use sunset policies: include a Sunset header with a date
- Provide clients with upgrade guides and changelogs
Stripe’s API changelog model is a best-in-class example of managing security and behavior shifts transparently.
3. Evolve Security Policies Between Versions
- Add rate limits, stricter scopes, or validation in v2+
- Drop deprecated headers or token formats
- Require stricter TLS versions or auth flows
GitHub began enforcing stricter OAuth2 scopes and rejecting deprecated authentication patterns in their v3 API, documented extensively in their changelog.
4. Audit and Monitor Legacy Versions
- Log traffic by version
- Alert on usage of deprecated routes
- Flag older clients bypassing security middleware or using unvalidated payloads
The OWASP API Security Top 10 (2023) lists “Unsafe Consumption of APIs” (API10:2023) as a key risk—particularly when older API versions consume external or outdated services.
Real-World Example
In a 2023 case documented by the Noname Security research team, a payment gateway kept an outdated v1 of its API online for mobile clients. It lacked updated rate limits and returned more data than necessary. Attackers targeted that version, bypassing newer protections in v2 and v3.
Best Practice in Action
- Each API version has its own schema, docs, and release notes
- Older versions are monitored and gradually deprecated
- New versions enforce updated auth, rate limits, and schemas
- Changelogs document security improvements and breaking changes
Tradeoffs
- Managing multiple versions adds maintenance overhead
- Requires strong CI/CD testing to avoid regressions
- Version drift can lead to inconsistent behavior across environments
9. Test APIs for Security Continuously — Not Just in Staging
In 2025, API gateways are more than just reverse proxies. They are critical enforcement points for authentication, rate limiting, validation, observability, and traffic shaping. Without them, API security logic ends up duplicated (or skipped) across services.
A well-configured API gateway reduces developer overhead while ensuring consistency across APIs—public or internal. It also helps enforce security policies uniformly across environments, especially when integrated into CI/CD pipelines, where configuration drift and inconsistent controls are common risks.
Why It Matters
APIs grow quickly, and without a centralized enforcement layer, they become inconsistent and vulnerable. API gateways reduce these risks by providing a dedicated layer for managing API security policies like input validation, token verification, and exposure control—keeping protections aligned with infrastructure scale.
Common risks addressed by gateways include:
- Inconsistent authentication
- Missing rate limits
- Lack of input validation or schema enforcement
- Unsafe exposure of internal routes
Traditional pen tests or quarterly scans aren’t enough. Real-world attackers automate and adapt—your testing strategy should do the same.
According to the Forrester Wave on API Security (2023), 63% of enterprises experienced API incidents despite having passed functional tests—because security edge cases weren’t covered.
What Developers Should Implement in 2025
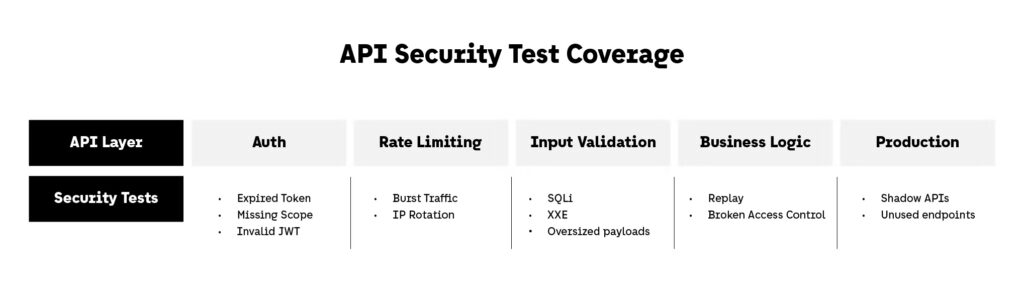
1. Automated API Security Scanning in CI/CD
Tools like:
- StackHawk (built for CI pipelines)
- 42Crunch (OpenAPI security linting + runtime testing)
- ZAP CLI (for custom OWASP ZAP scans in pipelines)
Include tests for:
- Unauthenticated access
- Rate limit bypass
- Injection vectors
- Broken authorization paths
StackHawk’s integration guide for GitHub Actions and GitLab CI/CD (updated 2023) provides implementation examples.
2. Contract and Schema Testing
Use OpenAPI or GraphQL schemas to test against:
- Undocumented fields or routes
- Data type mismatches
- Unexpected nested objects
Tools like Spectral and Dredd help ensure your APIs conform to specifications and flag potentially risky changes automatically. Spectral is an open-source JSON/YAML linter that enables teams to define and enforce style guides, detect errors, and improve consistency across OpenAPI and AsyncAPI definitions.
3. Negative and Abuse Case Testing
Write tests for:
- Invalid tokens and expired sessions
- Overly long or malformed payloads
- Unexpected HTTP verbs
- Missing or reordered parameters
These are common bypass paths for APIs that only test “happy path” logic.
The APIsec University (2023) curriculum explains how to write API-specific abuse tests and includes test data strategies.
4. Runtime Testing and Shadow API Detection
Use passive scanners and runtime agents to:
- Detect undocumented or deprecated endpoints
- Flag unexpected payloads or auth behaviors
- Catch test credentials in production traffic
The Noname Security API Discovery Guide (2023) explains how to detect shadow APIs and map undocumented attack surfaces.
Real-World Example
In 2023, a vulnerability disclosed by Checkmarx researchers showed how an e-commerce API had a “forgot password” endpoint with no rate limiting or response tampering checks. Although the functionality passed staging tests, runtime testing revealed the logic flaw during simulated credential stuffing.
Another case: a fintech API had old v1/transactions routes accessible without tokens. These were not scanned because the OpenAPI spec only included v3. They were discovered during runtime traffic inspection with automated discovery tooling.
Best Practice in Action
- API scanning is run in every pull request
- Schema linting blocks merges if spec is out of sync
- Production agents monitor for unknown endpoints
- Security tests include real-world abuse and invalid inputs
Tradeoffs
- Can slow down builds if scans aren’t optimized
- False positives must be triaged regularly
- Requires collaboration between security and QA/dev teams
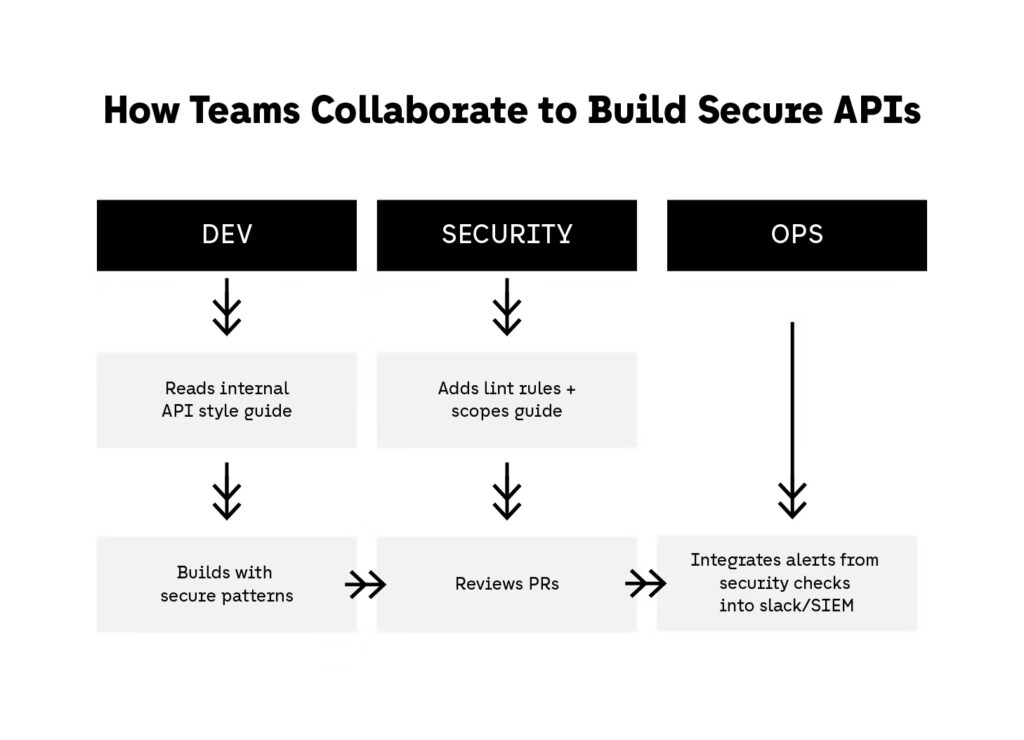
10. Document and Educate: API Security Is a Team Responsibility
Tools and gateways aren’t enough if your team doesn’t understand how and why to build secure APIs. In 2025, developer awareness is the frontline of API defense—especially with the rise of low-code tools, distributed teams, and fast iteration cycles.
Well-documented security practices help scale secure development across teams, geographies, and tech stacks.
Why It Matters
Security issues often stem from:
- Inconsistent implementation between teams
- Missing documentation for auth, scopes, or headers
- Developers bypassing protections to “unblock” progress
- Lack of onboarding around secure patterns
A 2023 report by Snyk and the Linux Foundation found that 59% of organizations had no internal API security guidelines, and 72% of developers had never received security-focused API training.
What Developers Should Implement in 2025
1. Document Auth Flows, Scope Models, and Headers
- Explain how tokens work (e.g., JWT fields, expiration)
- Clarify required scopes and headers per endpoint
- Include real examples for each auth scenario
Use tools like Stoplight, Redoc, or Swagger UI to visualize security expectations in the docs.
GitHub’s REST API docs set a high bar by embedding scope details directly into each endpoint reference.
2. Maintain a API Security Style Guide
Include guidance on:
- Naming sensitive endpoints
- HTTP verb usage (e.g., don’t use GET for destructive actions)
- Rate limit and auth enforcement tags
- How to write safe OpenAPI schemas
Shopify’s internal style guide (referenced in their 2023 engineering blog) includes security tagging as part of their API design review checklist.
3. Educate Through Playbooks and Postmortems
- Publish internal incident write-ups to promote learning
- Use blameless postmortems to share root causes and fixes
- Keep a secure development playbook available for all teams
Netflix’s Security Engineering team open-sourced its threat modeling playbook in 2023 to help drive team-wide awareness.
4. Promote a “Security by Default” Culture
Encourage developers to:
- Log security concerns, not just bugs
- Ask for reviews on security-critical PRs
- Use linter rules or CI gates for secure patterns
- Flag unsafe shortcuts in early design phases
The OWASP Developer Guide (2023) emphasizes team education as a central control in software security.
Real-World Example
In September 2023, Auth0 reported that a misconfigured authorization rule in a customer identity API allowed users to access other tenants’ data. The issue stemmed from missing tenant-scoped validation in a shared endpoint. This was detailed in their official security bulletin.
Best Practice in Action
- Every API has a security reference section in its docs
- Dev teams use shared style guides with API security defaults
- New engineers are trained in secure request/response design with API security in mind
- Postmortems are archived and searchable for all staff
Tradeoffs
- Requires documentation ownership and process discipline
- Needs developer buy-in to become effective
- May surface friction during fast-paced delivery cycles
API Security in 2025 Is Continuous, Collaborative, and Non-Negotiable
APIs are no longer secondary interfaces—they are the primary way software communicates, scales, and delivers value. And in 2025, they’ve also become one of the most targeted and exposed surfaces in modern architectures, making API security a top engineering priority.
The best way to stay ahead isn’t to patch vulnerabilities after a breach—it’s to build API security into your architecture from the ground up. That means enforcing authentication consistently, minimizing access scope, validating all input, monitoring usage patterns, and embedding a culture of security across every stage of development.
At Fyld, we’ve seen firsthand how critical it is to treat API security as a shared engineering responsibility—not just a security team concern. Whether you’re launching a new product or evolving a legacy system, adopting these ten best practices helps reduce risk, increase system resilience, and protect user trust from day one.
Security isn’t a checkbox. It’s a commitment to long-term product integrity—and it starts at the code level.


